Configuring a VPN tunnel
SSL or IPsec IKEv2 VPN
SN VPN Client Exclusive allows you to create and configure several types of VPN tunnels.
It also allows you to open them simultaneously.
SN VPN Client Exclusive allows you to configure the following types of tunnels:
-
IPsec IKEv2
-
SSL
The procedure used to create a new VPN tunnel is described in the previous sections: Configuration Wizard and VPN configuration tree > Contextual menus.
TIP
We recommend configuring IKEv2 tunnels with a certificate. Refer to chapter Security recommendations.
Editing and saving a VPN configuration
SN VPN Client Exclusive allows you to modify the VPN tunnels and test these modifications “on-the-fly” without saving the VPN configuration.
All unsaved changes in the VPN configuration are clearly shown in the tree, as the name of modified items appears in bold.
The VPN configuration can be saved at any time using either of the following:
-
Ctrl+S shortcut
-
Configuration > Save menu item
A warning will be displayed if a VPN configuration has been changed and the user tries to quit the software without saving.
Configuring an IPsec IKEv2 tunnel
IKE Auth: Authentication
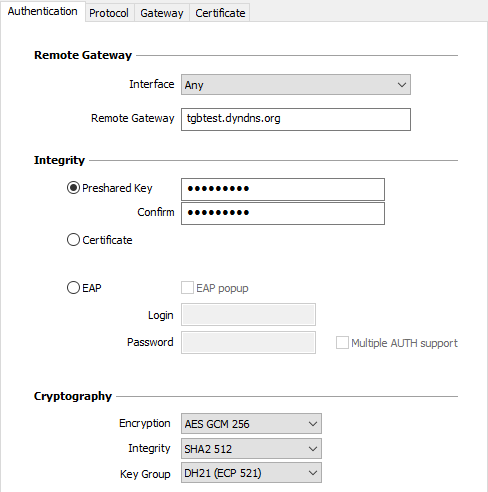
Addresses
| Interface |
Name of the network interface on which the VPN connection is open. The software can decide automatically which interface to use by selecting Any.
We recommend choosing this option if the tunnel being configured is to be deployed on a different workstation. NOTE
|
| Remote Gateway |
IP (IPv4 or IPv6) or DNS address of the remote VPN gateway. This field is mandatory. |
Authentication
| Preshared Key |
Password or key shared by the remote gateway. NOTE
|
| Certificate |
Use a certificate to authenticate the VPN connection. NOTE
Refer to the dedicated chapter Managing certificates. |
| EAP |
The Extensible Authentication Protocol (EAP) mode is used to authenticate the user based on a login name and password. When the EAP mode is selected, a pop-up window will prompt the user to enter a login name and password every time the tunnel is opened. When the EAP mode is selected, you can choose to display a prompt for the EAP login name and password every time the tunnel is opened (using the EAP popup checkbox) or to store them in the VPN configuration by entering them in the Login and Password fields. We recommend not to use the latter mode (see chapter Security recommendations). |
| Multiple AUTH support |
Enables the combination of certificate and EAP authentications. The VPN Client supports “Certificate then EAP” double authentication. The VPN Client does not support “EAP then Certificate” double authentication. |
Cryptography
| Encryption |
Encryption algorithm negotiated during the authentication phase: Auto, AES CBC (128, 192, 256), AES CTR (128, 192, 256), AES GCM (128, 192, 256). |
| Integrity |
Integrity algorithm negotiated during the authentication phase: Auto, SHA2 256, SHA2 384, SHA2 512. |
| Key Group |
Length of Diffie-Hellman key: Auto, DH14 (MODP 2048), DH15 (MODP 3072), DH16 (MODP 4096), DH17 (MODP 6144), DH18 (MODP 8192), DH19 (ECP 256), DH20 (ECP 384), DH21 (ECP 521) DH28 (BrainpoolP256r1). |
Refer to chapter Security recommendations on the choice of algorithm.
Auto means that the VPN Client automatically adapts to the gateway parameters.
IKE Auth: Protocol
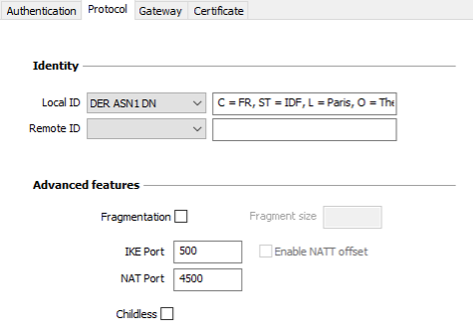
NOTE
If you use an IPsec DR gateway, you must add the dynamic parameter nonce_size (see section Displaying more parameters) and set its value to 16. These gateways will not accept any other nonce size.
Identity
| Local ID |
Local ID is the identifier that the VPN Client sends to the remote VPN gateway during the authentication phase. According to the type selected, this identifier can be any of the following:
If this parameter is not set, the VPN Client's IP address is used by default. |
| Remote ID |
Remote ID is the identifier of the authentication phase that the VPN Client expects to receive from the VPN gateway. According to the type selected, this identifier can be any of the following:
|
Advanced functions
| IKEv2 fragmentation |
Enables IKEv2 packet fragmentation in accordance with RFC 7383. This function prevents IKEv2 packets from being fragmented by the IP network they’re passing through. The fragment size must generally be set to a value that is smaller by 200 bytes than the MTU of the physical interface, e.g. 1300 bytes for a typical 1500-byte MTU. |
| IKE port |
IKE Init exchanges (during the IKE Authentication phase) use the UDP protocol and port 500 by default. IKE port configuration can bypass the networking hardware (firewalls, routers) that filter port 500. NOTE
|
| NAT port |
IKE Auth exchanges, IKE Child SA exchanges, and IPsec traffic use the UDP protocol and port 4500 by default. NAT port configuration can bypass the networking hardware (firewalls, routers) that filter port 4500. NOTE
|
| Enable NATT offset | When the IKE port is different from 500, it may be necessary to check this option for the gateway to accept the connection. |
| Childless | When this mode is enabled, the VPN Client will attempt to initiate IKE exchanges without creating any Child SA in accordance with RFC 6023. We recommend using this mode. |
IKE Auth: Gateway
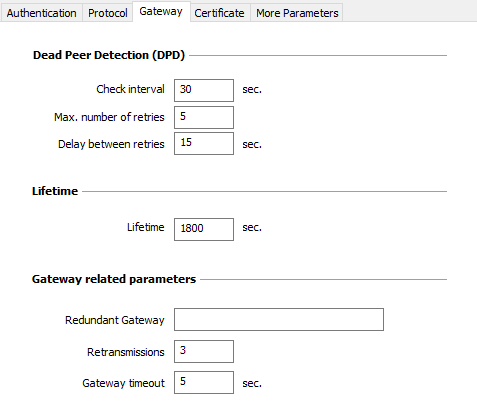
Dead Peer Detection (DPD)
| Check interval |
The Dead Peer Detection (DPD) function enables the VPN Client to detect whether the VPN gateway has become unreachable or inactive. The check interval is the time period between two consecutive DPD check messages sent, expressed in seconds. The DPD function is enabled upon opening the tunnel (after the authentication phase). When linked to a redundant gateway, DPD allows the VPN Client to automatically switch between gateways when one of them is unavailable. |
| Max. number of retries | Number of consecutive unsuccessful attempts before concluding that the VPN gateway is unreachable. |
| Delay between retries | Time between two DPD messages when the VPN gateway is not responding, expressed in seconds. |
IMPORTANT
A possible cause for the DPD function not working after a tunnel has been mounted could be that the gateway’s IP address belongs to the remote network, either due to a local configuration or because that’s the address the gateway sent. If this is the case, all IKE packets intended for the gateway are routed through the tunnel, instead of being sent outside of it. This is what’s causing the issue.
You therefore need to check whether this is the case and make the required changes where necessary to correct the issue.
Lifetime
| Lifetime |
Lifetime of the IKE Authentication phase. The lifetime is expressed in seconds. The default value is 14,400 seconds (4 h). |
Gateway-related parameters
| Redundant Gateway |
Used to define the address of a spare VPN gateway that the VPN Client will switch to when the initial gateway is unavailable or unreachable. The address of the redundant VPN gateway can be either an IP or a DNS address. IMPORTANT
Refer to chapter Redundant gateway. |
| Retransmissions | Number of IKE protocol message resends before failure. |
| Gateway timeout | Interval between two retransmissions. |
IKE Auth: Certificate
Refer to chapter Managing certificates.
Child SA: Overview
The purpose of the Child SA (Security Association IPsec) of a VPN tunnel is to negotiate the security parameters that will be applied to the data going through the VPN tunnel.
To configure Child SA parameters, select the Child SA in the VPN configuration tree. The parameters can be configured in the right-hand tabs of the Configuration Panel.
If any changes are made to a tunnel, it will appear in bold in the VPN configuration tree. You do not need to save a VPN configuration for it to be taken into account. The tunnel can be tested with the modified configuration immediately.
Child SA: Child SA:
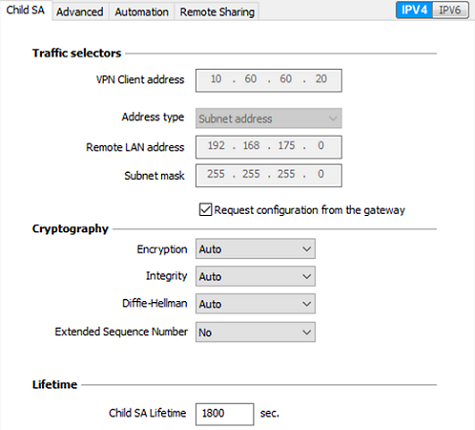
Traffic selectors
| VPN Client address |
“Virtual” IP address of the workstation, the way it will be “seen” on the remote network. From a technical standpoint, it is the source IP address of the IP packets going through the IPsec tunnel. NOTE
|
| Address type |
The endpoint of the tunnel can be a network or a remote workstation. Refer to section Configuring the address type below. |
| Request configuration from the gateway |
This option (also called “Configuration Payload” or “Mode CP”) lets the VPN Client get all the information required for the VPN connection from the gateway: VPN Client address, remote LAN address, subnet mask, and DNS addresses. When this option is checked, all corresponding fields are disabled (uneditable). They are filled in dynamically as the tunnel is opened with the values sent by the VPN gateway during the Mode CP exchange. NOTE
NOTE
|
Cryptography
| Encryption |
Encryption algorithm negotiated during the IPsec phase: Auto, AES CBC (128, 192, 256), AES CTR (128, 192, 256), AES GCM (128, 192, 256). |
| Integrity |
Integrity algorithm negotiated during the IPsec phase: Auto, SHA2 256, SHA2 384, SHA2 512. |
| Diffie-Hellman |
Length of Diffie-Hellman key: Auto, DH14 (MODP 2048), DH15 (MODP 3072), DH16 (MODP 4096), DH17 (MODP 6144), DH18 (MODP 8192), DH19 (ECP 256), DH20 (ECP 384), DH21 (ECP 521), DH28 (BrainpoolP256r1). |
| Extended Sequence Number |
Allows you to use 64-bit extended sequence numbers (see RFC 4304): Auto, No, Yes. We recommend using the ESN mode. |
Refer to chapter Security recommendations on the choice of algorithm.
Auto means that the VPN Client automatically adapts to the gateway parameters.
NOTE
If the IP address of the VPN Client workstation is included in the address range for a remote network (e.g. @workstation IP=192.168.10.2 and @remote network=192.168.10.x), then opening a tunnel will prevent the workstation from communicating on the local network. All communications will go through the VPN tunnel.
Lifetime
| Child SA Lifetime |
Time interval, expressed in seconds, between two renegotiations. The default value for the Child SA lifetime is 1,800 s (30 min). |
IPv4/IPv6
| IPv4/IPv6 |
Refer to chapter IPv4 and IPv6. |
Configuring the address type
| If the endpoint of the tunnel is a network, choose the Subnet address type and then enter the Remote LAN address and Subnet mask: |
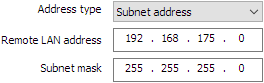
|
| As an alternative, you can also select Range address and enter the Start address and End address: |
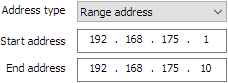
|
| If the endpoint of the tunnel is a workstation, choose the Single address type and then enter the Remote host address: |
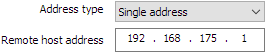
|
- The function Automatically open this tunnel on traffic detection is used to automatically open a tunnel when traffic with one of the addresses specified in the address range is detected (provided that this address range is authorized in the VPN gateway configuration).
- “All traffic through the VPN tunnel” configuration
The VPN Client can be configured so that all the workstation’s outbound traffic goes through the VPN tunnel. To implement this function, select Subnet address as the address type and specify 0.0.0.0 as the Remote LAN address and Subnet mask.
Child SA: Advanced
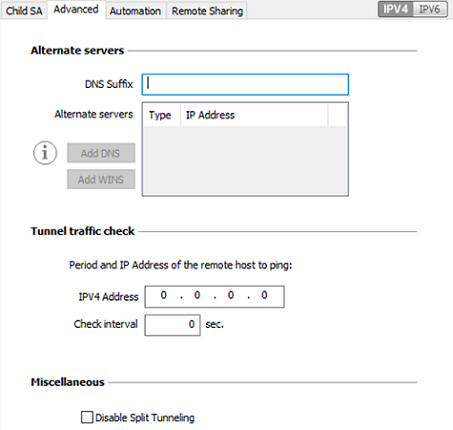
Alternate servers
| DNS Suffix |
Domain suffix to be added to all machine names. This is an optional parameter. When it is specified, the VPN Client will try to translate the machine address without adding the DNS suffix. However, if translation fails, the DNS suffix will be added, and the Client will try to translate the address again. |
| Alternate servers |
Table containing the IP addresses of the DNS (maximum 2) and WINS (maximum 2) servers available on the remote network. The IP addresses will be IPv4 or IPv6 addresses depending on the network type configured in the Child SA tab. NOTE
|
Tunnel traffic check
| Traffic check after opening |
The VPN Client can be configured so that connectivity to the remote network is checked on a regular basis. If connectivity has been lost, the VPN Client will automatically close the tunnel and attempt to open it again. The IPV4/IPV6 field is the address of a machine within the remote network, which should reply to pings sent by VPN Client. If a ping goes unanswered, the connection is considered lost. NOTE
|
| Check interval | The Check interval indicates the time interval in seconds between two pings sent by the VPN Client to the machine with the IP address specified above. |
Miscellaneous
| Disable Split Tunneling |
When this option is selected, only the traffic going through the tunnel is authorized.
The Disable Split Tunneling configuration option increases the “leakproofness” of the workstation, provided that the VPN tunnel is open. More specifically, this function eliminates the risk of incoming data flows that do not go through the VPN tunnel. When combined with the All traffic through the VPN tunnel configuration (see section Configuring the address type), this option guarantees the complete leakproofness of the workstation, provided that the VPN tunnel is open. We recommend using this mode. |
Child SA: Automation
Refer to chapter Automation.
Child SA: Remote sharing
Refer to chapter Remote Desktop Sharing.
Configuring an SSL/OpenVPN tunnel
Introduction
SN VPN Client Exclusive can be used to open SSL VPN tunnels.
SSL VPN tunnels established by SN VPN Client Exclusive are compatible with OpenVPN and can establish secure connections with all gateways implementing this protocol.
SSL: Authentication
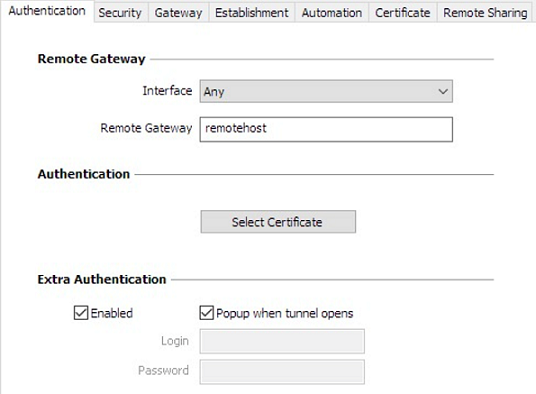
Remote Gateway
| Interface |
Name of the network interface on which the VPN connection is open. The software can decide automatically which interface to use by selecting Any.
We recommend choosing this option if the tunnel being configured is to be deployed on a different workstation. |
| Remote Gateway |
IP (IPv4 or IPv6) or DNS address of the remote VPN gateway. This field is mandatory. |
Authentication
| Select certificate |
Choose a certificate for VPN connection authentication. Refer to the dedicated chapter Managing certificates. |
Extra Authentication
| Extra Authentication |
This option increases the security level by asking the user to enter a login name and password whenever a tunnel is opened. When the box Popup when tunnel opens is checked, users will be prompted for their login name and password whenever they open the tunnel. When it is unchecked, the login name and password must be entered here permanently. Users therefore will not need to enter them every time they open the tunnel. |
SSL: Security
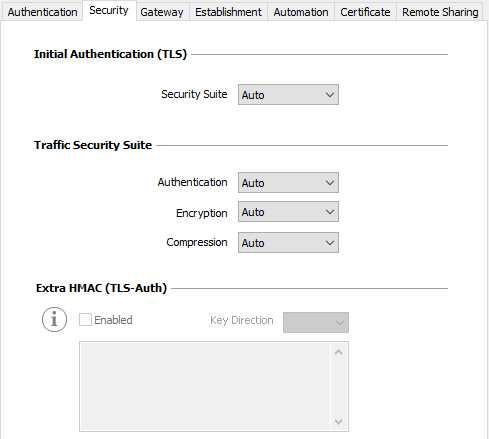
Initial Authentication (TLS)
| Security Suite |
This parameter is used to configure the security level of the authentication phase during the SSL exchange.
For further information: https://www.openssl.org/docs/man1.1.1/man1/ciphers.html |
Traffic Security Suite
| Authentication |
Authentication algorithm negotiated for traffic: Auto, SHA-224, SHA-256, SHA-384, SHA-512. NOTE
|
| Encryption |
Traffic encryption algorithm: Auto, AES-128-CBC, AES-192-CBC, AES-256-CBC. |
| Compression |
Traffic compression: Auto, LZ0, No, LZ4. |
Auto means that the VPN Client automatically adapts to the gateway parameters
Extra HMAC (TLS-Auth)
| Extra HMAC |
This option adds an authentication layer to the packets exchanged between the VPN Client and the VPN gateway. For this option to be fully operational, it must also be configured on the gateway (on gateways, this option is often referred to as “TLS-Auth”). If this option is enabled, a key must be entered in the field below the checked box. The same key must also be entered on the gateway. It consists of a string of hexadecimal characters, in the following format: -----BEGIN Static key----- The Key Direction must also be defined:
|
SSL: Gateway
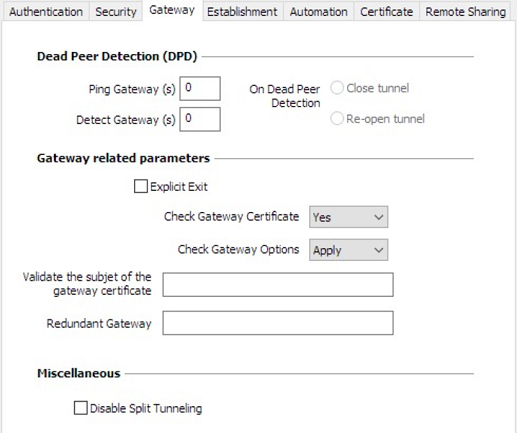
Dead Peer Detection (DPD)
The Dead Peer Detection (DPD) function enables both endpoints of the tunnel to mutually make sure the other one is active.
The DPD function is enabled once the tunnel is open. When linked to a redundant gateway, DPD allows the VPN Client to automatically switch between gateways when one of them is unavailable.
| Ping Gateway (s) |
Period, expressed in seconds, between two pings sent by the VPN Client to the gateway. Sending this ping enables the gateway to determine whether the VPN Client is still active. |
|
Detect Gateway (s) |
Time, expressed in seconds, after which the gateway is considered down if no ping has been received. |
| On Dead Peer Detection |
When the gateway is detected as unavailable (i.e. once the Detect Gateway time has expired), the tunnel can be closed, or the VPN Client may try to open it again. |
Gateway-related parameters
| Explicit Exit |
This parameter configures the VPN Client to send a specific VPN tunnel closing frame to the gateway when closing the tunnel. If this option is not selected, the gateway will use DPD to close the tunnel at its end, which is less effective. |
| Check Gateway Certificate |
Specifies the control level applied to the gateway certificate. In the current version, two levels are available:
The Lite option is reserved for future use. In this version, it is equivalent to the Yes option. If the Check gateway certificate signature option is enabled in the PKI Options (see section PKI Options), the present option on the Gateway tab is grayed out and the option is set to Yes. |
| Check Gateway Options |
Used to determine the level of consistency between the VPN tunnel and gateway parameters (encryption algorithms, compression, etc.).
|
| Validate the subject of the gateway certificate |
If this field is filled in, the VPN Client will check that the subject of the certificate received from the gateway is, indeed, the one specified. |
|
Redundant Gateway |
Defines the address of a spare VPN gateway that the VPN Client will switch to when the initial gateway is unavailable or unreachable. The address of the redundant VPN gateway can be either an IP or a DNS address. IMPORTANT
Refer to chapter Redundant gateway. |
Miscellaneous
| Disable Split Tunneling |
When this option is selected, only the traffic going through the tunnel is authorized. The Disable Split Tunneling configuration option increases the “leakproofness” of the workstation, provided that the VPN tunnel is open. More specifically, this function eliminates the risk of incoming data flows that do not go through the VPN tunnel. |
SSL: Establishment
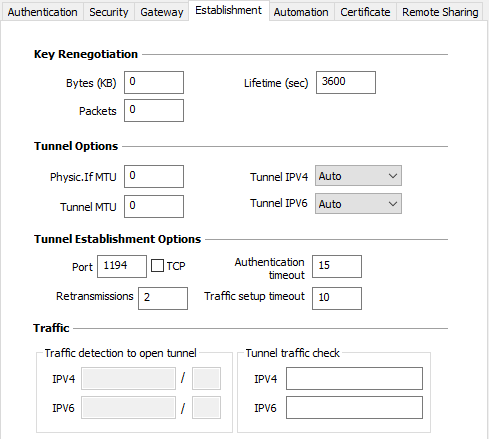
Key Renegotiation
| Bytes (KB), Packets, Lifetime (sec) |
Keys can be renegotiated when any of the three criteria (which can be combined) expire:
If more than one criterion is set, keys will be renegotiated when the first of these expires. |
Tunnel Options
| Physical interface MTU |
Maximum size of OpenVPN packets. Used to set a packet size so that OpenVPN frames are not fragmented at the network level. The default value for MTU is 0, meaning that the software will use the MTU value of the physical interface. |
| Tunnel MTU |
Virtual interface MTU. When values have been entered, we recommend setting a lower value for the tunnel MTU than that of the physical interface MTU. The default value for MTU is 0, meaning that the software will use the MTU value of the physical interface. |
| Tunnel IPV4 |
Defines the VPN Client’s behavior when it receives an IPv4 configuration from the gateway:
NOTE
|
| Tunnel IPV6 |
Defines the VPN Client’s behavior when it receives an IPv6 configuration from the gateway:
NOTE
|
Tunnel Establishment Options
| Port/TCP |
Port number used to establish the tunnel. The default port value is set to 1194. The tunnel will use UDP by default. The TCP option is used to transport the tunnel over TCP. |
| Authentication Timeout |
Time allowed to establish the authentication phase. When this time expires, it is assumed that the tunnel will not open. When this timeout expires, the tunnel is closed. |
| Retransmissions |
Number of retries for sending a protocol message. If there is no response by the time the defined number of retries is reached, the tunnel is closed. |
| Traffic setup timeout |
Tunnel establishment phase: time after which the tunnel is closed, if not all the steps have been completed. |
Traffic
| Traffic detection to open the tunnel |
With OpenVPN, the remote network’s details are not configured (they are automatically obtained during the tunnel opening exchange with the gateway). To implement traffic detection with OpenVPN, the remote network’s details must therefore be stated explicitly. That is the purpose of the IPv4 and IPv6 fields. It is not mandatory to fill in both fields. The IP field is a sub-network address, configured as an IP address and a prefix length. Example: IP = 192.168.1.0 / 24: the first 24 bits of the IP address are taken into account, i.e. the network: 192.168.1.x NOTE
|
| Tunnel traffic check |
If these fields are filled in, the VPN Client will try to ping these addresses after opening the VPN tunnel. The connection status (reply to pings or no reply to pings) is shown in the Console. It is not mandatory to fill in both fields. NOTE
|
SSL : Automation
Refer to chapter Automation.
SSL : Certificate
Refer to chapter Managing certificates.
SSL : Remote sharing
Refer to chapter Remote Desktop Sharing.