Managing certificates
Introduction
SN VPN Client Exclusive includes a selection of interfacing functions with all types of certificates, issued by any PKI, and on any type of storage device, such as smart card, token, certificate store, and configuration file.
SN VPN Client Exclusive implements the following features:
-
Automatic selection of the medium to use from among several
-
PKCS#11 and CNG access to tokens and smart cards
-
Selection of certificates to use according to multiple criteria: subject, key usage, etc.
-
Management of certificates on user’s side (the VPN Client’s side), such as VPN gateway certificates, including validity date, certificate chain, root certificate, intermediate certificate, and CRL management
-
Certificate authority (CA) management
-
Option to pre-configure all PKI parameters for automatic integration during installation
SN VPN Client Exclusive provides additional security features for PKI management, such as automatically opening or closing a tunnel upon insertion or removal of a smart card or token, or even the ability to configure the PKI interface in the software setup file in order to automate deployment.
The list of smart cards and tokens compatible with SN VPN Client Exclusive is available on TheGreenBow’s website at: https://www.thegreenbow.com/en/support/integration-guides/compatible-vpn-tokens/.
The certificates to be used are configured and specified in three steps as follows:
-
The Certificate tab of the relevant tunnel: IKE Auth (IKEv2) or TLS (SSL).
-
The PKI Options tab of the Tools > Options window in the Configuration Panel.
-
A configuration file for smart card readers and tokens called vpnconf.ini (refer to the “Deployment Guide”).
The following certificate types are supported:
-
RSASSA-PKCS1-v1.5 with SHA-2 (only if the corresponding dynamic parameter has been configured, see section Certificate authentication methods)
-
RSASSA-PSS with SHA-2 (only if the corresponding dynamic parameter has been configured, see section Certificate authentication methods)
-
ECDSA “secp256r1” with SHA-2 (256 bits)
-
ECDSA “BrainpoolP256r1” with SHA-2 (256 bits)
To find out more about the authentication methods and cryptography used in the SN VPN Client Exclusive, refer to section Basic cryptography concepts in the appendix.
User certificate
Overview
The VPN Client sends the user certificate to the gateway so that it can authenticate the user.
It must comply with the following constraints (ANSSI security recommendations):
-
• The Key Usage extension must be present, marked as critical, and only contain the value digitalSignature.
-
• The Extended Key Usage extension must be present, marked as critical, and only contain the value id-kp-clientAuth.
If these constraints are not observed, the VPN Client will display a warning in the Console but will not prevent communication with the gateway. However, the gateway should refuse the authentication of the VPN Client.
Dynamic parameters
As of version SN VPN Client Exclusive 7.4, two dynamic parameters now replace the corresponding MSI properties. They are defined within the IKE_AUTH authentication payload and apply to a given tunnel, whereas the MSI properties apply to all tunnels.
user_cert_dnpattern
The dynamic parameter user_cert_dnpattern is used to specify the certificate to be used. When it is defined, SN VPN Client Exclusive searches for the certificate whose subject contains the [text] pattern on the token, smart card or in the Windows certificate store.
If this dynamic parameter is not specified, the VPN Client searches for the first certificate that meets the other characteristics configured.
user_cert_keyusage
The dynamic parameter user_cert_keyusage is used to select a certificate based on its “key usage” field:
-
0 or undefined : Certificate is not selected based on “key usage” field.
-
1 : Certificate is selected based on “key usage” field whose attribute digitalSignature=1.
-
2 : Certificate is selected based on “key usage” field whose attributes digitalSignature=1 and keyEncipherment=1.
NOTE
When the value of the dynamic parameter user_cert_keyusage is set to 2, the Only use authentication certificate check box on the PKI Options tab is grayed out (see section PKI Options).
Automatic selection
As of version SN VPN Client Exclusive 7.4, an option can be used to automatically select the user certificate from a token/smart card, the Windows certificate store, or both.
The Certificate tab of an IKE or SSL connection includes an Automatic selection entry with the following options:
-
From a smart card
-
From the Windows Store
-
From both
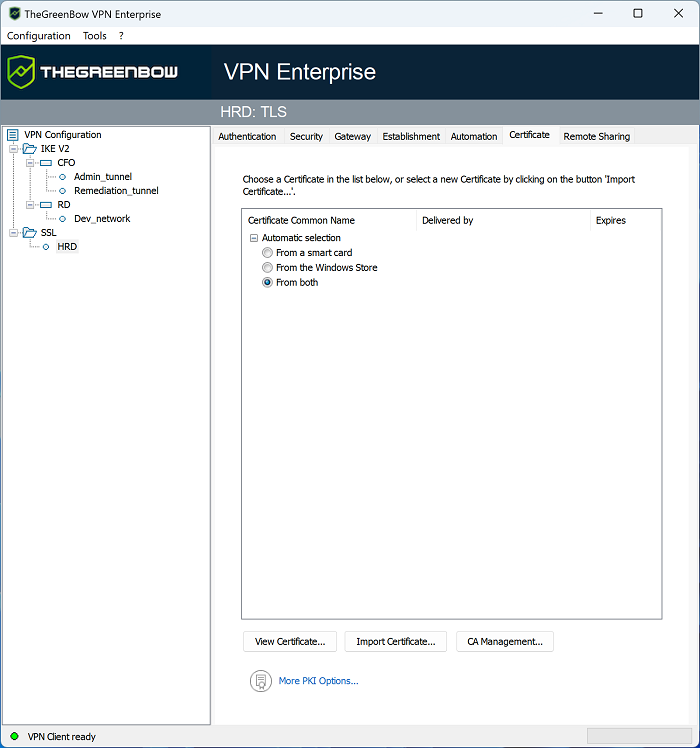
If you choose the latter option, the software will first look for the user certificate on a token/smart card. If it cannot find any, it will continue to search for a certificate in the Windows Certificate Store.
If you choose From a smart card or From both and you use several token/smart card readers, you must configure the dynamic parameter reader_pattern to specify the reader from which the certificate should be selected (see section Displaying more parameters). As value for this parameter, specify the name of the drive (e.g. NEOWAVE) or Virtual if it is a Trusted Platform Module (TPM).
NOTE
As of version SN VPN Client Exclusive 7.5, when several smart cards from the same manufacturer are used with identical smart card readers, the dynamic parameter user_smartcard_tip can be set to a desired value at the IKE Auth level, which will be displayed when the password is requested to help clearly identify the smart card (see section Displaying more parameters).
If you have previously imported a certificate into the configuration and you decide to choose automatic selection, a warning will be displayed to inform you that the certificate will be removed from the configuration when you save it.
Selecting a certificate (Certificate tab)
The VPN Client can assign a user certificate to a VPN tunnel.
There can only be one certificate per tunnel, but each tunnel can have its own certificate.
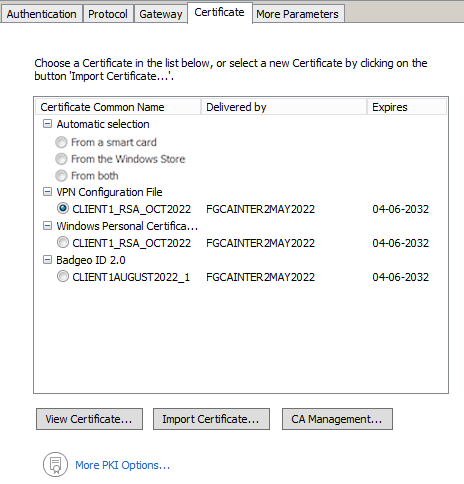
The VPN Client allows you to choose a stored certificate:
-
In the VPN configuration file (see below Importing a certificate to the VPN configuration)
-
On a smart card or token (see below Using a certificate stored on a smart card or token)
-
In the Windows Certificate Store (see below Using a certificate stored in the Windows Certificate Store)
The Certificate tab for the relevant tunnel lists all accessible storage media that contain certificates.
-
The smart card or token is compatible with CNG or PKCS#11
-
The smart card or token middleware is correctly installed on the computer
-
Where appropriate, the smart card is correctly inserted into the corresponding reader
If a medium does not contain any certificates, it simply will not appear in the list (e.g. if the VPN configuration file does not contain any certificates, it will not appear in the list).
Clicking the desired medium displays the list of certificates it contains.
NOTE
For smart cards readers, the reader is displayed with a warning icon in front, if the smart card is not inserted.
Click the desired certificate to assign it to the VPN tunnel.
NOTE
Only available certificates that have not expired are displayed.
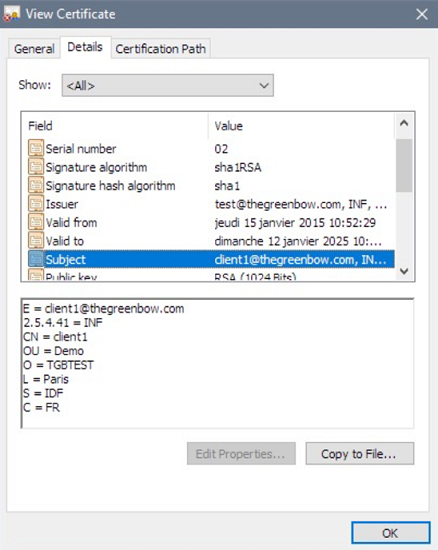
Once a certificate has been selected, the View Certificate button will show detailed information about the certificate.
NOTE
Once a certificate has been selected, the tunnel’s Local ID type will automatically switch to DER ASN1 DN and the certificate’s subject will be used as the default value of this Local ID. See below to find out how to automatically assign a DNS or e-mail value retrieved from the certificate.
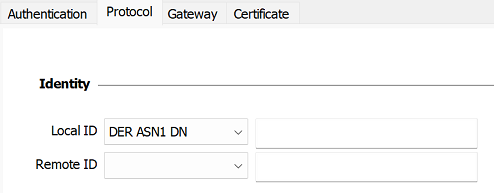
As of version SN VPN Client Exclusive 7.3, you can select DNS or Email from the Local ID drop-down list to automatically assign to the Local ID a DNS or e-mail value retrieved from the certificate.
If you choose DNS, the Local ID will automatically take the value of the dNSName field of the certificate subject alternative name (SubjAltName). If this field has not been filled in (no SubjAltName in the certificate or no dNSName in the SubjAltName), the CN value of the certificate subject will be used instead. If the latter value is also missing, no certificate is available to configure the tunnel and any attempt to establish the tunnel will fail.
If you choose Email, the Local ID will automatically take the value of the rfc822Name field of the certificate subject alternative name (SubjAltName). If this field has not been filled in (no SubjAltName in the certificate or no rfc822Name in the SubjAltName), the Email value of the certificate subject will be used instead. If the latter value is also missing, no certificate is available to configure the tunnel and any attempt to establish the tunnel will fail.
NOTE
As of version SN VPN Client Exclusive 7.4, an option can be used to automatically select the user certificate from a token/smart card, the Windows certificate store, or both (see section Automatic selection).
Importing a certificate to the VPN configuration
SN VPN Client Exclusive can import certificates in PEM/PFX or PKCS#12 format to the VPN configuration. This solution is less secure than using the Windows Certificate Store, a smart card, or a token, but it makes it easier to transport certificates.
This solution has the advantage of combining the certificate (user-specific) and the VPN configuration (generic) in a single file, which can easily be sent to the user’s workstation and imported into the VPN Client.
Nevertheless, the disadvantage of transporting certificates in a VPN configuration is that each configuration then becomes user-specific. We therefore do not recommend this solution for a substantial deployment.
IMPORTANT
Whenever you import a certificate into a VPN configuration, we strongly recommend that you protect the configuration file with a password when you export it (see section Exporting a VPN configuration) so that the certificate does not become visible in clear text.
Importing a PEM/PFX certificate
-
On the Certificate tab of an IKE Auth, click Import Certificate….
-
Choose PEM Format.
-
Click on Browse to select the Root Certificate and the User Certificate as well as the User Private Key to import.
-
Click on OK to confirm.
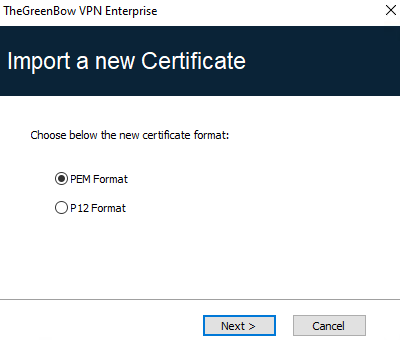
The certificate is shown and is selected in the certificate list displayed on the Certificate tab.
Save the VPN configuration. The certificate will be saved in the VPN configuration.
NOTE
The file containing the private key may not be encrypted.
Importing a PKCS#12 certificate
-
On the Certificate tab of a Child SA, click Import Certificate….
-
Choose P12 Format.
-
Click on Browse to select the PKCS#12 certificate to import.
IMPORTANT
For security reasons, as of version 7.5 of SN VPN Client Exclusive, PKCS#12 certificates encrypted with the RC2 algorithm are no longer supported and cannot be imported.
-
If it is password-protected, enter the password and click on OK to confirm.
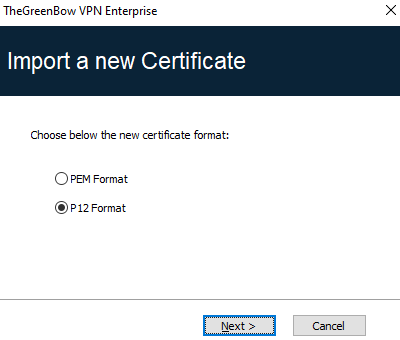
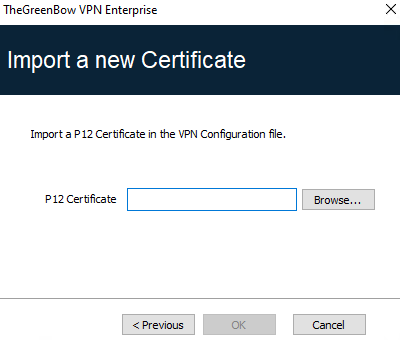
The certificate is added to the certificate list displayed on the Certificate tab and is selected.
Save the VPN configuration. The certificate will be saved in the VPN configuration.
NOTE
All CAs in the file that are in PKCS#12 format will also be imported to the VPN configuration.
Using a certificate stored on a smart card or token
When a VPN tunnel is configured to use a certificate stored on a smart card or token, users will be prompted for the PIN code required to access this smart card or token every time a tunnel is opened.
If the smart card is not inserted or the token cannot be accessed, the tunnel will not open.
If the certificate found does not meet the configured criteria (see section Importing a certificate depending on the store used device below), the tunnel will not open.
If an incorrect PIN is entered, SN VPN Client Exclusive will show a warning, informing users that they only have three (in most cases) consecutive attempts to unlock the smart card or token.
SN VPN Client Exclusive implements a mechanism to automatically detect smart card insertion.
Tunnels that are associated with a certificate stored on a smart card will therefore be established automatically when the smart card is inserted. Likewise, removing the smart card will close all the corresponding tunnels.
To implement this function, check Automatically open this tunnel when a USB stick is inserted (see chapter Automation).
NOTE
As of version SN VPN Client Exclusive 7.4, an option can be used to automatically select the user certificate from a token/smart card, the Windows certificate store, or both (see section Automatic selection).
NOTE
As of version SN VPN Client Exclusive 7.5, when several smart cards from the same manufacturer are used with identical smart card readers, the dynamic parameter user_smartcard_tip can be set to a desired value at the IKE Auth level, which will be displayed when the password is requested to help clearly identify the smart card (see section Displaying more parameters).
Using a certificate stored in the Windows Certificate Store
Required characteristics
NOTE
To offer finer granularity in how the choice of certificate store to use is configured, as of version SN VPN Client Exclusive 7.5, this choice is no longer made at the workstation level, but at the tunnel level.
For SN VPN Client Exclusive to identify a certificate available in the Windows Certificate Store, the certificate must meet the following criteria:
-
The certificate must be certified by a certification authority (which excludes self-signed certificates)
-
By default, the certificate must be located in the “Personal” Certificate Store (it represents the personal identity of the user who wants to open a VPN tunnel to the corporate network) To use the Windows Machine Certificate Store, add dynamic parameter MachineStore set to the value true (see section Displaying more parameters).
NOTE
Microsoft provides a standard management tool (certmgr.msc) to manage the certificates in the Windows Certificate Store. To run this tool, go to the Windows Start menu and then enter certmgr.msc in the Search for programs or files field.
Importing a certificate depending on the store used
When importing certificates using the CNG middleware, the store used (user or machine store) must be specified in the command line. Below you will find examples of command lines with the options you need to specify.
-
User store:
certutil -csp KSP -user -importpfx CertFileName.p12
-
Machine store:
certutil -csp KSP -importpfx CertFileName.p12
NOTE
In command lines, the -user option of the certutil command is used to specify the user store. When it is omitted, the machine store will be used by default.
NOTE
As of version SN VPN Client Exclusive 7.4, an option can be used to automatically select the user certificate from a token/smart card, the Windows certificate store, or both (see section Automatic selection).
PKI options: specifying the certificate and its storage device
SN VPN Client Exclusive provides several ways in which to specify the certificate to use, as well as to select the smart card reader or token that contains the certificate.
This feature is available under the More PKI options link at the bottom of the Certificate tab and on the PKI options tab of the Options configuration window.
VPN gateway certificate
We recommend forcing SN VPN Client Exclusive to check the certificate chain of the certificate received from the VPN gateway (default behavior).
See section Certificate Check.
To do this, you need to import the root certificate and all certificates in the certificate chain (root certificate authority and intermediate certificate authorities) to the configuration file.
If the option is checked, the VPN Client will also use the Certificate Revocation List (CRL) of the various certificate authorities.
If these CRLs are not in the certificate store, or if these CRLs cannot be downloaded when the VPN tunnel is opened, the VPN Client will not be able to validate the gateway certificate.
Checking each item in the chain implies the following:
-
Checking gateway certificate expiration date
-
Checking certificate validity start date
-
Checking signatures of all certificates in the certificate chain (including root certificate, intermediate certificates, and server certificate)
-
Checking whether the CRLs of all certificate issuers within the chain of trust
NOTE
As of version SN VPN Client Exclusive 7.5, you can check the revocation of the gateway certificate using Online Certificate Status Protocol Stapling (OCSP Stapling). To do this, you must add the dynamic parameter enable_OCSP set to the value true (see section Displaying more parameters).
Preventing or limiting CRL download
Introduction
A Certificate Revocation List (CRL) contains all the certificates that are no longer valid (validity date has expired, private key associated with the certificate has been lost or compromised, a field concerning the owner has been changed, etc.) and therefore cannot be trusted.
CRLs are defined in the RFC 5280 and 6818.
CRLs are published by certificate authorities (CAs) and Public Key Infrastructures (PKIs).
In some cases, these lists can be relatively large (several MB). Downloading them can therefore take time and slow down the time it takes to open a tunnel when a great number of users contacts the HTTP server at the same time.
SN VPN Client Exclusive provides two dynamic parameters described below to speed up the time it takes to open a tunnel. These parameters work independently from one another and can be combined.
The first dynamic parameter, named check_user_crl, prevents the download of the CRL used to validate the user certificate. The second, named crl_cache_duration, limits the download of the CRL used to validate the gateway CRL.
Preventing download of CRL used to validate the user certificate
By default, when the VPN Client verifies the user certificate (e.g. because it is issued by a known CA), it also verifies the CRL to determine whether the certificate is still valid. If the certificate is no longer valid, a simple warning is entered in the Console. Ultimately, it is up to the gateway to decide whether the user certificate can be accepted or not.
In order to prevent downloading the CRL and thus speed up the time it takes to open a tunnel, you can add the dynamic parameter check_user_crl set to the value false (see section Displaying more parameters). In this case, the user certificate CRL is not verified. The gateway will handle this verification.
Limiting download of CRL used to validate the gateway certificate
If you want to limit the number of times a CRL is downloaded to validate the gateway certificate without preventing its download altogether—again with the aim to speed up the time it takes to open a tunnel—you can add the dynamic parameter crl_cache_duration set to a value corresponding to the number of hours during which the CRL is stored in the cache memory (see section Displaying more parameters).
When the value of the parameter is set to zero, the caching of the CRL is disabled. Caching is limited to a maximum of seven days, i.e. 168 hours. Any value greater than 168 will be considered equal to the maximum of seven days.
When this dynamic parameter is configured with a value different from zero, the CRL will be stored in a cache memory and an expiration time in hours will be set for this CRL. As long as the expiration time has not passed, the CRL in the cache memory will be used and no download is performed. When the time has expired, the CRL is downloaded and updated in the cache memory.
Constraints on the Key Usage extension
The gateway certificate must comply with the following constraints on the Key Usage extension. The extension must:
-
Be present
-
Be marked as non-critical, and
-
Only contain the values digitalSignature and/or nonRepudiation
In the event that the VPN gateway does not comply with the constraints on the Key Usage extension mentioned above, you can configure the VPN Client so that it validates the certificate despite this, by adding the dynamic parameter allow_server_and_client_auth set to the value true (see section Displaying more parameters).
In this configuration, the certificate will also be validated if the Key Usage extension contains one of the following combinations of values:
-
digitalSignature + keyEncipherment + keyAgreement
-
digitalSignature + keyAgreement
-
nonRepudiation + keyEncipherment
-
nonRepudiation + keyEncipherment + keyAgreement
-
nonRepudiation + keyAgreement
-
keyEncipherment
-
keyEncipherment + keyAgreement
Moreover, in this configuration the Key Usage extension can be marked as non-critical.
NOTE
In accordance with security requirements, the keyEncipherment value of the Key Usage extension has been deprecated and replaced with the nonRepudiation value, which is now accepted by default. However, SN VPN Client Exclusive version 7.5 continues to accept the keyEncipherment value without needing to use dynamic parameter allow_extra_keyusage.
TIP
We recommend that you give preference to the nonRepudiation value over the keyEncipherment value of the Key Usage extension.
Constraints on the Extended Key Usage extension
The gateway certificate must comply with the following constraints on the Extended Key Usage extension. The extension may be present or not. If it is present, it must:
-
Be marked as non-critical, and
-
Only contain the following values:
-
id-kp-serverAuth or
-
id-kp-serverAuth + id-kp-ipsecIKE
-
In the event that the VPN gateway does not comply with the constraints on the Extended Key Usage extension mentioned above, you can configure the VPN Client so that it validates the certificate despite this, by adding the dynamic parameter allow_server_and_client_auth set to the value true (see section Displaying more parameters).
In this configuration, the certificate will also be validated if the Extended Key Usage extension contains one of the following combinations of values:
-
id-kp-ServerAuth + id-kp-ClientAuth or
-
id-kp-ServerAuth + id-kp-ClientAuth +
id-kp-ipsecIKE
Managing certification authorities
Overview
If the SN VPN Client Exclusive is configured to check gateway certificates, the Certificate Authorities (CAs) must also be accessible.
You must import the gateway’s root CA into the configuration.
If the gateway is not configured to send CAs, you must also import the intermediate CAs into the configuration.
NOTE
As of version SN VPN Client Exclusive 7.3, you can create configurations with more than three certificate authorities (CAs).
The following intermediate CA types are supported:
-
RSASSA-PKCS1-v1.5 with SHA-2,
-
RSASSA-PSS with SHA-2,
-
ECDSA “secp256r1” with SHA-2
-
ECDSA “BrainpoolP256r1” with SHA-2
The following Root CA types are supported:
-
RSASSA-PKCS1-v1.5 with SHA-2,
-
RSASSA-PSS with SHA-2,
-
ECDSA “secp256r1” with SHA-2
-
ECDSA “BrainpoolP256r1” with SHA-2
NOTE
For security reasons, the Windows Certificate Store may not be used to access CAs.
Importing a certificate authority
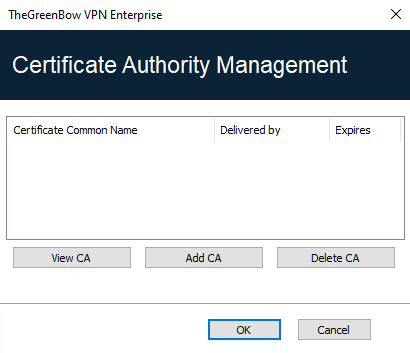
-
In the Certification Authority Management window, click on Add CA.
-
Choose the desired CA certificate type (PEM or DER).
-
Click on Browse and then select the CA to import.
IPsec DR mode
To be able to use SN VPN Client Exclusive in IPsec DR (Restricted) mode, compliance with ANSSI’s IPsec DR framework requires the Certification Authority value in the certificate request payload (CERTREQ) to be a concatenated list of SHA-2 hashes derived from the public keys of the trusted certification authorities.
As of SN VPN Client Exclusive version 7.5, the VPN Client automatically detects the format (SHA-1 or SHA-2) based on the length of the certificate request payload [CERTREQ] it receives from the gateway. This automatic selection is only performed if the dynamic parameter sha2_in_cert_req is not present.
If you want to select the format manually, you can add the dynamic parameter sha2_in_cert_req set to the value true for SHA-2 or false for SHA-1 (see section Displaying more parameters).
NOTE
If the length of the certificate request payload cannot be used to determine the format, SHA-1 is used. When connecting to a gateway configured in IPsec Restricted mode, you must therefore use the dynamic parameter sha2_in_cert_req to make sure the correct format is selected.