Isolating computers from the network
When an attack occurs or is suspected in your pool, the affected computers can be isolated from the network. By Isolating computers, incoming and outgoing connections can be shut down immediately, preventing any attack from spreading to the rest of the network, or exfiltrating data to the attacker's servers.
While computers are being isolated, communication between agents and agent handlers is maintained, so that you can perform analysis and remediation operations if necessary. When the intervention is complete, you can undo the isolation of the computers and restore connections.
From the SES Evolution administration console you can:
-
Isolate computers,
-
Monitor isolated computers,
-
Run Yara or IoC scan tasks and remediation tasks on isolated workstations,
-
Undo isolation of the computers.
Requests to isolate and undo isolation are logged in System and Agent logs.
The isolation feature can be used if all the following conditions are met:
-
Computers can be isolated on SES Evolution agents as of version 2.5.3.
NOTE
If you request the isolation of a set of agents in different software versions, only eligible agents will be isolated, i.e., those in at least version 2.5.3.
-
The SES Evolution agent must be able to communicate with its agent handler to apply requests to isolate computers and remove them from isolation. Agents that are disconnected from the agent handler cannot apply such requests.
-
The Networks feature must be enabled in agent group settings:
-
You must hold the Remediation-Modify permission to isolate computers, undo their isolation and edit the list of connections allowed during isolation.
If you hold the Agent groups - Show permission, you can look up the isolation status of computers in the agent group panel.
Computers can be isolated regardless of the security policy applied to agents.
The feature can be accessed from two panels in the console:
-
In the Agents panel, from the All agents view or from an agent group view, select one or more agents from the list and click on the Isolate computers button at the top of the panel.
-
In the Agent logs panel, you can isolate one or more computers directly from a log or log group if you detect a suspicious event. Select one or more logs and click on the Actions > Response > Isolate computer button at the top of the panel.
The following window will appear, allowing you to create the isolation task:
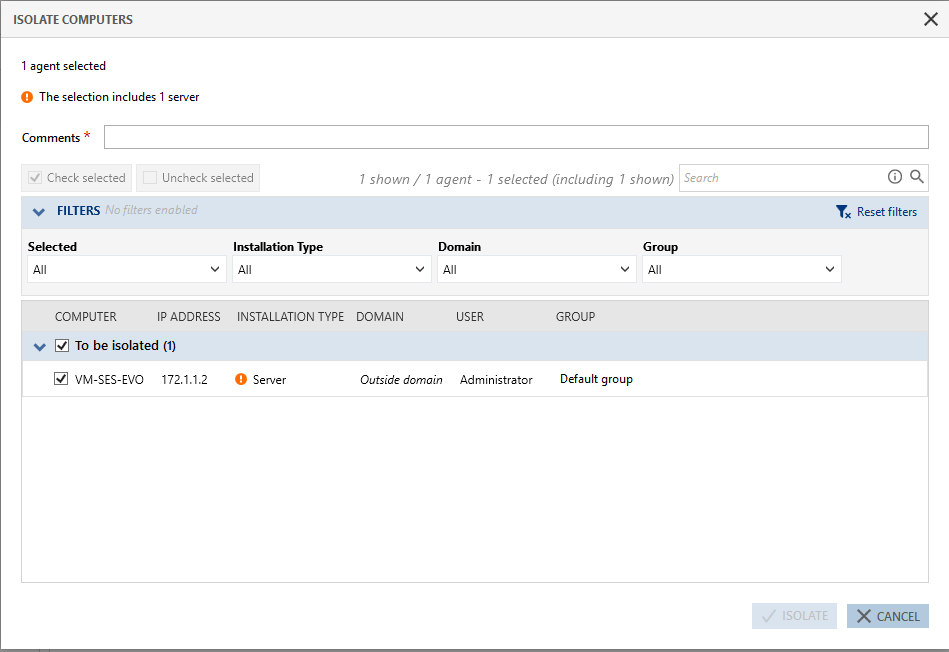
The agents selected during the isolation request appear in the list. You can filter the display.
-
Enter a comment.
-
Check the selection of agents to be isolated. If your agent selection includes agents installed on server workstations, confirm that you wish to isolate these workstations. Application services installed on these workstations will no longer be accessible (web or mail server, file server, etc.).
-
Click on Isolate.
The isolation monitoring panel appears (Responses > Isolation menu). For more information, refer to the section Monitoring and analyzing isolated computers.
As soon as the agent receives an isolation request:
-
TCP and UDP connections that have already been opened to outside networks will be shut down. However, you can allow some connections to remain open. For further information, refer to the section Allowing network connections during isolation.
-
New incoming and outgoing connections are no longer possible, except for connections necessary for communication with agent handlers (HTTPS port 443 for an agent greater than or equal to 2.7.1 or TCP port 17000 for an agent less than 2.7.1) and authorized connections. For further information, refer to the section Allowing network connections during isolation.
You can shut down isolated computers, as their isolated status will be kept when they are restarted.
NOTE
You can move isolated agents from one agent group to another. They will retain their isolation status.
Conversely, isolated agents automatically lose their isolation status in the following cases:
- If you request the downgrade of the agent to a version below 2.5.3,
- if you disable the Networks feature in the agent group settings.
You can monitor isolated agents through the Isolation dashboard and panel.
The Isolated agents diagram in the dashboard shows the number of agents isolated from the network and their isolation status: Isolated, To be isolated, Undoing isolation pending. For further information, refer to the section Checking agent status.
You can perform the following actions in the Responses > Isolation panel:
-
View the list of agents affected by the isolation.
-
Undo isolation of the agents. For further information, refer to the section Undoing isolation.
-
Create Yara and IoC scan tasks directly on the affected agents (Threat hunting button). For further information, refer to Analyzing behavior on user workstations.
-
Determine the network connections allowed during isolation (Settings tab). For further information, refer to the section Allowing network connections during isolation.
By default, isolation blocks all network connections on the computer using TCP and UDP protocols, except for DNS and DHCP requests on ports 443 (agent version 2.7.1 or higher) or 17000 (agent version lower than 2.7.1) in order to allow communication with SES Evolution agent handlers.
The Settings tab in the Isolation panel makes it possible to allow other connections during isolation, by defining exception rules.
To add rules:
-
Click on Edit in the upper banner.
-
Click on Add an authorized network connection.
-
Enter a description in the window that appears.
-
Specify the path or SID of the application to be authorized.
-
Configure the settings that follow and click on OK.
The rule will be created. It applies to all agents regardless of their agent group. -
Click on Save in the upper banner.
-
Deploy the environment from the Security > Deployment menu.
All changes made in this tab will be logged in System logs.
This list of exceptions takes priority over the network rules in the security policy. It does not have priority over the agent's self-protection network rules.
Any administrator with the necessary permissions can stop the isolation of a computer, even if another administrator isolated it.
As soon as the agent receives the request to undo isolation, TCP and UDP connections will be restored.
To stop isolating a computer, go to the Isolation panel, General tab:
-
On an agent's line or on a selection of agents, right-click > Undo isolation for the selection,
-
Enter a comment,
-
Check the selection of agents,
-
Click on Undo isolation.
Maintenance mode
-
Agents in maintenance mode can receive requests to isolate or undo isolation.
-
The agent's maintenance mode can be enabled on computers that are under isolation. The computers will retain their isolation status.
For further information on Maintenance mode, refer to the section Enabling Maintenance mode.
Stopping the agent
When a computer is isolated and you request to stop the agent via a challenge:
-
Network connections will be allowed again,
-
The agent will still be seen as isolated in the administration console, and network connections will be shut down again at the end of the challenge.
When an agent is being stopped via challenge and you make an agent isolation request:
-
The isolation request will be applied, but will not take effect until the challenge has ended.
For more information on stopping agents, refer to the section Stopping an agent.
Automatic deletion of agents
The configuration for the automatic deletion of offline agents also applies to isolated agents. Agents are deleted by default after 30 consecutive days of staying offline.
For further information, refer to the section Monitoring agents in real time.
Uninstalling agents
Isolated agents can be uninstalled. In this case, if an agent is connected to its agent handler, the administration console will no longer consider it isolated from the network.
If it is disconnected from its agent handler when it is uninstalled, the management console will still consider it isolated. It will be automatically removed by the mechanism that automatically deletes offline agents.
Starting up in safe mode
Network connections will not be shut down when an isolated computer is restarted in networked safe mode.
Computer disconnected from the corporate network
When a computer is no longer on the internal corporate network, as in the case of a mobile user for example, it cannot receive requests to isolate or undo isolation. The request will be applied when the computer is reconnected to the network.
Temporary web access
Temporary web access has a lower priority than network isolation.
When you request to isolate a computer with temporary web access :
-
Temporary access will be shut down and the computer will be isolated,
-
Temporary access will resume when isolation is undone, with the remaining time before isolation if the computer is not restarted during its isolation,
-
Temporary access will not resume when isolation is undone if you restart the computer during isolation.
For more information on temporary web access, refer to Allowing temporary web access.