Allowing temporary web access
The temporary web access mechanism allows a user to bypass Network protection rules in the policy, with specific applications and for a duration that you can set.
When this duration expires, new connections will be blocked once more, according to the rules in the security policy. However, applications for which connections were opened during temporary web access will not be shut down, and existing connections will not be interrupted.
EXAMPLE
Temporary web access makes it possible to manage mobile users who want to log in to their corporate network via a VPN tunnel from unsecure networks. When these workstations are outside the corporate network, the security policy that applies may prevent communications over the network. Temporary web access therefore allows them to temporarily unblock the VPN client and browser upon users’ request, so that the client can log in to the corporate network and switch to the internal security policy. Users will then be able to use their workstations normally.
Temporary access only needs to be allowed on one of the policies assigned to an agent group for this feature to be available on the agent side.
The temporary web access feature is available only in protection rule sets.
This feature is disabled by default. If there are several protection rule sets in your security policy, ensure that you enable the policy only for the set(s) in which you want to configure temporary web access, and arrange your rule sets in the right order in the policy. If you enable and allow temporary web access in a rule set near the top of the policy, this rule may overload and cancel the effect of the temporary web access configuration in the rule sets that follow.
- Application identifiers must be created beforehand for applications allowed to access unrestricted networks when temporary web access is enabled. For more information, refer to the section Creating application identifiers.
- The application firewall must be enabled in the configuration of agent groups:
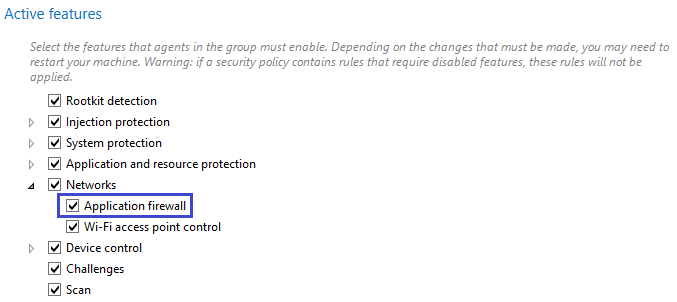
- Select the Security > Policies menu and click on a policy.
- Select a protection rule set.
- Click on the Networks > Temporary web access tab.
- If you are in read-only mode, click on Edit in the upper banner.
- Enable the feature.
- Allow temporary web access.
- Select one or several application identifiers allowed to access the web. These applications will be allowed to connect to all IP addresses over all ports.
- Choose the maximum duration of web access.
- Choose the number of access authorizations. The counter will be reset when the user restarts the workstation.
- If necessary, create a shortcut on the user’s desktop. Users have several ways to enable temporary access on their workstations. For more information, see the next section.
- Click on Save at the top right of the window to save changes.
The SES Evolution agent provides the user with several ways to enable temporary web access:
- A Start temporary web access button in the
 tab of the agent's interface,
tab of the agent's interface,
- A pop-up menu that appears by right-clicking on the agent's
 icon in the taskbar.
icon in the taskbar. - A desktop icon, if the feature is enabled in the temporary web access settings,
- The command EsGui /GrantWebAccess to be inserted into a script, for example.
When the user’s temporary web access is in progress, a banner at the bottom of the agent's interface indicates the remaining time.
The user can stop temporary access:
- via the agent's interface,
- via the pop-up menu of the agent's icon in the taskbar.