Configuring a policy-based mesh topology
Example of a scenario:
A company has its headquarters and two other sites in England and one site abroad. Every site has its own Research and Development department and the four R&D sub-networks need to share information. Every site is protected by a firewall managed by the SMC server.
The authentication method selected is X509 certificate authentication.
The certification authority that issues certificates can be found on one of the SNS firewalls, such as the headquarters, for example, or it may be an external authority.
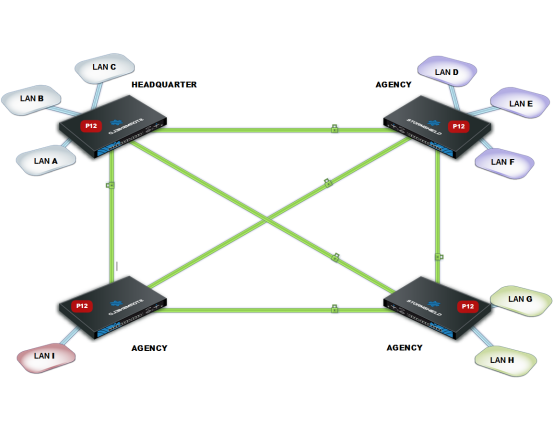
To configure VPN tunnels between the four sites, follow the steps below.
To import or declare a certificate in PKCS#12 or PEM format from the SMC server web interface, refer to the section Importing a certificate from the server's web interface.
Certificates can also be imported from the command line interface. Refer to the section Importing a certificate from the command line interface
On the SMC server, you need to declare the certification authorities to be trusted by the firewalls that SMC manages.
In order for the topology to be deployed, the SMC server must know the certification authorities' entire chain of trust. For further information and to find out how to add certification authorities, refer to the section Managing certificates and certification authorities.
You must give the SMC server the addresses of the distribution point(s) of the Certificate Revocation List (CRL) that firewalls would use for each declared authority. They can be external or you can also set SMC as a distribution point.
Setting external distribution points
- In the properties of a certification authority, click on the List of CRL distribution points tab.
- Add the addresses of the external distribution point(s) for the certificate revocation list.
Setting SMC as a distribution point
The SMC server can act as a CRL distribution point for SNS firewalls:
- In the properties of a certification authority, click on the SMC as CRL distribution point tab.
- Select the CRL file (.pem or .der format) to import onto the server.
The SMC server then makes the file available for the SNS firewalls on the URI
smc://[SMC address]:[SMC port]/api/certificates/authorities/[uuid CA].crl.
As the CRL has an expiry date, it must be regularly imported onto the SMC server.
As firewalls can contact the SMC server through several addresses (they are specified in the connecting package), enter one URI for each address.
You can also import a CRL on the SMC server in command line, with the commandsmc-import-crl. - In the List of CRL distribution points tab, add the URI address to the list. The CA UUID is showed in the SMC URL address as well as in the example provided in the tab.
- Go to the Objects menu on the left.
- Create as many objects as the number of traffic endpoints or hosts that will be included in your VPN topology, i.e., four objects in our example.
These may be Network, Host or Group objects.
IMPORTANT
It is not possible to use groups containing variable objects in VPN topologies. VPN tunnels configuration would be invalid.
You now have all the necessary elements for configuring your VPN topology.
- In Configuration > VPN topologies, click on Add a VPN topology at the top of the screen and select Mesh.
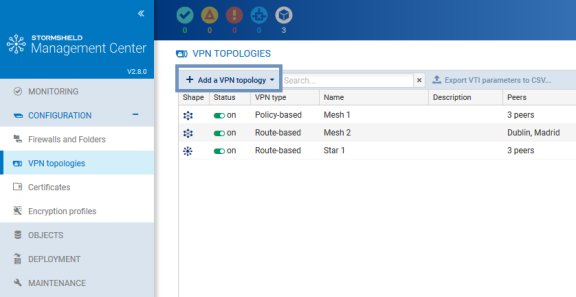
- In the window that opens, select Policy-based VPN and click on Create the topology.
- Enter a name. A description is optional.
- Select X.509 certificate authentication and select the certification authorities that issued the certificates for the firewalls involved in the VPN topology. If an authority’s CRL has expired, a warning appears in the list of the VPN topologies menu.
- If you wish to do so, indicate a post-quantum pre-shared key ID and its password. Such keys provide protection particularly from "store now, decrypt later" attacks. For more information, refer to the SNS User guide. This feature is available only when X.509 certificate authentication is used on firewalls in at least version 4.8.0, and only with IKEv2.
- Select the encryption profile. The SMC server offers pre-configured profiles. Create your customized profiles in Configuration > Encryption profiles. Refer to the SNS User guide for more information on encryption profile options.
- Select your topology peers. You can select connected or offline firewalls. You can also select firewalls that have never connected, on the condition that you have set a default custom or dynamic contact address in the System > IPsec VPN tab in the firewall settings.
You need to hold write access privileges on the firewalls that you wish to select as peers. For more information, refer to the section Restricting folder administrators' access privileges. - Select the traffic endpoints associated with each of your peers. For further information on the Contact address and Local address settings, refer to the sections Defining the contact IP address of firewalls for VPN topologies and Selecting the output interface of firewalls for VPN topologies.
- Click on Apply.
- Deploy the configuration on the firewalls involved in the topology. The VPN configuration belongs to the firewall's global policy.