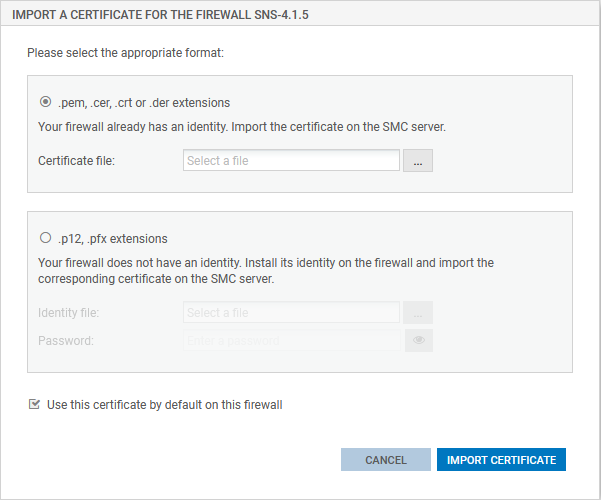
Importing or declaring a certificate for a firewall
A DER or PEM certificate is required for each firewall that is part of a VPN topology using .X509 authentication.
A PKCS#12 identity can be installed on the firewall from the SMC server, which retrieves the corresponding certificate.
The certificate can be imported on the SMC server from the server's web interface or from the command line interface. Several certificates may be imported for a single firewall.
Certificates used by an SNS firewall can also be declared on SMC without having to import them on the server (SCEP or EST protocols).
You need to hold write access privileges on the firewall to perform these operations. For more information, refer to the section Restricting folder administrators' access privileges.
Certificates can be imported for a firewall from several panels in the web administration interface.
- In the Monitoring > Firewalls menu, double click on a connected firewall.
- In the System > IPsec VPN tab, select the By file option.
- Click on Import a new certificate. The link will take you to the Configuration > Certificates menu.
- Scroll over the name of the firewall in the Firewall column and click on the
 icon. For further information regarding the Certificates menu, refer to Managing certificates and certification authorities.
icon. For further information regarding the Certificates menu, refer to Managing certificates and certification authorities.
-or-
- In the Monitoring > Firewalls menu, scroll over the name of a connected firewall and click on the
 icon.
icon.
-or-
- In the Configuration > Certificates, click on Import certificate at the top of the grid. For further information regarding the Certificates menu, refer to Managing certificates and certification authorities.
-or-
- During the configuration of a VPN topology, when choosing peers, click on the
 icon on the line of a firewall. For more information, please refer to the section Creating policy-based VPN topologies.
icon on the line of a firewall. For more information, please refer to the section Creating policy-based VPN topologies.
The option Use this certificate by default on this firewall allows you to select the certificate to be used for VPN negotiations. There can only be one default certificate for each firewall. To change the default certificate later, refer to the section Importing or declaring a certificate for a firewall.
- To import a certificate from the command line interface, connect to the SMC server via the console of your hypervisor or in SSH.
- Enter the command
smc-install-certificate
TIP
Display help using the option --help:
Three of these options are mandatory:
- --certificate: path of the certificate (.p12 or . pfx) to be installed,
- --firewall: name of the firewall on which the certificate needs to be installed,
- --password: password that protects the certificate if a .p12 file is used.
The operation will be saved in the log file/var/log/misc/install-certificate.log.
Import the certificate for the active node of the cluster.
The SMC server then synchronizes both nodes of the cluster.
- Situation: You have selected the certificate and entered the password but the Import button remains grayed out.
- Cause: When running a script or deploying a configuration, you will not be able to import any certificates for any firewalls.
- Solution: Wait for the script to finish its run or for the configuration to be fully deployed.
- Situation: When you import a certificate on a firewall, the SMC server returns the error "Insufficient privileges".
- Cause: You are unable to import a certificate on a firewall on which a session has been opened either directly or via SMC.
- Solution: Log off from the firewall and attempt to import the certificate again.
- The file exceeds the maximum limit allowed, which is 1 MB.
- The file format is neither .p12 nor .pem. The SMC server only supports .p12 or .pem files.
- You have entered the wrong password.
Certificates used by an SNS firewall can also be declared in SMC by indicating their subject and issuer. You therefore do not need to import the certificate on the server.
This feature may be useful whenever the firewall generates its own keys and obtains a certificate automatically from the certification authority via SCEP or EST.
There can only be one certificate obtained via SCEP or EST for each firewall.
- In the Monitoring > Firewalls menu, double click on a connected firewall.
- In the System > IPsec VPN tab, select By subject and issuer names and enter the corresponding information.
To enable the renewal of expired certificates that were obtained via SCEP or EST, on the SMC server, indicate the address of an SCEP or EST server in the panel of properties of a certification authority. For further information, refer to the section Managing certificates and certification authorities.
If you have imported several X509 certificates for a firewall, to find out which certificate is used by default in VPN topologies:
- Go to Monitoring > Firewalls, and double click on the row of the firewall in question.
- Open the System > IPsec VPN tab. The certificate used by default is the certificate selected in the Certificate for authentication section.
To change the certificate used by default, select another certificate from the drop-down list or import a new certificate.
You cannot delete the certificate used by default if it is in use in a VPN topology.