Restricting folder administrators' access privileges
SMC can segment the administration of your firewall pool by assigning different administrators to separate firewall groups. To do so, you can restrict an administrator's write access to a firewall group, based on the folder tree available in SMC. By segmenting administration, a perimeter can be defined for each administrator, thereby increasing security on your firewall pool.
EXAMPLE
If your firewall pool extends across several countries or continents, you can choose to assign a different administrator for each country or continent. Individual administrators can then manage only firewalls in the folder corresponding to their zone. They can also look up the configuration of other firewalls and of the SMC server in read-only mode.
Only the super administrator can restrict other administrators' write access privileges to certain folders.
The super administrator can then define two administrator profiles that hold write access privileges:
| General administrator |
|
| Folder administrator |
|
For more details on administrator profiles, as well as the implications and limitations of restricting access privileges to folders, refer to the section Managing administrators from local and external directories and the sections below.
The super administrator selects the folder(s) on which folder administrators hold write privileges. This means that the super administrator gives the administrator full write access to these folders, any sub-folders and the firewalls that they contain, as well as future sub-folders or firewalls.
The folder administrator can always view in read-only mode the configuration of firewalls outside their administration perimeter.
To restrict an administrator's privileges:
-
Go to Maintenance > SMC Server > Administrators.
-
Double-click on the row of the administrator.
-
In the Folders drop-down list, select the folder(s) that the administrator will be able to manage.
-
Apply changes.
In the firewall monitoring view, folder administrators see only the firewalls in their administration perimeter by default, meaning the firewalls that belong in the folders to which they have write access.
To display all firewalls, click on See read-only folders.
Folder administrators can create configuration items (objects, rules, QoS queues, etc.) and use them to configure the firewalls that they manage. They can also use all the configuration items available in SMC, and which have been added by other administrators.
However, they cannot modify or delete these items if they are used in the configuration of firewalls that are not in their administration perimeter.
To create, modify or delete a VPN topology, folder administrators must hold write access privileges to all firewalls included in the topology.
Otherwise, i.e., if the peers from the same topology are firewalls that have been organized in several folders managed by different folder administrators, only a general administrator can create, modify or delete the topology.
Write access privileges to the folder prevail over write access privileges to a topology. As such, folder administrators retain permissions to configure firewalls to which they have write access, even if these firewalls are part of a topology to which the administrators do not have full access.
EXAMPLE
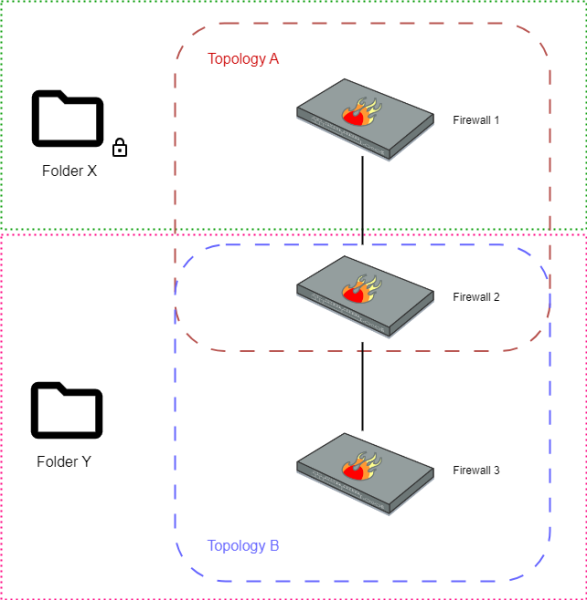
In this example, firewall 1 is organized in folder X, and firewalls 2 and 3 are organized in folder Y. The administrator of folder Y cannot modify topology A as it includes firewall 1, on which the administrator does not have write access privileges. However, the administrator retains write access privileges on firewall 2, although it is part of topology A.
Folder administrators cannot perform the following operations on the general SMC configuration:
-
Adding or changing global custom properties on firewalls,
-
Importing objects via a CSV file,
-
Changing the default VTI network pool in VPN topologies,
-
Loading and deploying older configurations,
-
Enabling or modifying the consistency check for “Diffusion Restreinte (DR)” mode,
-
Entering or changing a shortcut to the Stormshield Log Supervisor (SLS) server,
-
Adding an SNS CLI script or an attachment to a script,
-
Changing the settings of the Active Update server,
-
Creating API keys with write privileges to access the public SMC API.