Controlling network access
This protection is used to control access to incoming and outgoing networks by specific applications.
Access can be filtered by:
- Network events such as "bind", "accept" (server rule) and "connect" (client rule),
- TCP and UDP protocols,
- Specific ports,
- Specific IPv4 or IPv6 addresses.
It is not necessary to explicitly open communications between the SES Evolution server and the agents. Indeed, the agent's self-protection mechanism ensures that no security rule whatsoever can block these communications.
Network rules make it possible to:
- Protect a server by controlling access to the host,
- Force users of a service in the company to use a specific application to access a given network resource.
The following must be created beforehand:
- Application IDs for allowed applications or applications that cannot access the network. For more information, refer to the section Creating application identifiers.
- Network IDs for the IP addresses that you want to protect. For more information, refer to the section Creating network identifiers.
There are two types of rules; client rules and server rules.
- As part of a rule set that applies to workstations, client rules allow or do not allow applications to connect to remote resources (Remote field) by controlling the “connect” network event. They also make it possible to cater to specific subnets for example (Local field).
- As part of a rule set that applies to servers, server rules allow or do not allow applications to open ports and accept incoming connections (Local field) by controlling the "bind" and "accept” network events. They also make it possible to specify the source of connections (Remote field).
To create a network access rule:
- Select the Security > Policies menu and click on your policy.
- Select a rule set.
- Click on the Networks > firewall tab.
- If you are in read-only mode, click on Edit in the upper banner.
- Choose to add a Client network rule or a Server network rule by clicking one of the Add buttons. A new line is displayed.
- Choose the network IDs of the resources you want to protect in the left side of the rule:
- Local
 : Local resource affected by the rule. E.g., if the workstation has several network cards, you can specify which card is impacted.
: Local resource affected by the rule. E.g., if the workstation has several network cards, you can specify which card is impacted. - ELocal
 Local resource excluded from the rule.
Local resource excluded from the rule. - Remote
 : Remote resource affected by the rule. E.g., the internet.
: Remote resource affected by the rule. E.g., the internet. - Remote
 : Remote resource excluded from the rule.
: Remote resource excluded from the rule.
- Local
- In the Ports field, indicate the ports affected by the network rule. These ports are the destination ports for client rules and local ports for server rules.
- To add several ports at one go, separate them with commas. Example: 8080.8081.
- To add a port range, separate the first value and last value with a dash. Example: 80-90
- Leave the field empty to specify that all ports are concerned.
- Choose the TCP or UDP transport protocol, or both.
- In Default behavior, choose the behavior of each Connect, Accept or Bind network event:
- Accept (for server rules): allows or does not allow specified applications to receive incoming connections on the network resource(s) indicated,
- Bind (for server rules): allows or does not allow specified applications to open connections on the network resource(s) indicated,
- Connect (for client rules): allows or does not allow specified applications to connect to the network resource(s) indicated.
- Allow to allow the action by default,
- Block to block the action by default,
- Block and kill to block the action by default, and shut down the process that launched the action.
- Block, kill and quarantine to block the action by default, kill the process that triggered the action, and quarantine suspicious files. For more information, see the section Managing file quarantine.
- Ask for the user to be consulted.
- Skip behavior to ignore the subrule if the behavior is detected and move on to the next behavior.
- Skip rule to ignore the rule contained in this rule set and evaluate the next rule.
- Skip rule group to ignore the rules contained in the rule group and evaluate the next rule group or rule.
- Skip rule set to ignore all the rules contained in this rule set and evaluate the next rule set.
Protection rules can behave as follows:
- Click on + Add a specific behavior and choose the application identifiers of resource(s) that you want to exclude from the default behavior.
EXAMPLE
This is the client rule that can block connections from the network card on the unprotected network card to the internet and the protected network over ports 80, 443 and 8080 and TCP. Only the web server specified in the protected network can be accessed.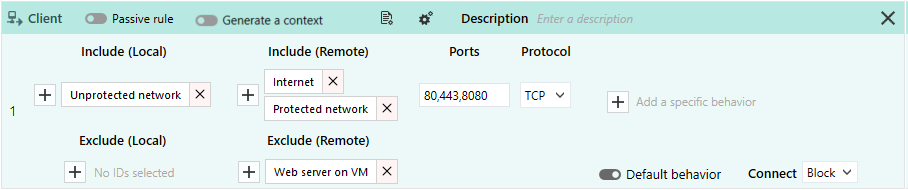
- In the upper banner in the rule, you can:
- If necessary, rearrange the order of the rules by clicking on
 when the cursor hovers the rule. Each rule displays its line number in the banner.
when the cursor hovers the rule. Each rule displays its line number in the banner. - Disable rule. For more information, refer to the section Disabling security rules.
- Indicate the intent of the rule, according to predefined categories:
Unclassified: unclassified rule.
Nominal: non-blocking rule conforming to nominal application behavior.
Protect: blocking rule with a high log severity level.
Protect silent: blocking rule with a severity level below the log thresholds displayed by default on the agent and console. Protects access to resources deemed sensitive, even if carried out by programs with no malicious intent. As there may be many such programs, a rule with too high a log severity could trigger massive log generation.
Detect: non-blocking audit rule or passive rule.
Context: rule used to build an attack graph.
Syslog: rule triggering logs sent exclusively to a Syslog server.
Watch: rule for monitoring behavior in order to fine-tune the security policy or gain a better understanding of technical events occurring in the pool.
- Enter a description to explain what this rule aims to achieve.
- Make the rule passive. Passive rules behave like standard rules but do not actually block any actions. The agent only generates logs that indicate which actions security rules would have blocked.
Use this mode to test new restriction rules, determine their impact, and make the necessary adjustments before disabling Passive rule mode. For further information on testing rules and policies, refer to Testing security policies. - Indicate whether the rule must generate a context when it is applied. By default, if a rule generates Emergency or Alert logs, it will generate a context, but you can disable this feature. In case of mass generation of similar logs, the context is not generated. For more information on mass log generation, refer to the section Monitoring SES Evolution agent activity.
- Adding a comment.
- Select the log settings that this rule will send.
- Specify whether an action must be performed when a log is sent for this rule. You can request that a script be run and/or that a Yara or IoC scan be triggered. You can also request that a notification be displayed on the agent, provided that it is associated with a an Alert or Emergency level blocking log.
- Deleting the rule.
- If necessary, rearrange the order of the rules by clicking on
- Expand the Classification in logs part to indicate the intent of the suspected attack when the rule applies, along with the tags for associating the rule with the MITRE repository. This information is then visible in the logs generated by the rule. For more information, see Classifying attacks according to the MITRE repository.
- Click on Save at the top right of the window to save changes.