Configuring actions triggered by rules
When a protection rule blocks an operation performed on an SES Evolution agent, it will be logged, and you can determine the severity and destination of the log.
If you want it to, when this log is generated, it can trigger other actions on the agents in question. Various types of actions are possible:
- Show a notification on the agent. This notification will appear at the bottom right of the screen, indicating that a prohibited action was blocked by a protection rule.
- Run custom scripts.
- Run a Yara or IoC scan. For more information, refer to Running Yara scans and Searching for indicators of compromise
This action is available only for rules in which processes or files have been logged. It does not apply, for example, to Devices and ARP Spoofing rules.
EXAMPLE
This feature may be useful in triggering an antivirus analysis the moment the incident is logged, or it can move a dangerous file to a specific folder. Launching a Yara or IoC scan makes it possible to identify malware, for example.
- Select your security policy in the Security > Policies menu, then select the set of rules. The main page of the rule set appears.
- Click on the tab of the rule that you want to modify.
- If you are in read-only mode, click on Edit in the upper banner.
- In the banner at the top of the rule, click on
 . The window Action when logs generated appears.
. The window Action when logs generated appears. - Enable a notification on the agent, if you wish to, for every time this rule triggers a log. This feature is available only for rules in Protection mode.
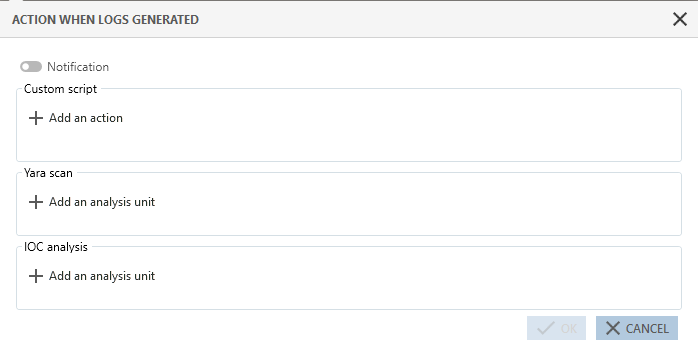
- If you wish to run a script whenever this rule generates a log, click on Add an action.
- Enter a name for the action in the Run custom script window.
- To the right of the Script field, click on + to add the script to run.
- In the Arguments field, specify the arguments to add when the script is run.
- In the Run in list, choose Local service because this is an account with restricted privileges. Do not choose Interactive session or System accounts unless absolutely necessary.
Do note that scripts cannot be run during interactive sessions on a server with several remotely connected users.
All scripts that were declared in SES Evolution appear in the Script list. Select an existing script and click on ![]() to view it or
to view it or ![]() to import a new version of the script.
to import a new version of the script.
- If you wish to run a Yara or IoC scan whenever this rule generates a log, click on Add an analysis unit in the relevant section.
- Click on one or several analysis units to select them, then close this window. For an IoC scan, only text or file name indicators can be used here.
- In the Action when logs generated window, click on Log settings to determine the severity and destination of the logs that the Yara or IoC rules generated.
- If necessary, select Shut down the processes detected to remove the dangerous processes, identified during the Yara or IoC scan, from the agent.
If the rule is part of an audit rule set, or if the rule is in passive mode, the processes will not be shut down even when this setting is enabled. - If the above option is enabled, select Quarantine if you also want to quarantine detected files. For more information, see the section Managing file quarantine.
- Click Validate.
For IoC scans activated when a log is generated, they can analyze only the element that triggered the rule. Scheduled or on-demand IoC scans are more precise as their settings make it possible to include or exclude the folder to scan. For more information, refer to Scheduling IoC scans and Running IoC scans on demand.
EXAMPLE
In a File rule that protects files located in C:\temp from being deleted, you configured an IoC scan when logs are generated, to search for "suspect_text" in files. If the user attempts to delete a file in C:\temp wiith PowerShell, the rule will apply and the IoC scan will be triggered, but only on the powershell.exe file and on the memory of the powershell.exe process.