Classifying attacks according to the MITRE repository
SES Evolution references in its logs the techniques and sub-techniques of attackers such as those listed and described in the MITRE ATT&CK® matrices and in the common vulnerabilities and exposures (CVE) published by the US organization MITRE. Thus, in the event of an attack, IT administrators can quickly identify it and take appropriate action.
This feature associates a security rule with an attack intent and tags.
This allows you to specify for each rule the type of attack that might be underway when the rule is applied. You can also specify a list of tags to automatically associate your SES Evolution rules with the MITRE repository.
The purpose of this feature is to rapidly provide administrators with information via the logs sent to the console when security rules are applied. They can then identify the possible attack underway on the pool by viewing its classification, and go directly to the URL of the MITRE technique or CVE. Tags can also reference vulnerabilities identified by Stormshield on its https://advisories.stormshield.eu/ website.
EXAMPLE
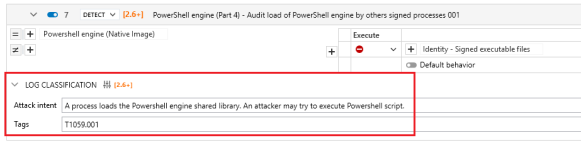
In each security rule, you can add an attack intent and tags corresponding to the techniques, sub-techniques or vulnerabilities referenced by MITRE. This information can be used to associate rules with known types of attack. They are displayed in logs when a rule is applied, making it possible to classify logs generated by agents and quickly identify the type of attack possibly underway.
In a security rule:
-
Expand the Classification in logs part.
-
Indicate the intent of the attack, i.e. specify the type of attack that may be underway if the rule is triggered. For example, for a rule protecting a USB stick in read mode, you could specify "Extract sensitive data via removable media".
-
You can specify up to 10 tags, referring to the MITRE ATT&CK® matrices, CVE vulnerabilities or Stormshield. For tag formats, see MITRE ATT&CK® matrices, common vulnerabilities and exposures (CVE) or the https://advisories.stormshield.eu/ site. For example T1546.001, CVE-2021-40444 or STORM-2023-022.
You can use the search field to filter rules by attack intent or tags.
Classification information is displayed differently on the SES Evolution agent and in the administration console.
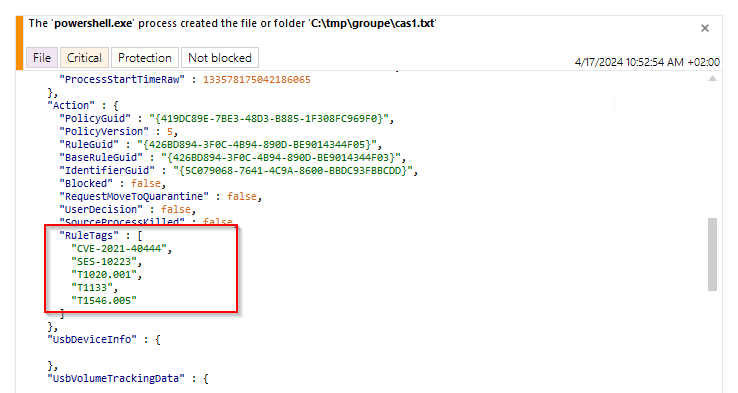
The Events tab of the agent interface lets you view the tags associated with the rule that generated a log in the Raw log display:
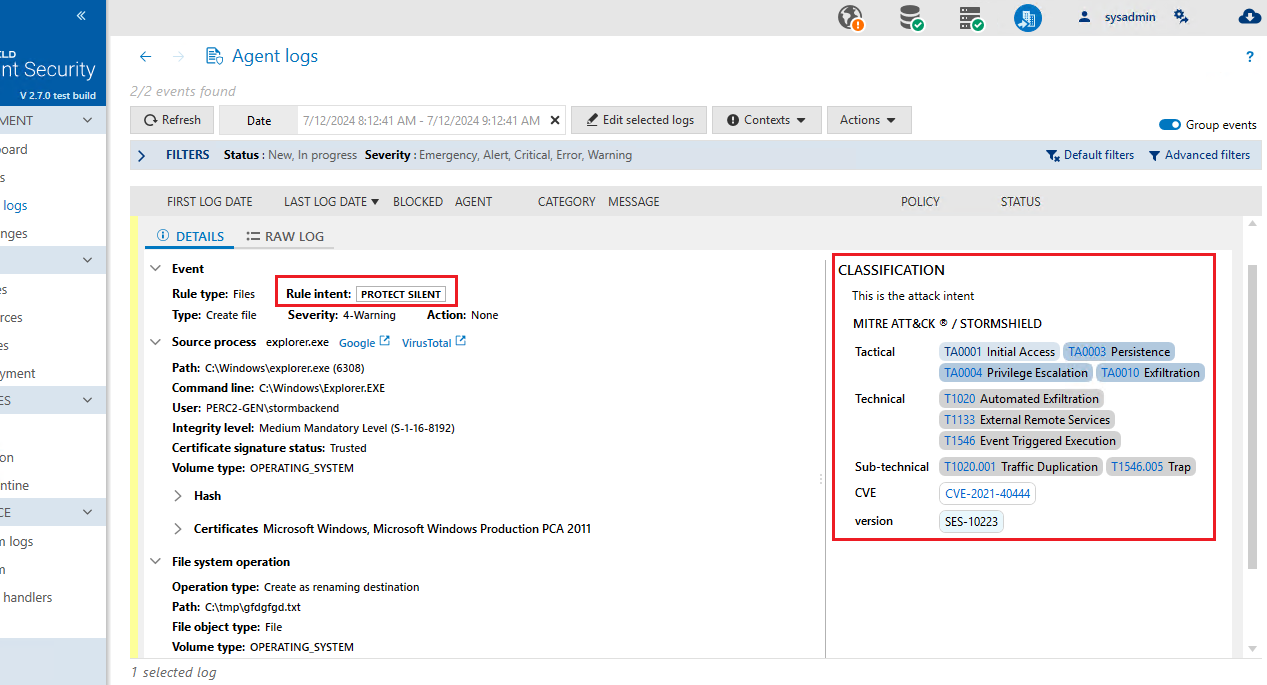
In the agent logs in the administration console, the Classification panel in a log's details displays the attack intent and the tags associated with the rule that generated the log:
-
Click on the MITRE and CVE tags to go directly to the details.