Configuring threat protection
The security rules that Stormshield provides include audit or protection rules that you can configure to protect your network from major attack classes that threaten workstations.
For more information on the attacks that SES Evolution thwarts, refer to the section Protection against various threats.
All threat protection rules are disabled by default. If there are several protection rule sets in your security policy, ensure that you enable the policy only for the set(s) in which you want to configure threat protection, and arrange your rule sets in the right order in the policy. If you configure threat protection in a rule set near the top of the policy, this rule may overload and cancel the effect of the threat protection configuration in the rule sets that follow.
- For Driver loading and Driver integrity audit rules, you must create a driver ID beforehand for every legitimate driver to ignore.
For more information, refer to the section Creating driver identifiers. - For all other protection types, application identifiers must be created beforehand for every application to be protected and for every approved application to be excluded from the protection rules.
For more information, refer to the section Creating application identifiers.
- Select the Security > Policies menu and double-click on your policy.
- Select the rule set in which you wish to add your rule.
The main page of the rule set appears. - Click the Threats > Built-in Protections tab.
Each protection type is a group of rules and can contain one or more rules. - If you are in read-only mode, click on Edit in the upper banner.
- Enable the desired rule by clicking on the
 button on the left and click on the arrow to display its contents.
button on the left and click on the arrow to display its contents. - In the Status field in Default behavior, there are three or four statuses for each protection mode. Select:
- Allow: SES Evolution does not block malicious actions and does not generate any logs.
- Detect only: As in audit mode, SES Evolution detects malicious actions without blocking them, and generates logs for the administrator. But unlike audit mode, this option stops evaluating the rules that follow, and ignores them.
- Block: SES Evolution blocks malicious actions and generates logs for the administrator.
- Block and kill: SES Evolution blocks malicious actions and shuts down the process that launched the action.
- Block, kill and quarantine SES Evolution blocks malicious actions, shuts down the process that launched the action and quarantines suspicious files. See Managing file quarantine.
For audit rules, the available actions are always Allow, which does not do anything, and Audit, which generates a log and evaluates the next rule.
- Click on + Add a specific behavior to add the IDs of the applications for which the protection must behave differently. In process hollowing for example, you can enable the protection by default, and disable it specifically for your internal applications, such as virtualization tools, that use this operating mode.
- In the upper banner in the rule, you can:
- If necessary, rearrange the order of the rules by clicking on
 when the cursor hovers the rule. Each rule displays its line number in the banner.
when the cursor hovers the rule. Each rule displays its line number in the banner. - Disable rule. For more information, refer to the section Disabling security rules.
- Indicate the intent of the rule, according to predefined categories:
Unclassified: unclassified rule.
Nominal: non-blocking rule conforming to nominal application behavior.
Protect: blocking rule with a high log severity level.
Protect silent: blocking rule with a severity level below the log thresholds displayed by default on the agent and console. Protects access to resources deemed sensitive, even if carried out by programs with no malicious intent. As there may be many such programs, a rule with too high a log severity could trigger massive log generation.
Detect: non-blocking audit rule or passive rule.
Context: rule used to build an attack graph.
Syslog: rule triggering logs sent exclusively to a Syslog server.
Watch: rule for monitoring behavior in order to fine-tune the security policy or gain a better understanding of technical events occurring in the pool.
- Enter a description to explain what this rule aims to achieve.
- Make the rule passive. Passive rules behave like standard rules but do not actually block any actions. The agent only generates logs that indicate which actions security rules would have blocked.
Use this mode to test new restriction rules, determine their impact, and make the necessary adjustments before disabling Passive rule mode. For further information on testing rules and policies, refer to Testing security policies. - Indicate whether the rule must generate a context when it is applied. By default, if a rule generates Emergency or Alert logs, it will generate a context, but you can disable this feature. In case of mass generation of similar logs, the context is not generated. For more information on mass log generation, refer to the section Monitoring SES Evolution agent activity.
- Adding a comment.
- Select the log settings that this rule will send.
- Specify whether an action must be performed when a log is sent for this rule. You can request that a script be run and/or that a Yara or IoC scan be triggered. You can also request that a notification be displayed on the agent, provided that it is associated with a an Alert or Emergency level blocking log.
- Deleting the rule.
- If necessary, rearrange the order of the rules by clicking on
- Expand the Classification in logs part to indicate the intent of the suspected attack when the rule applies, along with the tags for associating the rule with the MITRE repository. This information is then visible in the logs generated by the rule. For more information, see Classifying attacks according to the MITRE repository.
- Click on Save at the top right of the window to save changes.
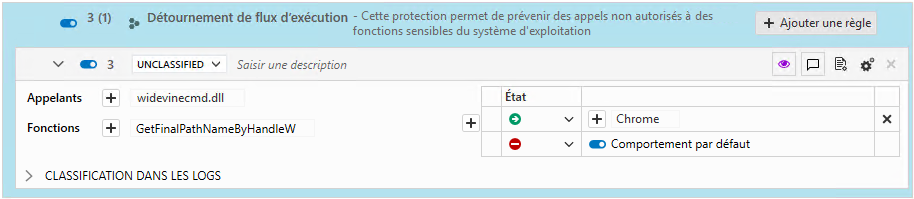
Case of protection against execution flow hijacking
To avoid false positives due to this protection, you can fine-tune it by declaring executables or DLLs (callers) and/or functions that can be authorized or blocked.
EXAMPLE
Some streaming platforms use DLLs and features to control user access. These can be considered illegitimate by the SES Evolution execution flow hijacking protection. Declare them in the rule to authorize them.
-
Follow the Configuring built-in protections procedure.
-
To the left of the rule, click Callers +, and enter the path to one or more executable resources or DLLs. The generic characters "?" and "*" are allowed in this field.
- Click on Functions + to select one or more functions.
To implement the example described above, you must:
-
Allow the Chrome process to access the GetFinalPathNameByHandleW function via the winevinecmd.dll DLL,
-
Block all other types of attempts (default behavior).
For more information, refer to the section Protection against various threats.
To enable and configure advanced protection:
- Select the Security > Policies menu and double-click on your policy.
- Select the rule set in which you wish to add your rule.
The main page of the rule set appears. - Click the Threats > Advanced Protections tab.
- If you are in read-only mode, click on Edit in the upper banner.
- Enable the desired rule by clicking on the
 button on the left and click on the arrow to display its contents.
button on the left and click on the arrow to display its contents. - In the Version drop-down list, indicate the version of the protection that you wish to run - either a version in particular or Always use latest version. If you are not using the latest version available, the indicator
 will appear to the right of the drop-down list. It also appears on a policy's general panel when at least one enabled advanced protection mode is not using its latest version.
will appear to the right of the drop-down list. It also appears on a policy's general panel when at least one enabled advanced protection mode is not using its latest version. - In the Status field, several statuses are available for each protection. Select:
- Allow: SES Evolution does not block malicious actions and does not generate any logs.
- Detect only: As in audit mode, SES Evolution detects malicious actions without blocking them, and generates logs for the administrator. But unlike audit mode, this option stops evaluating the rules that follow, and ignores them.
- Block: SES Evolution blocks malicious actions and generates logs for the administrator.
- Block and kill: SES Evolution blocks malicious actions and shuts down the process that launched the action.
- Block, kill and quarantine SES Evolution blocks malicious actions, shuts down the process that launched the action and quarantines suspicious files. See Managing file quarantine.
- In the upper banner in the rule, you can:
- Select the version of protection to run, either a specific version, or Always use the latest version. If you are not using the latest version available, the indicator
 will appear to the right of the drop-down list. It also appears on a policy's general panel when at least one enabled advanced protection mode is not using its latest version.
will appear to the right of the drop-down list. It also appears on a policy's general panel when at least one enabled advanced protection mode is not using its latest version. - Enter a comment.
- Select the log settings that this rule will send.
- Specify whether an action must be performed when a log is sent for this rule.
- Select the version of protection to run, either a specific version, or Always use the latest version. If you are not using the latest version available, the indicator
- Rules against WMI persistence, Malicious use of certutil, Environment discovery, Ransomware and Parent PID Spoofing each have specific parameters:
WMI Persistence Compatibility list: in this section, list the consumers that represent legitimate WMI events and which the protection mode must not block.
Malicious use of certutil Compatibility list: add here the IDs of applications which could use certutil.exe in legitimate cases and which should not be blocked by the protection. Environment discovery - Interval: indicate the interval in seconds (minimum five seconds) between the first command and the last command, and the interval after which discovery operations must be ignored.
- Compatibility list: in this section, add the IDs of applications allowed to run commands similar to discovery operations and which the protection mode must not block.
- Sensitivity: select the threshold above which the protection will be triggered.
Ransomware - Compatibility list: add here identifiers for legitimate encryption applications that should not be blocked by protection, such as StormshieldData Security.
- Sensitivity: select the threshold above which the protection will be triggered. With a Very low level, the protection mode will be triggered if a ransomware program encrypted at least 20 files within 3 seconds. With a Low level, the threshold will be 15 files, and with the Moderate level, 10 files.
If you enable this anti-ransomware protection mode, ensure that you also Enabling Windows shadow copies so that you can restore lost files if necessary.
For further information on restoration, refer to Managing ransomware attacks.
Protection against various threats Compatibility: here, add the IDs of applications that will be allowed to spoof parent processes without being blocked by the protection mechanism.
- Click on Save at the top right of the window to save changes.
NOTE
If subsequently, you want to change the version of an advanced protection, a deployment is required after the change is made.