Using certificates with TPM-protected private keys
This section explains how to use certificates with TPM-protected private keys in the configuration of an SNS firewall.
SSL/TLS decryption (web administration interface and captive portal)
This use case is exclusive to SNS 4.8.7 and higher versions.
The private key in the certificate presented by the web administration interface and the SNS firewall's captive portal can be protected by the TPM.
To check/change the certificate used:
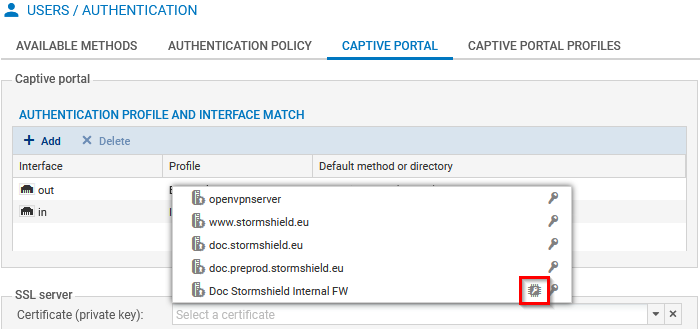
- Go to Configuration > Users > Authentication, Captive portal tab, SSL server section.
-
In the Certificate (private key) field, select the desired certificate. The
 icon indicates certificates with a TPM-protected private key.
icon indicates certificates with a TPM-protected private key. -
Apply changes.
The connection to the web administration interface will be lost. A warning message may appear when you go back to the authentication page. You can proceed to the website.
A backup certificate can be used to maintain access to the web administration interface if the private key of the selected certificate is protected, and access to the TPM is denied.
- On SNS 4.8.7 and higher versions of 4.8.x in factory configuration, this is a certificate that corresponds to the SNS firewall's serial number,
- On versions 5 in factory configuration, the certificate is self-generated for this access.
SSL VPN
This use case is exclusive to SNS 4.8.7 and higher versions.
The private key of the certificate that is presented by the SNS firewall SSL VPN service can be protected by the TPM.
IMPORTANT
If the private key of the selected certificate is protected, and access to the TPM is denied in the future, you will no longer be able to set up SSL VPN tunnels with the SNS firewall until the TPM has been resealed.
To check/change the certificate used:
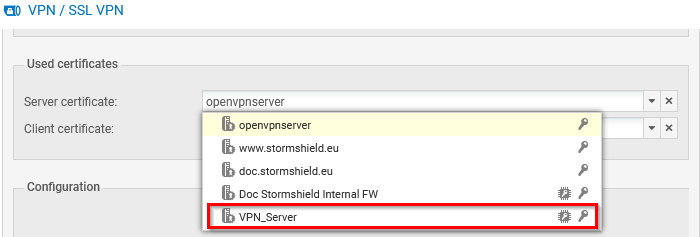
- Go to Configuration > VPN > SSL VPN, Advanced properties area, Certificates section.
-
In the Server certificate field, select the desired certificate. The
 icon indicates certificates with a TPM-protected private key. The selected certificate must be issued from the same certification authority as the one for the client certificate.
icon indicates certificates with a TPM-protected private key. The selected certificate must be issued from the same certification authority as the one for the client certificate. -
In the Client certificate field, you cannot select certificates that have TPM-protected private keys. This is because the private keys of such certificates must be available in plaintext (unencrypted) in the VPN configuration that is distributed to VPN clients.
-
Apply changes.
If you are using the Stormshield VPN SSL client in automatic mode, the VPN configuration will automatically be retrieved at the next connection. For all other use cases, the VPN configuration must be imported again (.ovpn file). For more information, refer to the technical note Configuring and using the SSL VPN on SNS firewalls.
IPsec VPN
The private key of the certificate that is presented to set up IPsec tunnels in a certificate authentication can be protected by the TPM.
IMPORTANT
If the private key of the selected certificate is protected, and access to the TPM is denied in the future, you will no longer be able to set up IPsec VPN tunnels with the SNS firewall until the TPM has been resealed.
To check/change the certificate used:
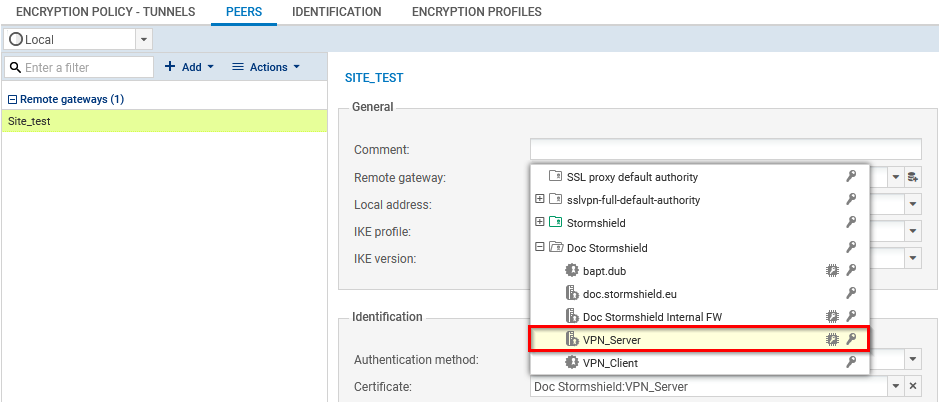
- Go to Configuration > VPN > IPsec VPN > Peers tab.
- In the grid, select the peer that was used in the VPN configuration.
-
In the Identification section, Certificate field, select the desired certificate. The
 icon indicates certificates with a TPM-protected private key.
icon indicates certificates with a TPM-protected private key. -
Apply changes.
Communications with the SMC server
This use case is exclusive to SNS 4.8.7 and higher versions.
The private key of the certificate that is used to communicate with the SMC server can be protected by the TPM.
IMPORTANT
As a reminder, if the private key of the certificate that is used to communicate with the SMC server is protected and access to the TPM is denied in the future, communications with the SMC server will no longer be possible until the TPM has been resealed.
For more information, see the section Firewall pools managed by an SMC server.
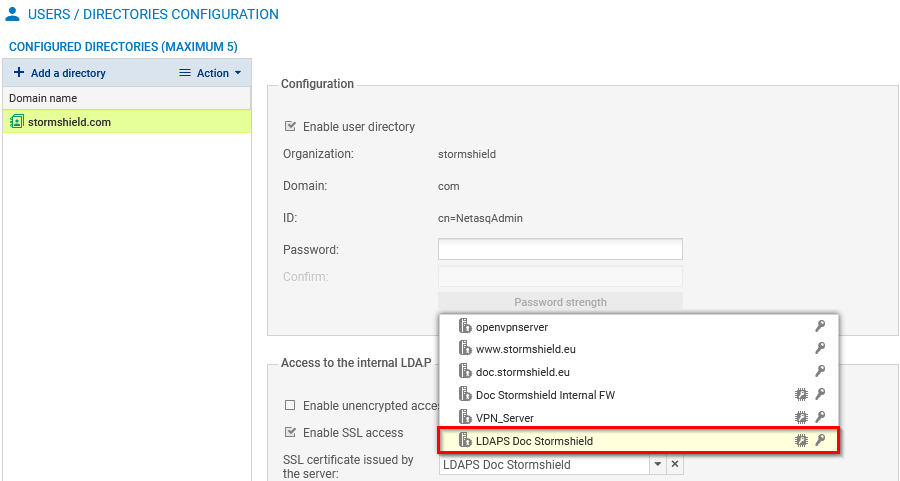
Internal LDAP
This use case is exclusive to SNS 4.8.7 and higher versions.
The private key of the certificate that is used for authentication to the internal LDAP directory can be protected by the TPM.
To check/change the certificate used:
- Go to Configuration > Users > Directory configuration.
-
Select the internal LDAP directory from the grid.
-
In Access to the internal LDAP, SSL certificate issued by the server field, select the desired certificate. The
 icon indicates certificates with a TPM-protected private key.
icon indicates certificates with a TPM-protected private key. -
Apply changes.
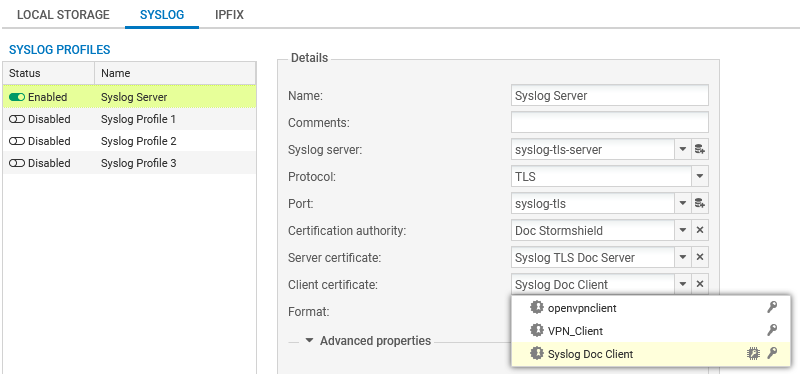
Sending logs to a TLS syslog server
This use case is exclusive to SNS 4.8.7 and higher versions.
The private key of the certificate that is presented by the SNS firewall to authenticate on the Syslog server can be protected by the TPM.
To check/change the certificate used:
- Go to Configuration > Notifications > Logs – Syslog - IPFIX, Syslog tab.
- Select the profile of the syslog server that you wish to modify from the grid. The details of the profile appear on the right.
- In the Certification authority field, select the certification authority (CA) that signed the certificates that the SNS firewall and Syslog server will present in order to authenticate mutually.
-
In the Server certificate field, select the certificate that the Syslog server will need to present in order to authenticate on the SNS firewall. You cannot select a certificate with a TPM-protected private key.
-
In the Client certificate field, select the certificate that the SNS firewall will need to present in order to authenticate on the Syslog server. The
 icon indicates certificates with a TPM-protected private key.
icon indicates certificates with a TPM-protected private key. - Apply changes.
- Ensure that the syslog server has the selected client certificate. You can export the certificate as a P12 file in Configuration > Objects > Certificates and PKI.