Initializing the TPM on SNS firewalls
This section explains how to initialize the TPM on an SNS firewall or TPMs in an SNS firewall high availability cluster.
From the web administration interface
The initialization process varies according to the version installed on the SNS firewall.
SNS in 4.8.7 and higher versions
-
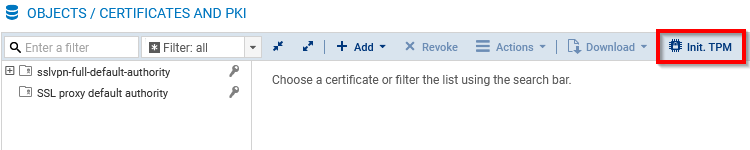
Go to Configuration > Objects > Certificates and PKI.
-
Click on Init. TPM.
-
If Secure Boot has not been enabled, a warning will appear. You are advised to enable Secure Boot before initializing the TPM, but this can be done later.
IMPORTANT
As a reminder, the integrity of the SNS firewall and its TPM will be compromised if Secure Boot is not enabled. -
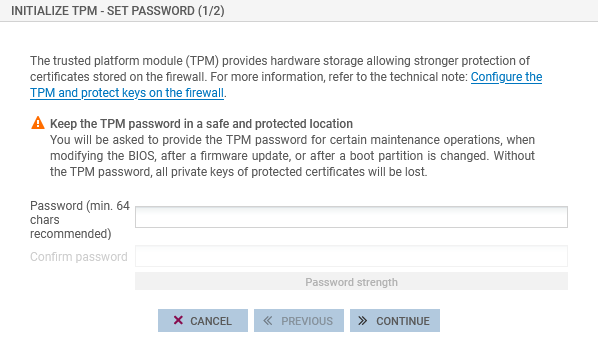
In the Set password window, set the administration password of the TPM, by following the recommendations in the section TPM administration password, then click on Continue.
-
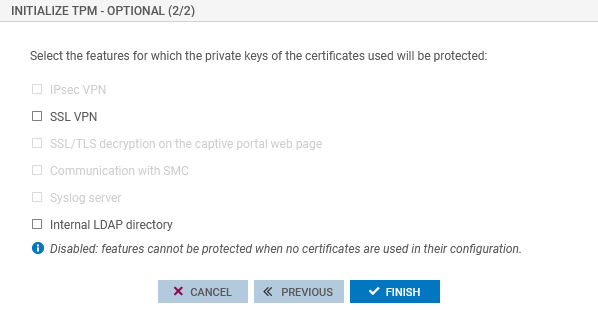
Select the features for which the private key of the certificate used will be protected. Features that do not use certificates in their configuration cannot be selected. You can also leave all checkboxes unchecked and protect private keys in SNS firewall certificates later.
-
Click on Finish.
The TPM is initialized and the mechanism that derives the symmetric key is used to generate the symmetric key, regardless of whether the SNS firewall is a member of a high availability cluster. If the SNS firewall is part of a high availability cluster, the TPM on the passive firewall will be automatically initialized.
SNS version 4.3.37 LTSB and higher 4.3 LTSB versions
-
Go to Configuration > Objects > Certificates and PKI.
-
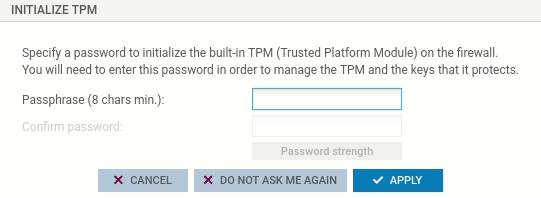
In the window to initialize the TPM, set the administration password of the TPM, by following the recommendations in the section TPM administration password. If the window does not automatically appear, check whether the TPM has already been initialized, or initialize it from the CLI console.
-
Click on Apply.
The TPM is initialized and the mechanism that derives the symmetric key is used to generate the symmetric key, regardless of whether the SNS firewall is a member of a high availability cluster. If the SNS firewall is part of a high availability cluster, the TPM on the passive firewall will be automatically initialized.
You then need to protect the private keys of certificates on the SNS firewall.
From the CLI console
-
Initialize the TPM on the SNS firewall with the command:
SYSTEM TPM INIT tpmpassword=<password> derivekey=<on|off>
-
Replace <password> with the desired administration password of the TPM, by following the recommendations in the section TPM administration password,
-
If the SNS firewall is a member of a high availability cluster, enter derivekey=on to use the symmetric key derivation mechanism.
-
-
If the SNS firewall is part of a high availability cluster, initialize the TPM on the passive firewall by running this command on the active firewall:
HA TPMSYNC tpmpassword=<password>
You then need to protect the private keys of certificates on the SNS firewall.
When a high availability firewall cluster has not yet been created
The TPM has not yet been initialized on either firewall in the cluster
- Configure the cluster (create the cluster and integrate the second SNS firewall).
- Refer to the procedures above on initializing the TPM on SNS firewalls.
The TPM is already initialized on the future active firewall in the cluster
SNS in 4.8.7 and higher versions
- Configure the cluster (create the cluster and integrate the second SNS firewall).
- Log out of the SNS firewall's web administration interface and log back in.
- A window will automatically appear, asking you to initialize the TPM on the passive firewall. Enter the TPM password in the relevant field.
- Click on OK.
SNS version 4.3.37 LTSB and higher 4.3 LTSB versions
-
From a CLI console, renew the symmetric key on the active firewall with the command:
SYSTEM TPM RENEW tpmpassword=<password> derivekey=on
- Replace <password> with the TPM password,
- As the firewall is a member of a high availability cluster, enter derivekey=on to use the symmetric key derivation mechanism.
All TPM-protected private keys will be decrypted, then encrypted again with the new symmetric key derived from the TPM password.
-
Initialize the TPM on the passive firewall by running this command on the active firewall:
HA TPMSYNC tpmpassword=<password>