Required operations following a BIOS update from a USB key
Once you have updated BIOS from a USB key, you will need to perform the operations below, in this order.
Configuring the password to access the UEFI control panel
If you had set a password to access the UEFI control panel before updating the BIOS, this password will be deleted. You will need to set it again, by following the instructions in the technical note Protecting access to the configuration panel of the UEFI on SNS firewalls.
Enabling Secure Boot
Secure Boot is disabled by default on SN3100 firewall models. If you had enabled it on your firewall before updating the BIOS, you will need to enable it again by following the instructions in the section Enabling Secure Boot in the SNS firewall’s UEFI in the technical note Managing Secure Boot in SNS firewalls' UEFI.
Sealing the TPM
If the TPM had been initialized on the firewall before updating the BIOS, you will need to seal it once again. This is because at the end of the BIOS update, trusted hash values have changed, preventing the decryption of protected private keys.
The reseal the TPM, follow one of the procedures below.
From the web administration interface
This use case is exclusive to SNS 4.8.7 and higher versions.
-
Log in to the SNS firewall’s web administration interface.
A window will appear automatically. In a high availability configuration, a window also appears if the TPM on the passive firewall needs to be sealed. If both members of the cluster are concerned, two windows will appear one after the other.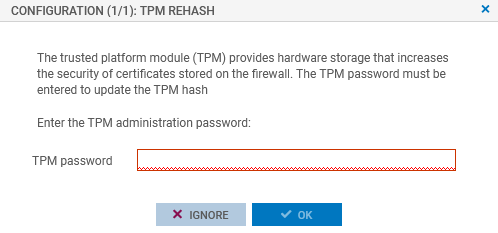
-
Enter the TPM password in the relevant field.
-
Click on OK.
From the CLI console
-
Seal the TPM on the SNS firewall with the command:
SYSTEM TPM PCRSEAL tpmpassword=<password>
Replace <password> with the TPM password.
-
If the SNS firewall is part of a high availability cluster, seal the TPM on the passive firewall with the command:
SYSTEM TPM PCRSEAL tpmpassword=<password> serial=passive