Hosts
From the menu tree, click on Hosts.
This window lists the connected hosts.
“Hosts” tab
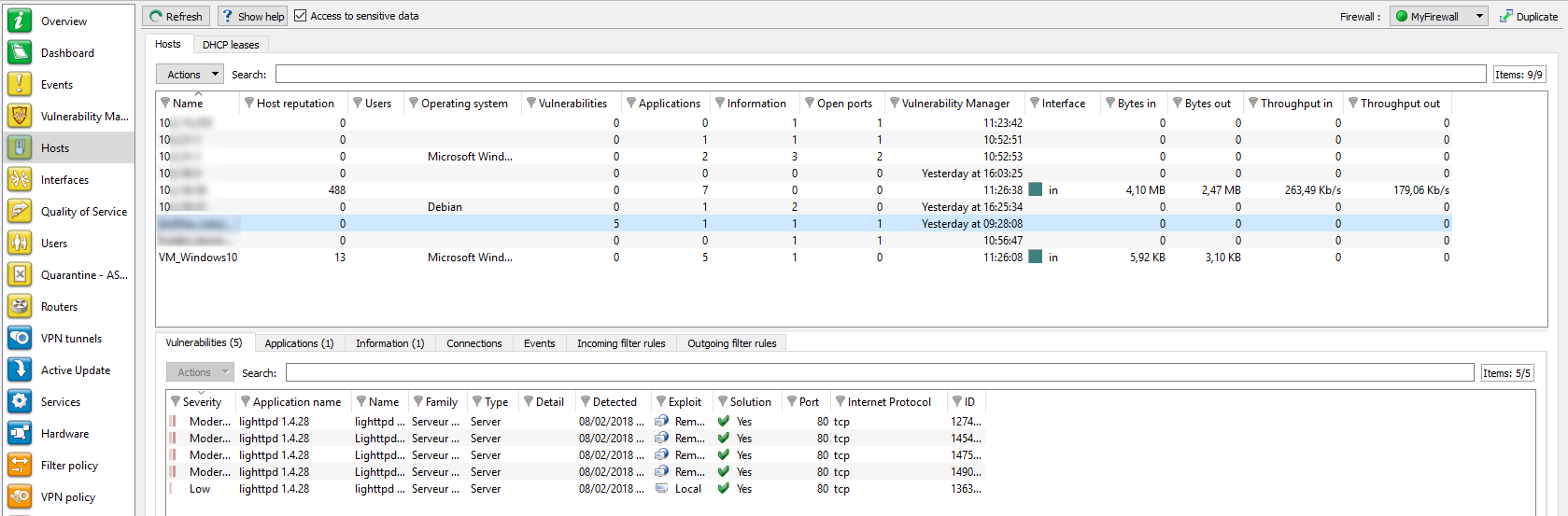
Figure 36: Hosts
This screen consists of 3 views:
- A view listing the hosts
- A view that lists the Vulnerabilities, Applications, Information, Connections and Events relating to the selected host
- A hidden help view that you can display by clicking on "Show help" (top left of the screen). This allows working around the selected vulnerability, if a solution exists.
"Hosts" view
This view shows all hosts detected by the firewall. Every row represents a host.
The "Hosts" view displays the following data:
|
Name |
Name of the sending host (if declared in objects) or IP address of the host (if not declared). |
|
Address |
IP address of the host. |
|
Users |
User logged on to the host (if any). |
|
MAC address |
MAC address of the host. |
|
Operating system |
Operating system used on the host. |
|
Vulnerabilities |
Number of vulnerabilities detected. |
|
Applications |
Number of applications on the host (if there are any). |
|
Events |
Number of detected events. |
|
Open ports |
Number of open ports. |
|
Vulnerability Manager |
Indicates the date and time of the last Vulnerability Manager event. |
|
Interface |
Interface to which the user belongs. |
|
Bytes in |
Number of bytes that have passed through the firewall from the sending host ever since the firewall started running. |
|
Bytes out |
Number of bytes that have passed through the firewall towards the sending host ever since the firewall started running. |
|
Incoming throughput |
Actual throughput of traffic to the host passing through the firewall |
|
Outgoing throughput |
Actual throughput of traffic from the host passing through the firewall |
| Host reputation | Host's reputation score This column will only contain data when host reputation management has been enabled and the selected host is a monitored host. |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- Remove host from ASQ,
- Reset Vulnerability Manager information,
- Send to quarantine,
- Manually set the Operating System
- Add the host to the Object base,
- Ping host,
- Traceroute to source host.
"Vulnerabilities" view
For a selected host, this tab will describe the vulnerabilities detected. Each vulnerability can then later be viewed in detail.
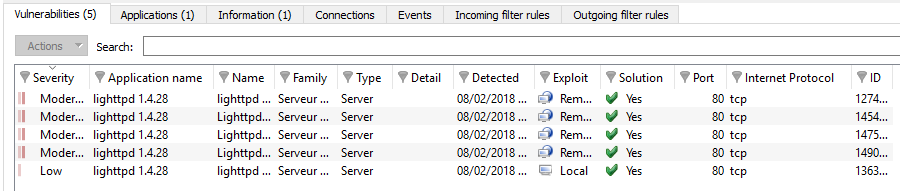
Figure 37: Hosts – Vulnerabilities
The "Vulnerabilities" view displays the following data:
|
Severity |
Indicates the level of severity on the host(s) affected by the vulnerability. There are 4 levels of severity: "Low", "Moderate", "High", "Critical". |
|
Name of the application |
Name of the software as well as its version, if available. |
|
Name |
Indicates the name of the vulnerability. |
|
Family |
Number of hosts affected. |
|
Type |
Software type (Client: the software does not provide any service – Server: the software application provides a service). |
|
Details |
One of 2 targets: "Client" or "Server". |
|
Assigned |
Family to which the vulnerability belongs. |
|
Exploit |
Access may be local or remote (via the network). It allows exploiting the vulnerability. |
|
Workaround |
Indicates whether a workaround exists. |
|
Port |
Date on which the vulnerability was detected. WARNING This refers to the discovery date and not the date on which the vulnerability appeared on the network. |
|
Internet Protocol |
Name of the protocol used. |
|
ID |
Vulnerability ID |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View hosts with the same vulnerability
"Application" view
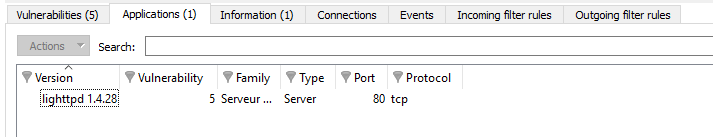
Figure 38: Hosts – Applications
For a selected host, this tab will describe the applications detected. It is possible to view applications in detail later.
The "Application" view displays the following data:
|
Version |
Name and version of the application. |
|
Vulnerability |
Number of vulnerabilities detected on the application. |
|
Family |
The software application’s family. |
|
Type |
Application type (Client: the software does not provide any service – Server: the software application provides a service). |
|
Port |
Port used by the application (if it uses one). |
|
Protocol |
Protocol used by the application |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View all hosts that use this application,
- View the vulnerabilities for this application,
- Impose a server application.
“Information” view
This tab provides information relating to a given host.
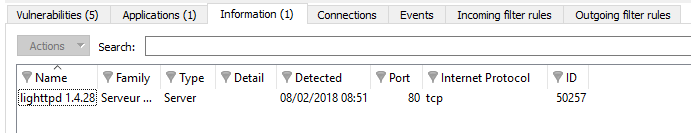
Figure 39: Hosts – Events
REMARK
The number of events is displayed in the tab’s name.
The "Information" view displays the following data:
|
Name |
Name of the detected OS. |
|
Family |
Family of the vulnerability that is likely to appear (Example: SSH). |
|
Type |
Application type (Client: the software does not provide any service – Server: the software application provides a service). |
|
Details |
Description of information. |
|
Assigned |
Date and time of detection. |
|
Port |
Number of the port on which the vulnerability had been detected. |
|
Protocol |
Name of the protocol used. |
|
ID |
Unique identifier of the vulnerability family. |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View hosts with the same information.
"Connections" view
Figure 40: Hosts - Connections
This view shows all connections detected by the firewall. Every row represents a connection. The "Connections" view displays the following data:
|
Time |
Indicates the date and time of the object's connection. |
|
Protocol |
Communication protocol used for the connection. |
|
Source |
Name of the object that connected to the selected host. |
|
Source MAC address |
MAC address of the object at the source of the connection |
|
Source port |
Number of the source port used for the connection |
|
Source interface |
Name of the interface on the firewall on which the connection was set up. |
|
Destination |
Name of the object for which a connection has been established. |
|
Destination MAC address |
MAC address of the object at the destination of the connection. |
|
Average throughput |
Average value calculated by the amount of data exchanged divided by the length of the session. |
|
Destination Port |
Number of the destination port used for the connection |
|
Destination interface |
Name of the destination interface used by the connection on the firewall. |
|
Data sent |
Number of bits sent during the connection. |
|
Data received |
Number of bits received during the connection. |
|
Duration |
Connection time. |
|
Router |
ID assigned by the firewall to the router used by the connection |
|
Router name |
Name of the router saved in the objects database used by the connection |
|
Policy |
Name of the policy that allowed the connection |
|
Rule |
ID name of the rule that allowed the connection |
|
Operation |
Identified command of the protocol. |
|
Parameter |
Operation parameter. |
|
Status |
This parameter indicates the status of the configuration corresponding, for example, to its initiation, establishment or closure. |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- Ping source host,
- Traceroute to source host,
- Ping destination host,
- Traceroute to destination host,
- Send connection to quarantine.
“Events” view
Figure 41: Hosts - Events
This view allows you to view all the events that the firewall has detected. Each line represents an alarm. The information provided in the “Events” view is as follows:
|
Date |
Date and time the line was recorded in the log file at the firewall’s local time. |
|
Logs |
Source of the event. |
|
Action (action) |
Action associated with the filter rule and applied to the packet (Examples: Block/Pass, etc.) |
|
Priority |
Determines the alarm level. The possible values are: 0: emergency 1: alert 2: critical 3: error 4: warning 5: notice 6: information 7: debug |
|
Config |
Name of the application inspection profile that reported the event. |
|
Policy |
Name of the SMTP, URL or SSL filter policy that raised the alarm. |
|
User |
Identifier of the user requesting authentication |
|
Protocol |
Protocol of the packet that set off the alarm. |
|
Source |
IP address or name of the object corresponding to the source host of the packet that set off the event. |
|
Source MAC address |
MAC address of the object at the source of the connection |
|
Src prt num |
Port number of the source (only if TCP/UDP). |
|
Destination |
IP address or name of the object corresponding to the destination host of the packet that set off the event. |
|
Destination Port |
Port requested for this connection (in letters, e.g.: http). |
|
Dst. port (num) |
Destination port requested for this connection (in numerals, e.g.: 80). |
|
Details |
Describes the event relating to the log. This description groups information from other columns in a single column. Example: if it is an alarm log, information such as whether the alarm is sensitive, the filter rule number and rule identifier will be indicated in this column or will otherwise be new columns in order to enable filtering. Please refer to the “Audit logs” technical note. |
| Source IP reputation |
Reputation category of the public IP address at the source of the traffic. This column will only contain data if this IP address is public and listed in the IP address reputation database. The possible values are: "anonymizer", "botnet", "malware", "phishing", "tor", "scanner" or "spam". |
| Source host reputation | Reputation score of the host at the source of the traffic. This column will only contain data when host reputation management has been enabled and the selected host is a monitored host. |
| Destination IP address reputation |
Reputation category of the public IP address at the destination of the traffic. This column will only contain data if this IP address is public and listed in the IP address reputation database. The possible values are: "anonymizer", "botnet", "malware", "phishing", "tor", "scanner" or "spam". |
| Destination host reputation | Reputation score of the host at the destination of the traffic. This column will only contain data when host reputation management has been enabled and the selected host is a monitored host. |
For the description of additional data available by column title, please refer to the section EVENTS.
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- Ping source host,
- Traceroute to source host,
- Ping destination host,
- Traceroute to destination host,
“Incoming filter rules” view
This view allows listing the incoming filter rules that can be applied to the selected host. Block rules are shown in red. Ignored rules are grayed out.
“Outgoing filter rules” view
This view allows listing the outgoing filter rules that can be applied to the selected host. Block rules are shown in red. Ignored rules are grayed out.
“DHCP leases” tab
This tab displays all hosts that have a lease in progress or which has ended and specifies the state of this lease. The information provided in the DHCP leases tab is as follows:
|
IP address |
IP address of the host. |
|
Name |
Name of the host that has a lease in progress or which has ended (if declared in objects) or host’s IP address otherwise. |
|
Status |
The status of the lease can be:
|
|
From |
Starting date and time of the lease assignment. |
|
Until |
Ending date and time of the lease assignment. This can be a date and time in the past or future |
|
MAC address |
Physical network identifier of the host with an ongoing or lapsed lease. |
REMARK
The leases assigned by reservation (static IP address reserved exclusively for a MAC address) are not displayed on this screen.
REMARK
When a new host logs on to a network, it will send a first request (DHCPDISCOVER) to the whole network to find out where the DHCP servers are. Upon reception, the DHCP server will pre-reserve an IP address and sends it to the host (DHCPOFFER). It is possible, however, that this host already uses the address range of another DHCP server. During this pre-reservation period (2 minutes), the IP address will no longer be available but will appear in the list as “free”. If many pre-reservations are made within a short period, the server may run out of available addresses while the screen continues displaying “free” addresses.
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- Display host,
- Ping source host,
- Traceroute to source host.