Events
The alarms generated by the firewall will appear in this window.
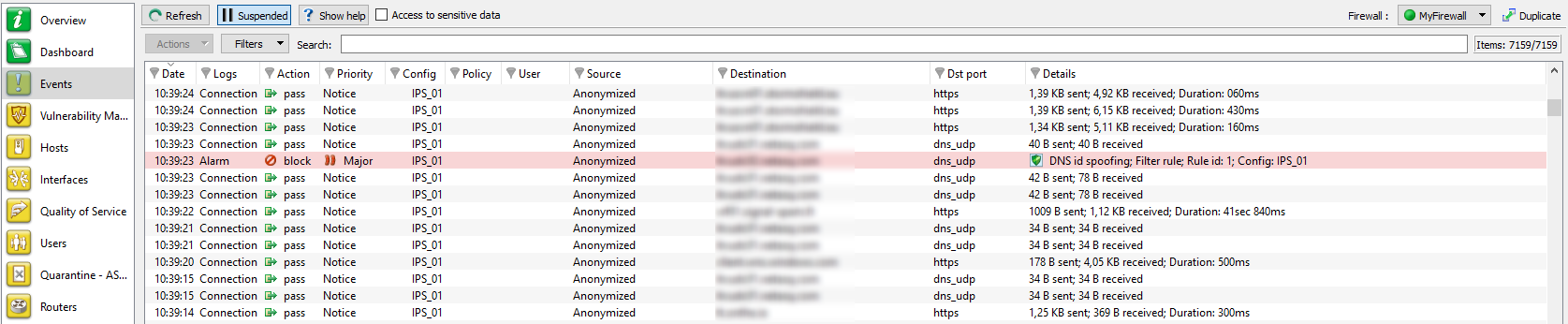
Figure 30: Events
In this module, the additional Activated/Suspended button allows switching the status of alarm refreshment. If this button is in a suspended status, the automatic refreshment will be disabled, making it easier to read logs.
When the Events menu in the tree on the left is selected, the data displayed by default are:
|
Date |
Date and time the line was recorded in the log file at the firewall’s local time. |
|
Logs |
Indicates the type of log. The possible types of logs are: Alarm, Plugin, Connection, Web, SMTP, FTP, POP3, Filter). |
|
Action |
Action associated with the filter rule and applied to the packet (Examples: Block/Pass, etc.) |
|
Priority |
Determines the alarm level. The possible values are:
|
|
Config |
Name of the application inspection profile that reported the event. |
|
Policy |
Name of the SMTP, URL or SSL filter policy that raised the alarm |
|
User |
Identifier for the authenticated user (ftp), e-mail address of the sender (SMTP), identifier for the user if authentication has been enabled (WEB). |
|
Source (src/srcname) |
IP address or name of the object corresponding to the source host of the packet that set off the alarm. |
|
Src. port (num) |
Source port number involved, displayed in digits. |
|
Destination (dst/dstname) |
IP address or name of the object corresponding to the destination host of the packet that set off the alarm. |
|
Destination Port |
Destination port number of the service or name of the object corresponding to the service port of the destination host if it exists and is requested for this connection. |
|
Details |
Describes the event relating to the log. This column groups some of the information gathered from the other columns. Example If an alarm log is concerned, information such as whether it was a sensitive alarm, the number of the filter rule, rule ID (already given in the columns "Sensitive alarm", "Rule" and "Rule ID") will be grouped in this column.
This column displays the icon that specifies the type of detection according to the categories Applications, Malware and Protections. |
Other available data includes:
|
Firewall (fw) |
Serial number or name of the firewall (if known) that caused the event. |
|
UTC Date (time+tz) |
UTC date (replaces the GMT) |
|
Start date (starttime) |
“Local” date at the start of an event. |
|
UTC start date (startime+tz) |
UTC date at the start of an event (a connection). |
|
Time zone (tz) |
Firewall’s time zone. |
|
Rule (ruleid) |
Number of the filter rule involved in the raised alarm. |
|
Protocol (proto) |
Protocol of the packet that set off the alarm. |
|
Connection group (groupid) |
Identifier that would allow tracking child connections. |
|
Source interface (srcif/srcifname) |
Name of the firewall interface on which the event was raised (source interface network card). |
|
Source address (src) |
IP address of the source host of the packet that set off the event. |
|
Source port (srcport/srcportname) |
Source port number of the service or the name of the object corresponding to the service port of the source host (only if TCP/UDP). |
|
Destination interface (dstif/dstifname) |
Network card of the destination interface. |
|
Destination address (dst) |
IP address of the destination host of the packet that set off the event. |
|
Authentication |
Authentication method used. |
|
Sensitive alarm (sensitive) |
Indicates whether an alarm is sensitive. This alarm is raised whenever the intrusion prevention system detects a sensitive packet and for which it has been configured in intrusion detection mode. If the alarm is sensitive, an icon in the form of an exclamation mark followed by “Yes” will appear. Otherwise, “No” will be indicated. When the alarm is blocked, the icon will be grayed out (it is disabled). NOTE Only protocol alarms can be described as “sensitive”. For alarms that are not in this class, the column will be empty. |
|
Copy (repeat) |
Indicates the number of an event’s occurrences within a defined period. |
|
Identifier (Id/alarmid) |
Indicates the number of the alarm. |
|
Context (class) |
Text indicating the category to which the alarm belongs (system, protocol, filter, etc). |
|
Alarm type (classification) |
Code (number) indicating the alarm category. This column also displays the type of detection according to the categories Applications, Malware and Protections. |
|
Caller |
VoIP: Indicates the caller |
|
Callee |
VoIP: Indicates the callee |
|
Duration |
Connection time in seconds. |
|
Sent |
Number of KB sent during the connection. |
|
Received (rcvd) |
Number of KB received during the connection. |
|
Operation (op) |
Identified command of the protocol.
|
|
Result |
Result of the operation in the protocol (example: 404 which indicates an error). |
|
Parameter (arg) |
Operation parameter. |
|
Category (cat_site) |
Web category of the requested website. |
|
Spam level (spamlevel) |
Spam level : 0 (Message not spam) 1,2 and 3 (spam) x (error while processing the message) and ? (the nature of the message could not be determined) if antispam has been enabled. |
|
Virus (virus) |
Indicates whether there is a virus (if the antivirus has been enabled). |
|
IP (ipproto) |
Internet protocol (tcp or udp). |
|
Media |
Type of traffic detected (audio, video, application,…) |
|
Message (Msg) |
Detailed description of the alarm. All commands sent by the client are found here. Sensitive information such as passwords is removed. |
|
ICMP code (icmpcode) |
ICMP code in the alarm logs. |
|
ICMP type (icmptype) |
ICMP type in the alarm logs. |
|
Packet |
Indicates the IP packet for which the alarm was raised. Right-clicking on this packet allows it to be viewed through a packet analyzer. The information displayed in this column shows the size of the IPv4 packets (value beginning with 45). The size of captured packets is 1536 bytes. WARNING
|
| Sandboxing | Indicates the result of sandboxing a file exchanged during the listed connection. The value of this result may be one of the following: Clean, Suspicious, Malicious, Unknown, Forwarded or Failure. |
| Hash |
Hash applied to the analyzed file and allowing it to be identified in various log files. |
| Sandboxing criticality |
This indicator will only be displayed when a file scanned by sandboxing has been deemed malicious. It will then be presented in the form of a score ranging from the detection threshold of a malicious file (set by default to 80) to 100. |
| Source IP reputation |
Reputation category of the public IP address at the source of the traffic. This column will only contain data if this IP address is public and listed in the IP address reputation database. The possible values are: "anonymizer", "botnet", "malware", "phishing", "tor", "scanner" or "spam". |
| Source host reputation | Reputation score of the host at the source of the traffic. This column will only contain data when host reputation management has been enabled and the selected host is a monitored host. |
| Destination IP address reputation |
Reputation category of the public IP address at the destination of the traffic. This column will only contain data if this IP address is public and listed in the IP address reputation database. The possible values are: "anonymizer", "botnet", "malware", "phishing", "tor", "scanner" or "spam". |
| Destination host reputation | Reputation score of the host at the destination of the traffic. This column will only contain data when host reputation management has been enabled and the selected host is a monitored host. |
NOTE
The logs will now be displayed for models without hard drives.
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View source host,
- View destination host,
- Add the source host to the Object base,
- Add the destination host to the Object base,
- Ping source host,
- Traceroute to source host,
- Ping destination host,
- Traceroute to destination host,
- Send source to quarantine,
- View packet,
- Flush alarms.