Presentation of the interface
Main window
From this window, you can open several windows, each connected to different firewalls.
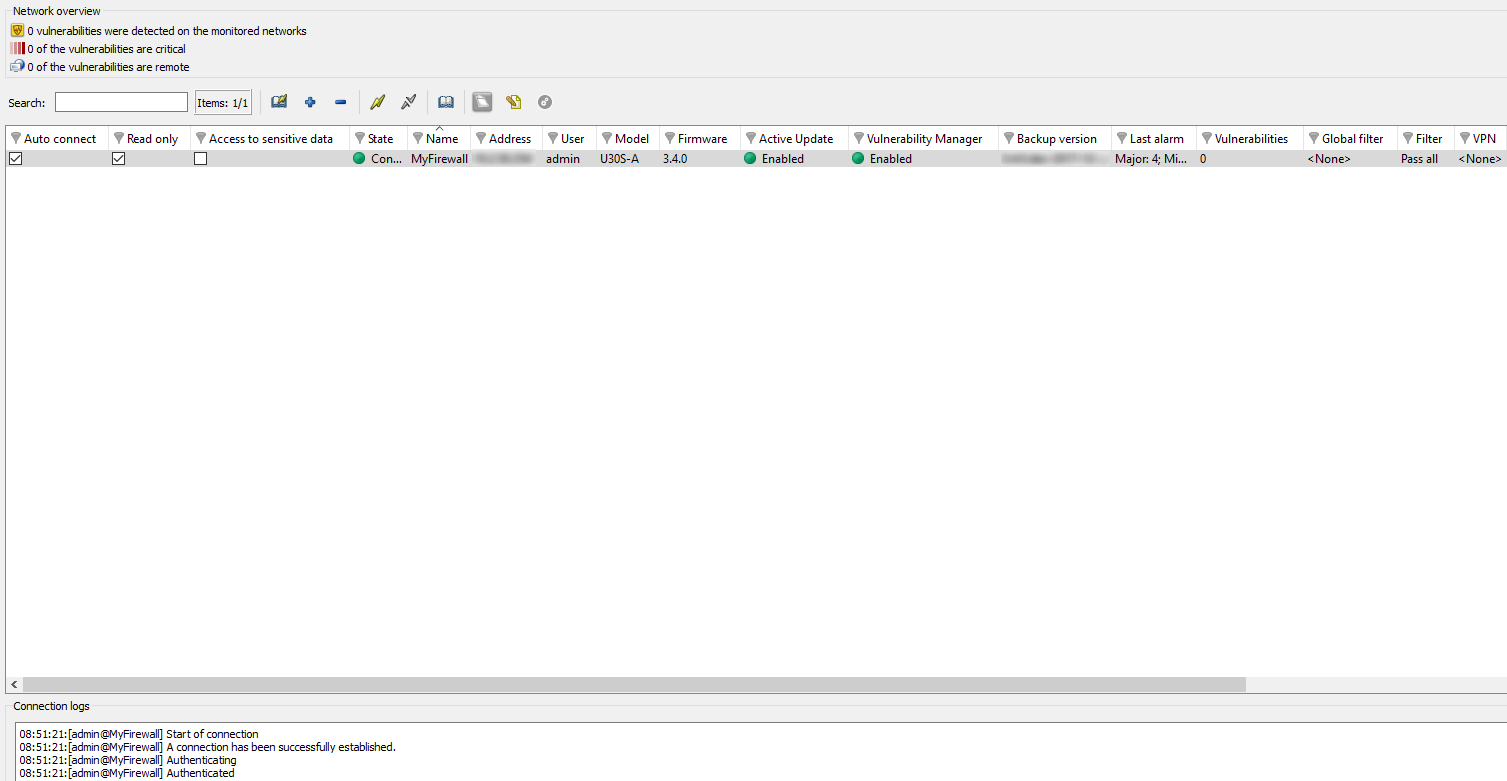
Figure 7: Overview
Once Monitor is connected, it will open a welcome window (Overview Menu) which will display various types of information on the firewall’s activity.
It consists of five parts:
- A menu bar,
- A horizontal bar containing icons relating to connection and a search zone,
- A vertical bar containing a menu directory allowing Stormshield Network Real-Time Monitor options to be viewed and configured,
- A result display zone,
- A status bar.
REMARK
The other windows in the menu directory may contain a button bar or a checkbox:
- Refresh,
- Show / Hide help,
- Access to private data,
- Firewall,
- Duplicate.
Descriptions of icons
|
|
Logs on via the address book. |
|
|
Connects directly to a firewall. |
|
|
Disconnects or deletes a connection. |
|
|
Connects to the selected firewall. |
|
|
Disconnects from the selected firewall. |
|
|
Edits the address book. |
|
|
Displays the dashboard of the selected firewall. |
|
|
Generates a web report for the selected firewall:
|
|
|
Logs on to the selected firewall’s web administration. |
Tabs
The main window contains the following menus: File, Windows, Applications, and ? (Help)
|
File |
Allows you to connect to firewalls and to access the application’s general options. |
|
Windows |
Allows you to organize the connection windows on the screen. |
|
? (Help) |
Allows you to access the relevant Help file, and to know which version the monitor runs on. |
Menu tree
|
Overview |
This window lists the firewalls. Monitor opens in this window once the connection has been established.
|
|
Dashboard |
This window gives you a summary of the main information relating to your product’s activity. |
|
Events |
This window lists events that the firewall has raised. |
|
Vulnerability management |
This window allows you to view alarms being raised and to get help in the event of vulnerability. |
|
Hosts |
List of hosts on your network. |
|
Interfaces |
This screen makes it possible to obtain statistics on the use of QoS queues (bandwidth, connections, throughput, etc.). |
|
Quality of Service |
This window allows you to get statistics on bandwidth, connections and throughput. |
|
Users |
This window allows you to get information on users and session privileges on authentication. |
|
Quarantine – ASQ Bypass |
This window displays the list of dynamically quarantined hosts. |
| Routers |
This window shows the status of routers used in the configuration of the firewall: default gateway and routers configured in filter rules (PBR: Policy Based Routing). |
|
VPN tunnels |
This window displays static information on the operation of VPN tunnels and on the source and destination. |
|
Active Update |
This window sets out the status of Active Update on the firewall for each type of update available. |
|
Services |
This window shows the active and inactive services on the firewall and how long they have been active/inactive. |
|
Hardware |
This window shows information on the initialization of high availability and RAID. |
|
Filter policy |
This window displays the active filter policy by grouping implicit and local rules. |
|
VPN Policy |
This window allows viewing the configuration of various VPN tunnel policies. |
|
Logs
|
This window allows viewing the size of the log file in real time.
|
Result display zone
Data and options from the selected menus in the horizontal bar appear in this zone. These windows will be explained in further detail in the corresponding sections.
Pop-up menu on columns
Right-clicking on a column header will display the following options:
|
Filter by this column |
Isolates a set of events according to the criteria provided. For example, filtering by events with a “minor” protocol. When a filter has been applied to a column, the |
|
Clear column filter |
Removes the filter that was previously set on the column. |
|
Clear all filters |
Removes the filters set on all the columns. |
|
Clear all filters except this |
Removes the filters set on all the columns except for the filter on the selected column. |
|
Hide column |
Hides the selected column. |
|
Columns |
Allows selecting the columns to display. |
|
Adjust column width to fit contents |
Columns will be resized according to the contents. |
When the menu Filter by this column is selected, the following screen will appear:
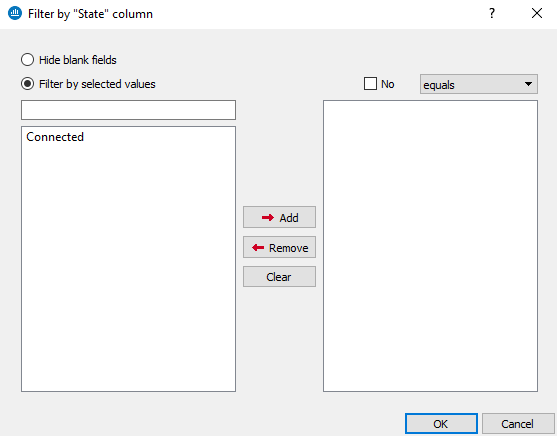
Figure 8: Filter by this column
The screen relates to the column that had been selected previously. (E.g.: Filter by the “Details” column).
- Hide blank fields option: allows displaying only fields that contain data.
- Filter by selected values: a value can be entered manually or selected from the suggested list.
To create a filter, you only need to select one or several values from the suggested list and add them in order for them to appear in the section to the right of the table.
You may use the following operators:
- Equals: the values found have to be equal to those selected.
- Contains: looks for a word in a phrase
- Begins with: looks for a phrase beginning with a string
- Ends with: looks for a phrase ending with a string.
- Joker (Wildcard): See the table below.
- Regular expression: cf. http://qt-project.org/doc/qt-4.8/qregexp.html
|
c |
E.g., if “c” is entered, the system will search for all occurrences of “c”. |
|
? |
Allows searching for a single character. |
|
* |
Allows searching for one or several characters. |
|
[…] |
Allows entering several characters between square brackets. For example, if [ABCD] is selected, the search will be conducted for A or B or C or D. If [A-D] is entered, the search will be for ABCD, if [A-Z] is entered, the search will be for all capital letters. |
Events can therefore be filtered according to one or several values. For example, displaying events using HTTP or HTTPS.
It is also possible to negate a criterion by selecting No. For example, display all entries unless the protocol used is HTTP.
- Columns can be resized according to their contents (option Adjust columns to fit contents).
Furthermore, the administrator can sort the table by clicking on the column by which he wishes to sort.
Pop-up menu on rows
Right-clicking against a line will display a pop-up menu that allows various operations. The options offered vary according to the table.
Overview
3 pop-up menus can be opened in this window:
- When right-clicking against a firewall
- When right-clicking against an empty zone in the list of firewalls
- When right-clicking against the “Connection logs” view
Pop-up menu relating to a firewall
|
Show dashboard… |
Opens the Dashboard menu of the selected firewall. |
|
Generate an instant web report… |
Clicking on this button will generate a report in HTML. This report will contain the following information at any given moment: system information, memory, connected users, services, Active Update status, bandwidth statistics, connection statistics, vulnerabilities, number of hosts, authenticated users, number of major and minor alarms, quarantine, the number of VPN tunnels, filter rules and configured IPSec tunnels. |
|
Launch Web administration interface |
Allows logging on to the web administration interface of the selected firewall |
|
Log off |
Allows logging off from the selected firewall. |
|
Remove this firewall from the connection list… |
Enables disconnecting and deleting the entry that corresponds to this connection. |
|
Add a new firewall to the connection list and connect to it |
Displays the direct connection window to allow logging on to a firewall. |
|
Add a firewall from the address book to the connection list |
Opens the address book window to allow the selection of a registered firewall. |
|
Add this firewall to the address book |
Opens a window that will allow saving the selected firewall in the address book. |
|
Edit the address book |
Opens the address book window to enable editing. |
Pop-up menu from right-clicking against an empty zone
|
Add a new firewall to the connection list and connect to it |
Displays the direct connection window to allow logging on to a firewall. |
|
Add a firewall from the address book to the connection list |
Opens the address book window to allow the selection of a registered firewall. |
|
Edit the address book |
Opens the address book window to enable editing. |
Pop-up menu relating to connection logs
|
Copy |
Copies the selected log line(s). |
|
Copy link location |
Copies the location of the link. |
|
Select all |
Selects all the log lines. |
|
Clear logs |
Deletes all log lines. |
Events
Right-clicking against a line containing an event will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by the priority “Major”, the administrator will get all the lines containing “Major”. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
View source host… |
Indicates the name of the source host. If this option is selected, the Hosts menu will open. |
|
View destination host… |
Indicates the name of the destination host. |
|
Add the source host to the Object base |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
|
Add the destination host to the Object base |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
|
Ping source host |
Allows pinging the source host from the firewall and obtaining its response time as a result. |
|
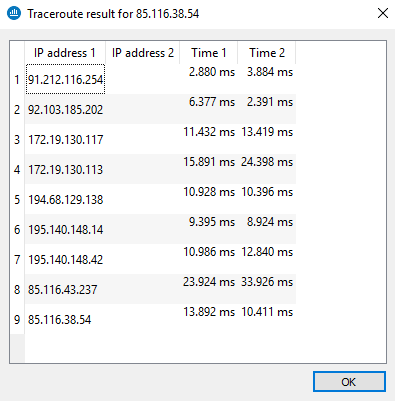
Traceroute to source host |
Two Traceroute commands are used to determine and test all appliances traffic has to go through in order to reach the source host from the firewall. The results are presented in the form of a table containing four columns:
REMARK When an appliance on the route does not respond to Traceroute requests, SN Real-Time Monitor will wait for the test packet to expire. The display time of the results window may then be longer.
|
|
Ping destination host |
Allows pinging the destination host from the firewall and obtaining its response time as a result. |
|
Traceroute to destination host, |
Allows testing and listing (Traceroute) all appliances traffic has to go through in order to reach the selected destination host from the firewall. This action works in the same way as Traceroute to source host. |
|
Send source to quarantine |
Allows quarantining the source host for a fixed period of 1 minute, 5 minutes, 30 minutes or 3 hours. |
|
View packet... |
This will open the tool that will allow you to view malicious packets. |
|
Flush alarms |
Clears the list of alarms displayed. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. |
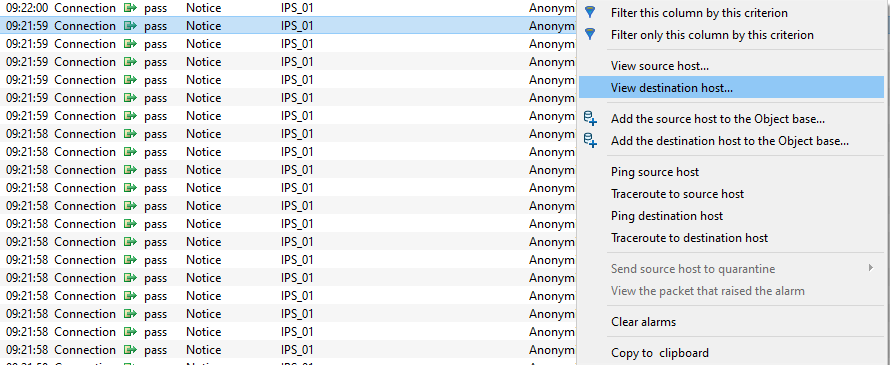
Figure 9: Pop-up menu
Vulnerability manager
In the Vulnerability tab, 3 pop-up menus can be opened:
- When right-clicking against a line detailing a vulnerability
- When right-clicking against a line detailing a host
- When right-clicking against the help zone,
Pop-up menu for a line containing a vulnerability
Right-clicking against a line containing vulnerability will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Critical" priority, the administrator will get all the lines containing "Critical". NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. |
Pop-up menu for a line containing a host
Right-clicking against a line containing a host will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by the "Client" priority, the administrator will get all the lines containing "Client" hosts. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
View host |
The Hosts tree menu will open to display additional information on the detected host. During “pre-filtering”, the host concerned will be selected. The data will be filtered according to the host name if available, or by its address. |
|
Add the host to the Object base, |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
In the Applications tab, 2 pop-up menus can be opened:
- When right-clicking against a line detailing an application
- When right-clicking against a line detailing a host
Pop-up menu for a line containing an application
Right-clicking against a line containing an application will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by the "Web server", the administrator will get all the lines containing the "Web server" family. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
Pop-up menu for a line containing a host
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Linux OS", the administrator will get all the lines containing the "Linux OS". NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
View host |
The Hosts tree menu will open to display additional information on the detected host. During “pre-filtering”, the host concerned will be selected. The data will be filtered according to the host name if available, or by its address. |
|
Add the host to the Object base, |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
In the Information tab, 3 pop-up menus can be opened:
- When right-clicking against a line containing information
- When right-clicking against a line detailing a host
- When right-clicking against the help zone,
Pop-up menu for a line containing information
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by the "Web server", the administrator will get all the lines containing the "Web server" family. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Pop-up menu for a line containing hosts
Right-clicking against a line containing an event will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Linux OS", the administrator will get all the lines containing the "Linux OS". NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
View host |
The Hosts tree menu will open to display additional information on the detected host. During “pre-filtering”, the host concerned will be selected. The data will be filtered according to the host name if available, or by its address. |
|
Add the host to the Object base, |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
Hosts
Many pop-up menus can be opened in this window:
- When right-clicking against a host,
- When right-clicking against the “Vulnerabilities” tab,
- When right-clicking against the “Applications” tab,
- When right-clicking against the “Information” tab,
- When right-clicking against the “Connections” tab,
- When right-clicking against the “Events” tab,
- When right-clicking against the help zone,
- When right-clicking against a DHCP lease.
Pop-up menu relating to a host
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Linux OS", the administrator will get all the lines containing the "Linux OS". NOTE Using this option will replace all the current filters on the columns |
|
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
|
Remove host from ASQ… |
Enables deleting the host’s ASQ information. This may be useful especially if a host has been hacked. The “Monitor modify” privilege is necessary. A message will appear, asking you to confirm this action. |
|
|
Reset Vulnerability Manager information |
Resets Vulnerability Manager data for the selected host. The “Monitor modify” privilege is necessary. A message will appear, asking you to confirm this action. When you perform this reset, the host will be deleted from the Vulnerability Manager database and as well as from data counters (detected vulnerabilities, software, etc). |
|
|
Send to quarantine |
The quarantined host will be dynamically blocked for a duration to be specified. (This duration can either be 1 minute, 5 minutes, 30 minutes or 3 hours). The “Monitor modify” privilege is necessary. You will not be asked to confirm this action. |
|
|
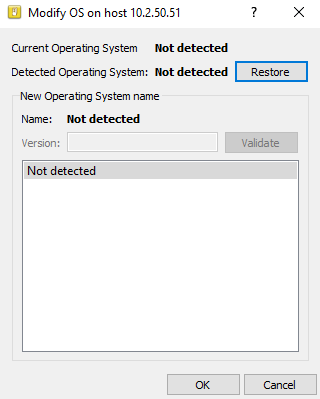
Manually set the Operating System |
This option allows specifying a host’s operating system when Stormshield Network Vulnerability Manager is unable to detect it automatically. The window will then offer several fields:
Current operating system: The OS that Stormshield Network Vulnerability Manager uses for detecting vulnerabilities on a host. The OS of a host may not be detected sometimes.
Detected operating system: OS that Stormshield Network Vulnerability Manager detects after performing a traffic scan on a host. The Restore button allows removing the OS indicated by the user and reverting to the OS detected by Stormshield Network Vulnerability Manager.
New OS name: In the event the host’s OS is not detected by Stormshield Network Vulnerability Manager, it is possible to impose it by selecting it from the suggested list. In this case, 2 situations may arise:
Imposing the host’s OS when it has not been detected will allow, in particular, viewing the vulnerabilities of services and products according to the system.
Figure 10: Manually set the Operating System |
|
|
Add the host to the Object base, |
This option allows:
For further information regarding this option, please refer to the Technical Note “Stormshield Network Collaborative Security”. |
|
|
Ping host |
Allows pinging the host from the firewall and obtaining its response time as a result. |
|
|
Traceroute to host |
Two Traceroute commands are used to determine and test all appliances that traffic has to go through in order to reach the host from the firewall. The results are presented in the form of a table containing four columns:
REMARK When an appliance on the route does not respond to Traceroute requests, SN Real-Time Monitor will wait for the test packet to expire. The display time of the results window may then be longer. |
|
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
|
Pop-up menu in the “Vulnerability” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Critical" severity, the administrator will get all the lines containing "Critical" severity. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
View hosts with the same vulnerability |
Allows displaying only hosts with a similar vulnerability. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Pop-up menu in the “Applications” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
View all hosts that use this application |
The Stormshield Network Vulnerability Manager menu appears with the name of the program concerned in pre-filtering. |
|
View the vulnerabilities for this application |
The “Vulnerabilities” tab is selected with the name of the program concerned in pre-filtering. |
|
Impose a server application |
The “Monitor modify” privilege is necessary. Only server programs can be modified.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Pop-up menu in the “Information” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
View hosts with the same information |
The Stormshield Network Vulnerability Manager menu appears with the name of the program concerned in pre-filtering.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Pop-up menu in the “Connections” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
|
Ping source host |
Allows pinging the source host from the firewall and obtaining its response time as a result. |
|
|
Traceroute to source host |
Two Traceroute commands are used to determine and test all appliances traffic has to go through in order to reach the source host from the firewall. The results are presented in the form of a table containing four columns:
REMARK When an appliance on the route does not respond to Traceroute requests, SN Real-Time Monitor will wait for the test packet to expire. The display time of the results window may then be longer.
|
|
|
Ping destination host |
Allows pinging the destination host from the firewall and obtaining its response time as a result. |
|
|
Traceroute to destination host, |
Allows testing and listing (Traceroute) all appliances traffic has to go through in order to reach the destination host from the firewall. This action works in the same way as Traceroute to source host. |
|
|
Send connection to quarantine |
Allows quarantining the connection for a fixed period of 1 minute, 5 minutes, 30 minutes or 3 hours. This allows preventing certain downloads, for example. |
|
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
|
Pop-up menu in the “Events” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
|
View the packet that raised the alarm |
This will open the tool that will allow you to view malicious packets. |
|
|
Ping source host |
Allows pinging the source host from the firewall and obtaining its response time as a result. |
|
|
Traceroute to source host |
Two Traceroute commands are used to determine and test all appliances traffic has to go through in order to reach the source host from the firewall. The results are presented in the form of a table containing four columns:
REMARK When an appliance on the route does not respond to Traceroute requests, SN Real-Time Monitor will wait for the test packet to expire. The display time of the results window may then be longer.
|
|
|
Ping destination host |
Allows pinging the destination host from the firewall and obtaining its response time as a result. |
|
|
Traceroute to destination host, |
Allows testing and listing (Traceroute) all appliances traffic has to go through in order to reach the destination host from the firewall. This action works in the same way as Traceroute to source host. |
|
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
|
Pop-up menu relating to a DHCP lease
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Linux OS", the administrator will get all the lines containing the "Linux OS". NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
Display host |
Allows displaying details of the selected host. |
|
Ping host |
Allows pinging the host from the firewall and obtaining its response time as a result. |
|
Traceroute to host |
Allows testing and listing (Traceroute) all appliances traffic has to go through in order to reach the destination host from the firewall. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Interfaces
Several pop-up menus can be opened in this window:
- When right-clicking against an interface,
- When right-clicking against the “Incoming connections” tab,
- When right-clicking against the “Outgoing connections” tab,
Pop-up menu relating to an interface
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
Display hosts associated with this interface |
This option allows displaying the list of hosts that have the same interface.
|
Pop-up menu in the “Incoming connections” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
View source host… |
Indicates the name of the source host. If this option is selected, the Hosts menu will open. |
|
View destination host… |
Indicates the name of the destination host. |
|
Send connection to quarantine |
Allows quarantining the connection for a fixed period of 1 minute, 5 minutes, 30 minutes or 3 hours. This allows preventing certain downloads, for example. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Pop-up menu in the “Outgoing connections” tab
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Unix", the administrator will get all the lines containing the "Unix" operating system. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website. |
|
View source host… |
Indicates the name of the source host. If this option is selected, the Hosts menu will open. |
|
View destination host… |
Indicates the name of the destination host. |
|
Send connection to quarantine |
Allows quarantining the connection for a fixed period of 1 minute, 5 minutes, 30 minutes or 3 hours. This allows preventing certain downloads, for example. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. . Data can be copied in two different ways:
|
Quality of Service
Refer to the section Quality of Service (QoS).
Users
2 pop-up menus can be opened in this window:
- When right-clicking against the “users” zone
- When right-clicking against an “administration sessions” zone
Pop-up menu in the “users” zone
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by a specific firewall address, the administrator will get all the lines containing this host. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
Remove user from ASQ |
Enables deleting the user’s ASQ information. This may be useful especially if a user has been affected by an attack. The “Monitor modify” privilege is necessary. A message will appear, asking you to confirm this action. |
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
Pop-up menu in the “administration sessions” zone
|
Copy to the clipboard |
Copies the selected line to the clipboard. Data can be copied in two different ways:
|
Quarantine – ASQ Bypass
2 pop-up menus can be opened in this window:
- When right-clicking against the “Quarantine” zone
- When right-clicking against an “ASQ Bypass” zone
Pop-up menu in the “Quarantine” zone
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, when filtering by a particular firewall address, the administrator will obtain only all the relevant lines. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard.
|
Pop-up menu in the “ASQ Bypass” zone
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, when filtering by a particular firewall address, the administrator will obtain only all the relevant lines. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard.
|
VPN tunnels
This module now presents tunnels set up via IPSec VPN and SSL VPN under two separate tabs.
“SSL VPN Tunnels” tab
By right-clicking on a row of SSL VPN tunnels, you will access a pop-up menu that allows you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field.
|
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the user name, the displayed list will only present the elements containing this user.
|
|
View host |
This option makes it possible to display all characteristics of the host corresponding to the IP addresses (vulnerabilities, applications, connections, etc) in the Host module of Stormshield Network Real Time Monitor. |
|
Remove this tunnel |
This option allows instantaneously shutting down the selected SSL VPN tunnel. |
“IPSec VPN Tunnels" tab
Right-clicking against a line containing a VPN tunnel will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "mature" status, the administrator will get all the lines containing "mature" status. |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to a source address, the displayed list will only show the elements containing this source address. |
|
View logs of outgoing SPIs |
This option will allow displaying the SPIs of the negotiated outgoing SA. |
|
View logs of incoming SPIs |
This option will allow displaying the SPIs of the negotiated incoming SA. |
|
View the outgoing policy |
Hypertext link enabling the display of the outgoing policy visible in the VPN Policy menu. |
|
View the incoming policy |
Hypertext link enabling the display of the incoming policy visible in the VPN Policy menu. |
|
Reset this tunnel |
The selected tunnel will be deleted, but the configuration on the firewalls will still be active. The SAs matching the selected tunnel will be cleared; new SAs will have to be renegotiated so that the tunnel can be used again. |
|
Reset all tunnels |
All tunnels will be deleted. |
Active Update
Right-clicking against a line in the Active Update section will bring you to the pop-up menu that will allow you to:
|
Copy to the clipboard |
Data can be copied in two different ways:
|
Services
Right-clicking against a line containing a service will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Enabled" status, the administrator will get all the lines containing "Enabled" status. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the "Enabled" status, the displayed list will only show the elements containing this status. |
|
Copy to the clipboard |
Copies the selected line to the clipboard.
|
Hardware
This menu is dedicated to high availability. Refer to the Hardware section.
Filter policy
This menu allows you to view different types of rules:
- Implicit rules
- Global filter rules
- Local filter rules
- Local NAT rules
For more information, please refer to the Filter policy section.
VPN Policy
Right-clicking against a line containing a VPN policy will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Firewall_bridge" as a destination router, the administrator will get all the lines containing the "Firewall_bridge" destination router. |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. |
|
View corresponding tunnels |
Goes to the VPN tunnels menu with a filter. |
Logs
VPN
Right-clicking against a line containing a VPN policy will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by "Phase established" message, the administrator will get all the lines containing the "Phase established" message. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor. Example If your cursor points to the destination / website consulted, the displayed list will only present the elements containing this destination / website.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard.
|
System
Right-clicking against a line in the System section will bring you to the pop-up menu that will allow you to:
|
Filter by these criteria, |
This option allows restricting the list of results to the selected field. For example, if the data is filtered by the priority “Major”, the administrator will get all the lines containing “Major”. NOTE Using this option will replace all the current filters on the columns |
|
Filter only this column by this criterion, |
This option allows restricting the list of results to the criteria under your cursor.
|
|
Copy to the clipboard |
Copies the selected line to the clipboard.
|
Status bar
Figure 11: Status bar
The status bar contains menus from the tree that may have been opened during a session. Being able to do so is particularly useful when you are monitoring several firewalls at a time. You will be able to get back the same information window for each firewall and thus make simultaneous comparisons.
Button bar

Figure 12: Button bar
This bar appears in most menus in Monitor.
Refresh
This button allows you to reinitialize the list displayed (Alarms, Vulnerability Manager, Hosts, Interfaces, Quality of Service, Users, Quarantine, VPN Tunnels, Active Update, Services, Hardware, Filter Policy, VPN, Logs).
Show/Hide help
This button allows you to show or hide a help screen. Subsequently, you only need to click on the selected line to get help when necessary.
Access to private data
If this option is selected, the administrator who has logged on to Monitor will be able to obtain privileges to view private data shown in the current window (source IP addresses, host names, user names, etc.). Depending on the account used, a temporary access code provided by the firewall supervisor may be required before such data can be displayed.
When this option is not selected, private data will be replaced with the term Anonymized.
Firewall
This drop-down menu allows you to filter the list of alarms on a selected firewall.
Duplicate
The window can be duplicated using the button found in it. This comes in handy especially when you wish to change the target (firewall or <all>) and view.
Search zone
The search zone is presented in 2 different formats:
1st format: the bar shown below can be seen on all screens except for the “Events” screen.

Figure 13: Search zone
2nd format: the bar below appears in the Events menu.
Figure 14: Search zone - Events
The Filters button contains the filters defined by the application and allows obtaining only the lines below:
- Alarm
- Virus
- Connection
- Web
- FTP
- Filtering
- SSL
- SSL VPN
- Authentication
- Applications (alarm)
- Protection (alarm)
- Malware (alarm)
Search
In this zone, you will be able to conduct searches through items in the list. Items are filtered while search criteria are being entered.









 icon will appear in blue in the column label.
icon will appear in blue in the column label.