Use case: Blocking access to USB keys that have not been decontaminated
Many malware programs can be spread through USB keys. To safely monitor USB keys plugged into your pool, you can make it mandatory to decontaminate all keys with contents that were modified outside the organization. To do so, set up air-gapped workstations equipped with antivirus solutions that analyze the plugged in devices. Next, configure SES Evolution so that it automates this analysis and guarantees that only USB keys with the appropriate level of trust are allowed on SES Evolution agents.
USB keys that are modified on a SES Evolution-protected workstation keep their trust level and do not need to be decontaminated.
-
Create a Decontamination agent group of all the workstations used as USB key decontamination airlocks. For further information, refer to the section Creating agent groups.
-
Enable the following options in the Trusted devices section:
-
Allow device identification - Automatic,
-
Automatically scan devices.
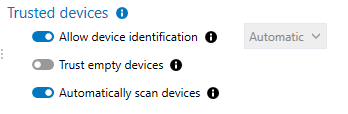
For further information, refer to the section Detecting and configuring the trust level on devices
-
-
Create a USB storage security rule.
-
In the left section of the rule, add an All file ID that corresponds to all files.
- Block all access in the default behavior.
- Add a specific behavior that grants full access to keys with Trust level 2.
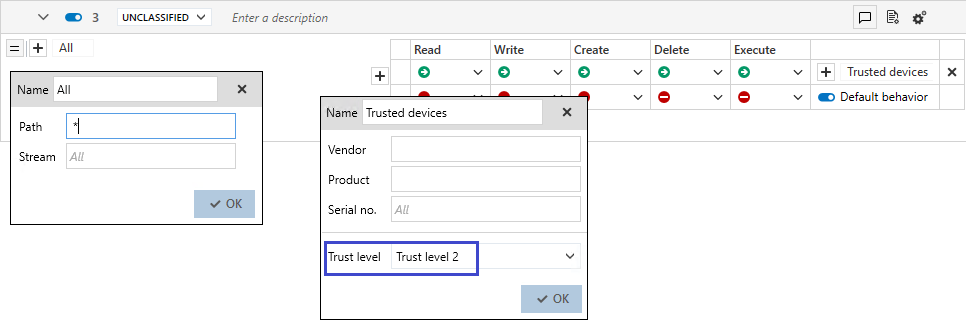 With this rule, full access can be granted to Trust level 2 devices, and those with a lower level will be blocked.
With this rule, full access can be granted to Trust level 2 devices, and those with a lower level will be blocked. - Apply this rule to all agent groups if you want to monitor the trust level of their USB keys.
For further information, refer to the section Controlling storage on USB devices.