SSL VPN
SSL VPN allows remote users to securely access a company's resources - internal or otherwise - via the SNS firewall. An SSL VPN client must be installed on the user’s workstation or mobile device before a VPN tunnel can be set up with the SNS firewall.
Several VPN clients are compatible with the SSL VPN service on the SNS firewall. Stormshield's SSL VPN client (SN SSL VPN Client) has a connection mode that allows it to automatically and securely retrieve its VPN configuration, unlike OpenVPN Connect, on which the VPN configuration must be manually integrated.
Enabling the SSL VPN service
|
Enable SSL VPN  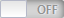 |
Enables or disables VPN SSL on the SNS firewall. |
Configuring the SSL VPN service
Two tabs allow you to respectively configure:
- The general settings of the SSL VPN service,
- The policy verifying the compliance of client workstations (ZTNA). Zero trust network access (ZTNA) consists of trusting users and devices only after they have been verified.
NOTE
If the LZ4 compression feature in the SSL VPN service is enabled, a warning message will automatically appear when the module opens, encouraging you to disable the feature. You are strongly advised to disable it for security reasons. If you ignore this warning, a message will continue to be displayed as long as the feature is not disabled. You will need to use these CLI/serverd commands to disable it:CONFIG OPENVPN UPDATE compress=0 then CONFIG OPENVPN ACTIVATE.
Do note that in order to set up SSL VPN tunnels, the Authentication, Access privileges and Filter - NAT modules must also be configured. For more information, refer to the technical note Configuring and using the SSL VPN on SNS firewalls.
See also