Checking whether the private key in the SNS firewall's certificate is protected
This chapter explains how to check whether the private key in the SNS firewall's certificate is protected by the TPM.
From the web administration interface
This use case is exclusive to SNS 4.7 and higher versions.
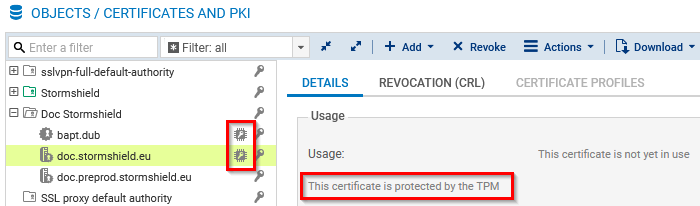
In Configuration > Objects > Certificates and PKI, locate the certificate (identity) in question. If the ![]() icon appears, this means that the private key of the certificate is protected by the TPM. This information also appears in the Details tab when the certificate in question is selected beforehand.
icon appears, this means that the private key of the certificate is protected by the TPM. This information also appears in the Details tab when the certificate in question is selected beforehand.
From the CLI console
To verify the certificates used in the firewall configuration:
Run the following command:
MONITOR CERT
tpm=Used indicates that the private key of the certificate is protected by the TPM.
To check all certificates on the firewall:
-
Run the following command to show the certification authorities:
PKI CA LIST
-
If required, show the list of intermediate certification authorities that signed the root authority in question (
<RootCA>in the command) with:PKI CA LIST CANAME=<RootCA>
-
Show the certificates issued by the certification authority (
<CA>in the command) with:PKI CERT LIST CANAME=<CA>
tpm=ondiskindicates that the private key of the certificate is protected by the TPM. -
If required, show information about a certificate (
<CERTNAME>in the command) with:PKI CERT SHOW CANAME=<CA> NAME=<CERTNAME>
From the SMC server
For more information, refer to the section Finding out whether a private key is TPM-protected in the SMC administration guide.