Disabling TPM (Trusted Platform Module) certificate protection during installation on the firewall
SNS firewalls offer the possibility of protecting certificates with TPMs.
Whenever you install an identity (.p12 format) on an SNS firewall from the SMC server, the protection of the private key with a TPM is enabled by default. The private key is protected by a password stored on the TPM.
In SMC, TPM-protected keys can only be used in IPsec VPN topologies with IKEv2 encryption profiles.
To create VPN topologies with IKEv1 encryption profiles, disable this protection using the environment variable SMC_FW_TPM_ENABLED.
If a TPM has been installed and enabled on an SNS model firewall, whenever you install an identity on a firewall from the SMC server, the TPM will protect the corresponding private key.
To find out whether a private key is protected by a TPM, go to the following panels in the SMC server web administration interface:
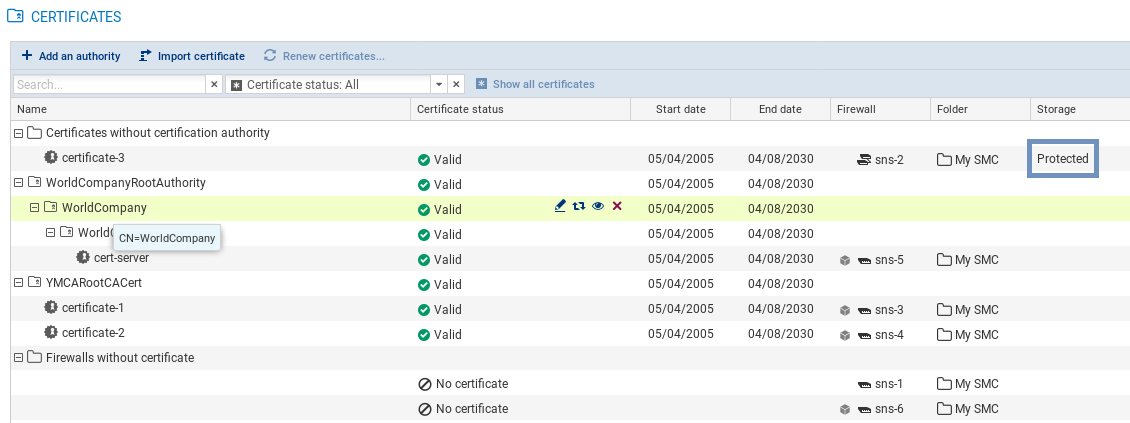
- In the Configuration > Certificats menu, show the Storage column (hidden by default). The status Protected is indicated in the column if a private key is protected by a TPM.
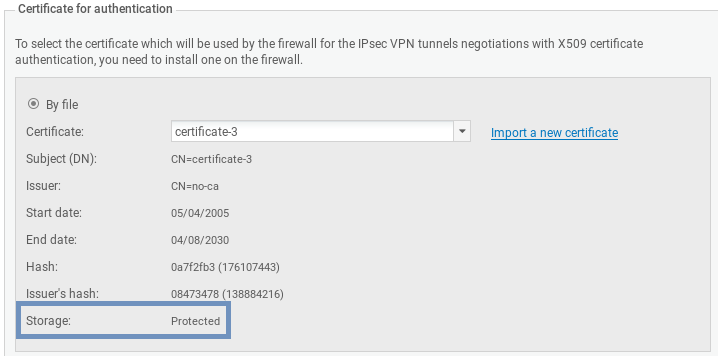
- In a firewall's System > IPsec VPN properties, the status Protected is indicated in the X509 certificate's characteristics.
Whenever you install a new certificate on the firewall, the status will also be indicated in the window showing the results of the installation of a certificate.
To disable TPM protection when you install an identity on an SNS firewall from the SMC server, the SMC_FW_TPM_ENABLED environment variable must be modified:
- Log in to the SMC server via the console of your hypervisor or in SSH.
- In the file /data/config/fwadmin-env.conf.local, change the value of the environment variable:
SMC_FW_TPM_ENABLED=false - Restart the server with the command
nrestart smc.
- To enable TPM protection on a private key that has already been installed on a firewall, run the following SNS CLI script from the Scripts/SNS CLI scripts menu:
PKI CERTIFICATE PROTECT caname=<CA_name> name=<certificate_CN> tpm=ondisk