Configuring multifactor authentication (TOTP)
This section explains how to configure a multifactor authentication method (TOTP) to set up SSL VPN tunnels with the SNS firewall.
General information on multifactor authentication
Multifactor authentication strengthens the authentication of users who set up SSL VPN tunnels with a second authentication factor.
The second factor is generally a one-time password, known as an OTP or TOTP, which the user must enter in addition to their password to set up the SSL VPN tunnel. Stormshield has its own TOTP solution.
A third-party solution can also be used with a RADIUS server or a third-party application to be installed on a trusted device. For example, the Trustbuilder solution (formerly inWebo) is compatible and allows users to generate OTPs or approve setting up connections (push notifications) in their application.
Configuring the multifactor authentication solution
Stormshield TOTP solution
Refer to the technical note Configuring and using the Stormshield TOTP solution, which explains how to configure and manage the TOTP solution on the SNS firewall, and presents the enrollment procedure for TOTP solution users.
Third-party solution with a RADIUS server
The chosen third-party multifactor authentication solution has to be configured and connected to your RADIUS server. If you need help with this configuration, refer to the documentation for your chosen solution.
On the SNS firewall:
- Enable and configure the RADIUS method to connect your SNS firewall to your RADIUS server. To do so, go to Configuration > Users > Authentication, Available methods tab. For more information, refer to the section Authentication > Available methods tab > RADIUS in the v4 user guide or v5 user guide, depending on the SNS version used.
-
Increase the maximum response time for RADIUS requests if the selected solution requires users to approve the setup of their SSL VPN tunnels in an application. The default maximum response time is 3 seconds. To increase it to 30 seconds, for example, use the following CLI/serverd commands:
CONFIG AUTH RADIUS timeout=30000 btimeout=30000
CONFIG AUTH ACTIVATE
Setting up SSL VPN tunnels using multifactor authentication
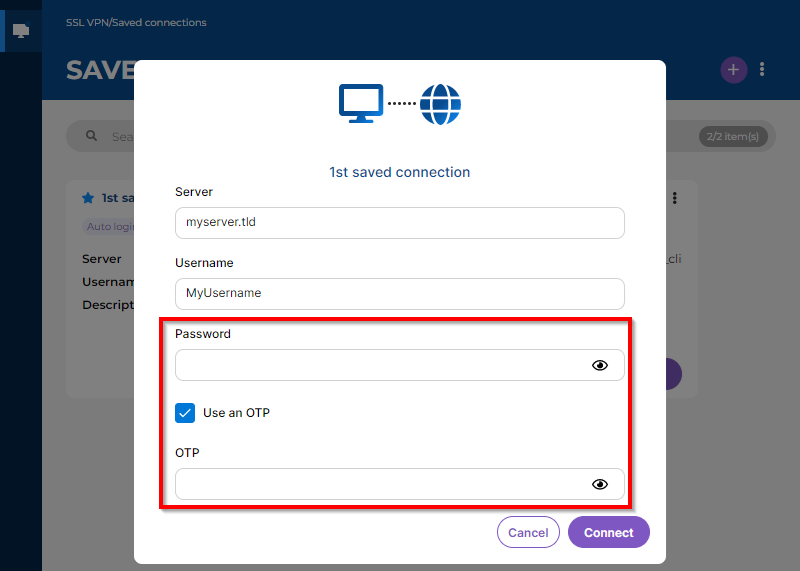
The Use an OTP checkbox must be selected in advance in the details of the connection on the Stormshield SSL VPN client.
-
Set up the SSL VPN tunnel in the menu of your choice on the Stormshield SSL VPN client.
In the window, fill in the Password and OTP fields, depending on whether the selected solution requires a password and OTP, only an OTP without a password, or neither password nor OTP, only the approval to set up the SSL VPN tunnel from an application.
Depending on the menu used, click once on Connect to show the Password and OTP fields.
-
If the selected solution requires the setup of the SSL VPN tunnel to be approved in an application, a push notification will be sent to your device. Open your application and approve the setup of the SSL VPN tunnel.
-
Wait while the Stormshield SSL VPN client sets up the SSL VPN tunnel.