Using an authentication method with a user certificate
This section explains how to use an authentication method with a user certificate to set up SSL VPN tunnels with the SNS firewall. If you do not wish to use an authentication method with a user certificate, proceed to the next section.
With this authentication method, users can set up SSL VPN tunnels by authenticating on the SNS firewall with their user certificate.
Requirements
To use the authentication method with a user certificate, you need to meet the following requirements:
- An SNS firewall in version 5.
- Stormshield SSL VPN clients in version 5. Earlier versions of the Stormshield SSL VPN client and third-party SSL VPN clients, such as OpenVPN Connect, are not compatible.
- SSL certificate method enabled and configured in Authentication > Available Methods on the SNS firewall. For more information, refer to the section Authentication > Available methods tab > Certificate (SSL) in the v4 user guide or v5 user guide, depending on the SNS version used.
- Rules created, allowing users to authenticate through the SSL Certificate method in the Authentication > Authentication Policy module on the SNS firewall. Adapt the information in the section Configuring the authentication policy to obtain this configuration.
- SSL VPN service enabled and configured in the SSL VPN module on the SNS firewall. This configuration is described in the following sections.
- User certificates installed on the workstations of the users in question. You can download the user identity of the certificate in P12 format in the Objects > Certificates and PKI module on the SNS firewall.
Setting up an SSL VPN tunnel by authenticating with a user certificate
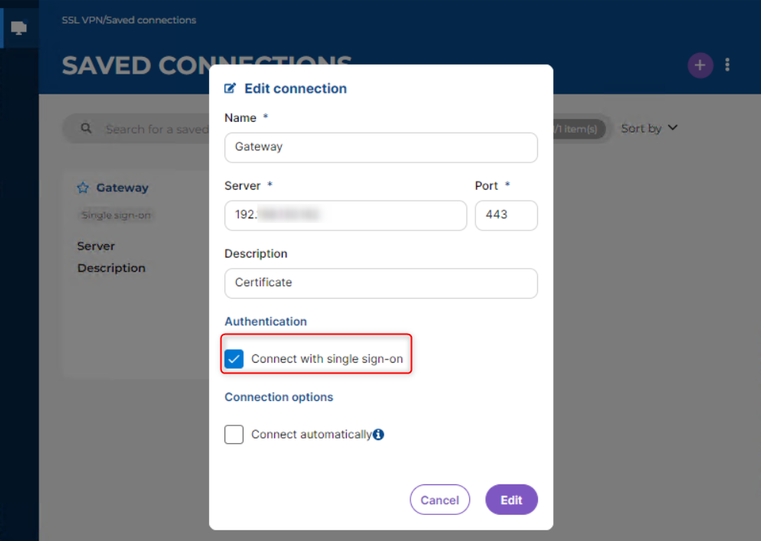
On the Stormshield SSL VPN client, the connection (saved or direct) must be set up with the following parameters:
- Stormshield mode has to be selected. OpenVPN connections (imported OVPN file) are not compatible.
- The Connect with single sign-on checkbox must be selected.
Once the SSL VPN tunnel has been initiated, the SNS firewall's captive portal opens automatically in the user's web browser. The user then authenticates on the portal by following the instructions.
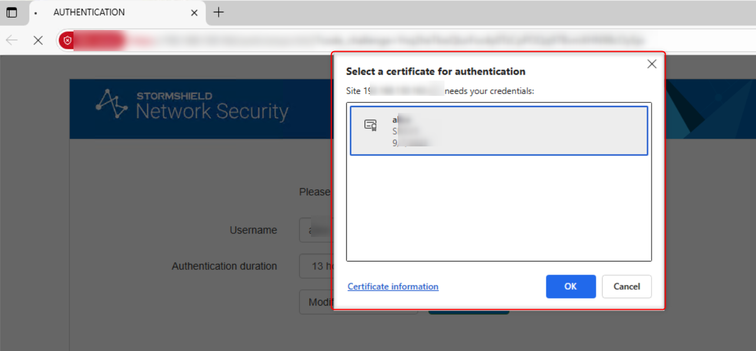
Once the user is authenticated, the SSL VPN tunnel is set up. The expiry date of the user's authentication session is displayed in the Stormshield SSL VPN client graphical interface. As long as this date has not been reached, and the authentication session is still valid on the SNS firewall, the user does not need to authenticate again to set up the SSL VPN tunnel.
For more information, refer to the section Setting up a secure connection in the Stormshield SSL VPN client v5 user and configuration guide.
Known limitations
TLS 1.3 incompatibility
With SNS version 5.0.2, authentication with user certificates is not supported over TLS 1.3. This limitation will be fixed in a future version of SNS.
Workarounds are available, depending on your users' web browser:
-
On Firefox, enable the following setting in the Firefox configuration:
security.tls.enable_post_handshake_auth
-
For other browsers such as Chrome or Edge, you need to force the SNS firewall's captive portal to use TLS 1.2. To do so, run the following SSH commands on the SNS firewall:
setconf /usr/Firewall/ConfigFiles/auth Config TLSv13 0
ensl
Entering the user name during authentication
Users currently have to enter their user names on the captive portal before they can select the certificate to be used for authentication. This limitation will be improved in a future version of SNS.