Case no.1: configuring the satellite sites Spoke A and Spoke B
In a Hub and Spoke configuration, a satellite site only knows one IPsec peer: the Firewall of the Hub site.
Spoke A site
Following the method described in the paragraph Creating the Site_Spoke_A and Site_Spoke_B peers, create the peer Site_FW_Hub using the following values:
- remote gateway: Firewall of the Hub (object Pub_FW_Hub),
- certificate: the certificate of the Spoke A Firewall.
Spoke B site
Following the method described in the paragraph Creating the Site_Spoke_A and Site_Spoke_B peers, create the peer Site_FW_Hub using the following values:
- remote gateway: Firewall of the Hub (object Pub_FW_Hub),
- certificate: the certificate of the Spoke B Firewall.
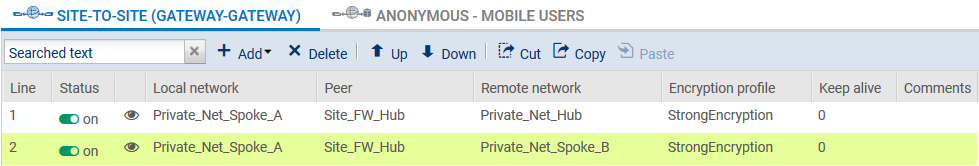
Spoke A site
Following the method described in the paragraph Creating tunnels, create the two tunnels needed:
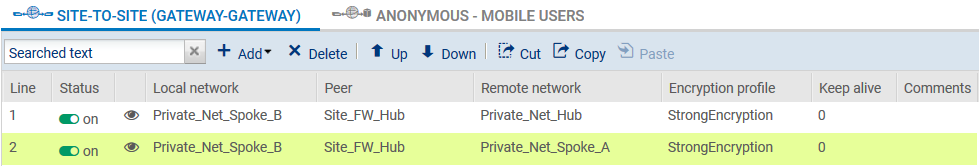
Spoke B site
Following the method described in the paragraph Creating tunnels, create the two tunnels needed:
In this tutorial, traffic between private networks is voluntarily not specified (destination port: ANY). To optimize performance (save bandwidth and machine resources), it is important to refine the filtering on satellite sites (authorized protocols, ports, etc) in order to prevent unnecessary packets from going through the tunnels. This filtering policy will also be on the Hub site.
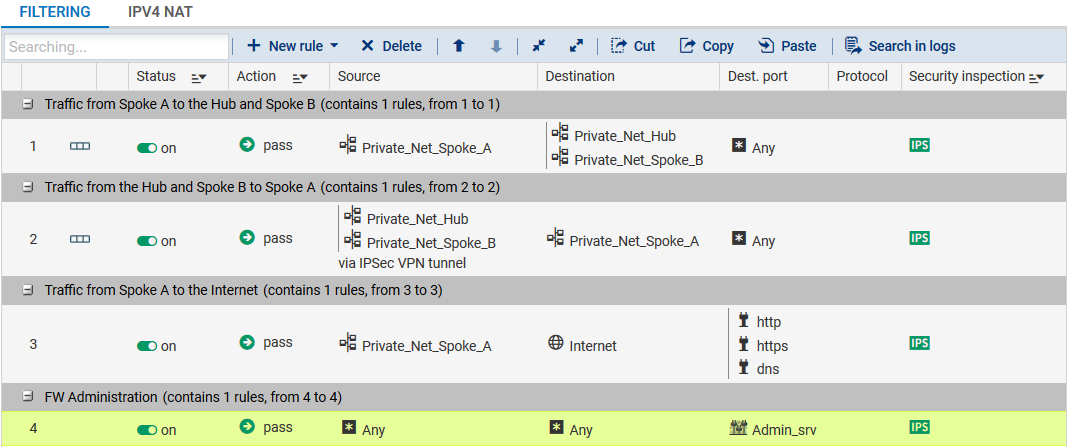
Spoke A site
Define the filtering rules needed for exchanges between Spoke A and Spoke B, Spoke A and the Hub as well as local traffic to the Internet:
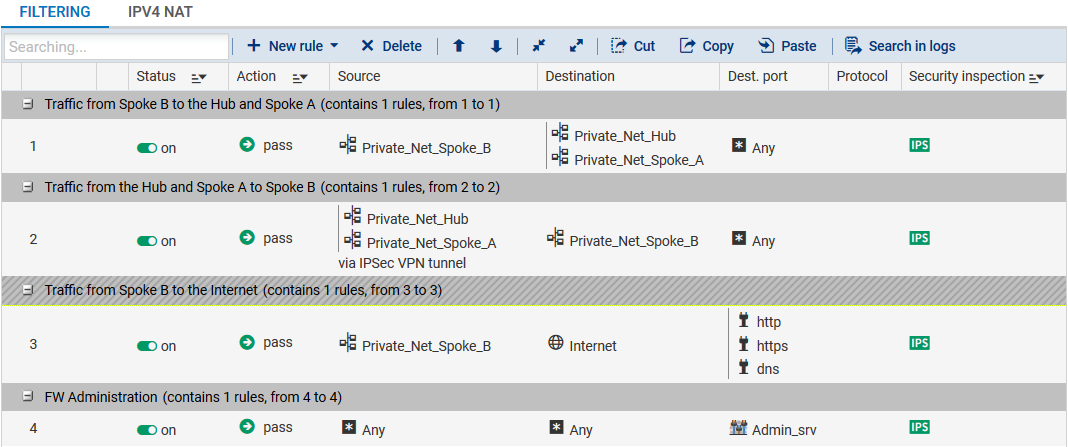
Spoke B site
Define the filtering rules needed for exchanges between Spoke B and Spoke A, Spoke B and the Hub as well as local traffic to the Internet:
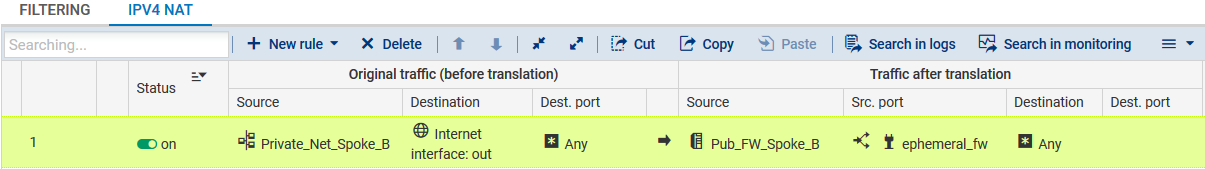
Spoke A site
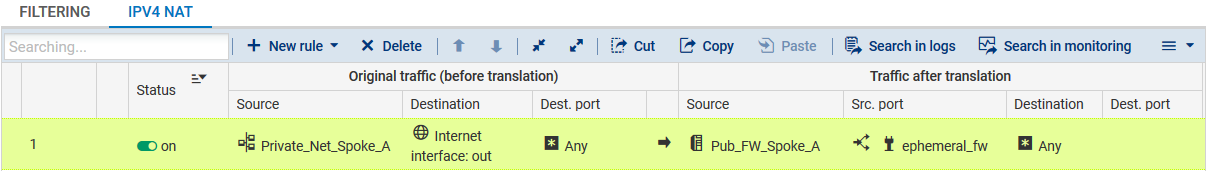
To allow hosts on the network Private_Net_Spoke_A to access the internet, create the following NAT rule:
Spoke B site
To allow hosts on the network Private_Net_Spoke_B to access the internet, create the following NAT rule: