Recommendations and best practices
Several conditions must be met before firewalls can be interconnected to form an operational cluster.
Choosing a firewall model that supports HA
- HA is offered across the entire SNS range, except for SN160(W) and SN210(W) models.
- HA cannot be configured if the bypass mechanism has been enabled, as both mechanisms are incompatible. For more information, refer to the General configuration tab section in the SNS user manual.
- Clusters must consist of two firewalls of the same model.
- On firewalls that support extension modules, both members of the cluster must have the same number of network interfaces.
- HA is supported on VMWare, HyperV and KVM virtualization platforms. However, it is not supported on public virtualization platforms such as Microsoft Azure, Amazon Web Services and OpenStack.
Obtaining compatible firewalls
To set up a firewall cluster, your firewalls must be in one of the following configurations:
- A standard firewall (master license) and a backup firewall for high availability (slave license),
- Two standard firewalls (master license).
Clusters cannot be configured with two firewalls that have a slave HA license option.
If you choose the master and slave license, the backup firewall is designated with an “HA” label on its packaging (e.g., NA-SN6100 HA) and on its delivery slip.
When you order firewalls that will make up a cluster, the options subscribed for the standard firewall (Extended Web Control, Stormshield Network Vulnerability Manager, Advanced antivirus, etc.) will be automatically replicated on the backup firewall, except for the “Express exchange” option, which must be subscribed individually for each firewall.
Using the same firmware version
- To successfully set up HA, the same firmware version must be installed on both members of the cluster.
- If both firewalls have different firmware versions, the cluster will run in fail-soft mode so that the member with the older firmware version can be upgraded.
Closely following security rules and installation precautions
- Documentation is provided with every firewall, and sets out the security rules and installation precautions that you must follow to ensure that your firewalls are optimally set up.
- These documents are also available in PDF on the Stormshield technical documentation website (Installation guide, Security rules - SN range, Security rules - SN6100 and Security rules - SNi40).
- Refer to Recommended connectors for high availability (HA) links as well in the Product presentation and installation guide available on the Stormshield technical documentation website.
Recommendations regarding dedicated HA links
- HA control links can be set up between unaggregated network interfaces (LACP) or unaggregated VLAN interfaces (LACP).
- An HA control link must be connected to the same physical interface on both members of the cluster (e.g., dmz1).
- If the nodes communicate through an Ethernet interface, the interface has to be reserved solely for this purpose. It will not be supported as the parent interface of a virtual VLAN interface.
- The interface that is used for communications between the nodes of a cluster can be isolated in a VLAN. In this case, some of the advanced features relating to the communication of cluster members will not be available.
- The addresses of HA links must not be translated or routed.
- HA links can go through switches that are compatible with multicast routing. If this is the case, ensure that IGMP snooping features are disabled on the ports that host HA links.
In any case, Stormshield recommends using a direct link between both members of the cluster. - If there is only one HA control link and its connection is lost, both members of the cluster will attempt to manage network traffic, causing the network to be highly unstable.
You are therefore strongly advised to define a secondary HA control link. -
Latency between two members of a cluster must be below 200 ms. This is the time it takes for a packet to make a return trip (i.e., 100 ms outbound and 100 ms inbound).
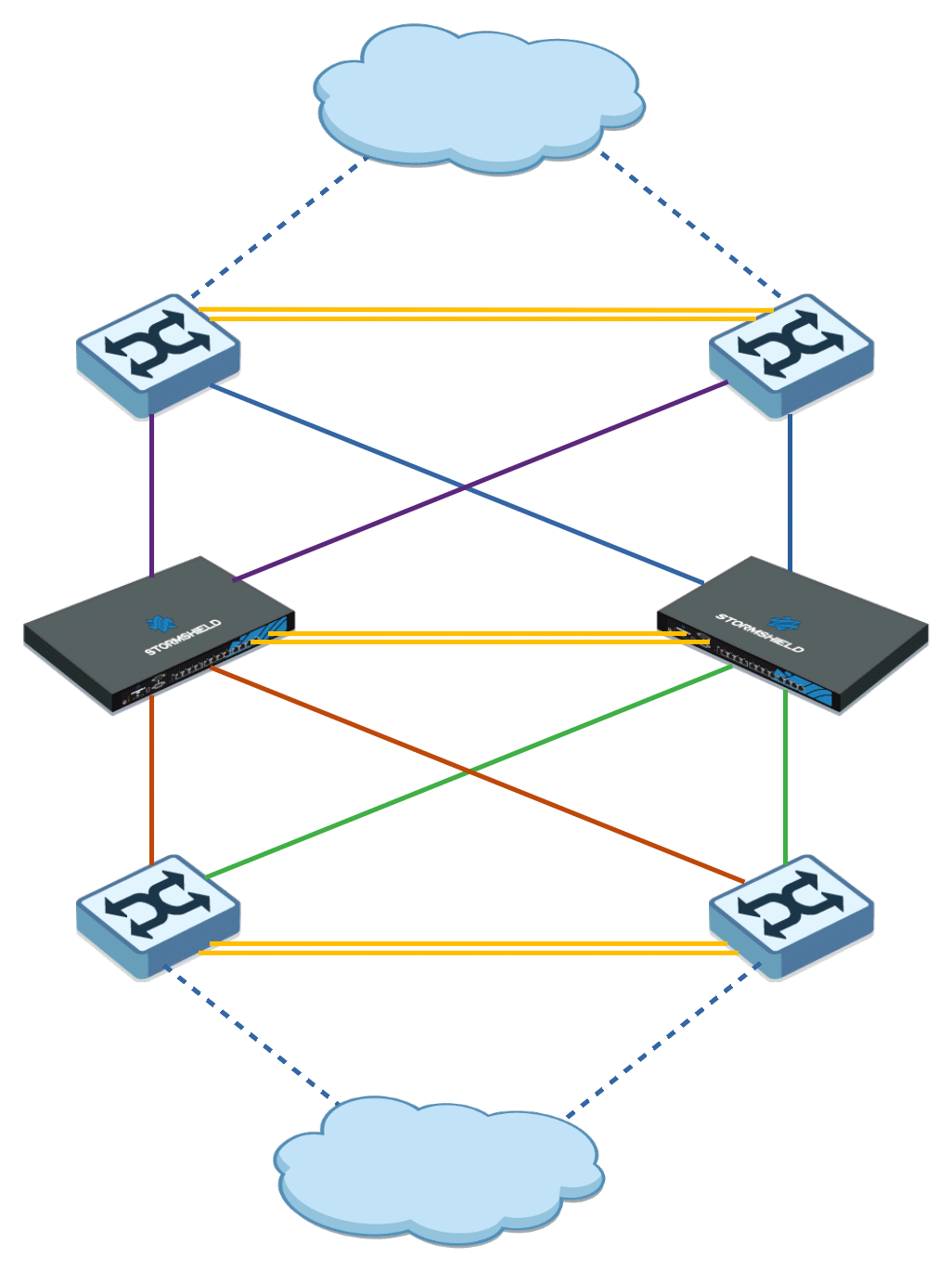
Network architecture - interconnections
To avoid creating a Single Point Of Failure (SPOF), you are strongly advised to:
- Duplicate interconnecting network devices (switches),
- Connect firewalls to each switch,
- Duplicate links between each switch.
Example: