Advanced configuration
Advanced configuration is implemented here. In addition to this configuration connecting the three individual configurations, it also contains an iBGP link that was set up simultaneously with the OSPF link.
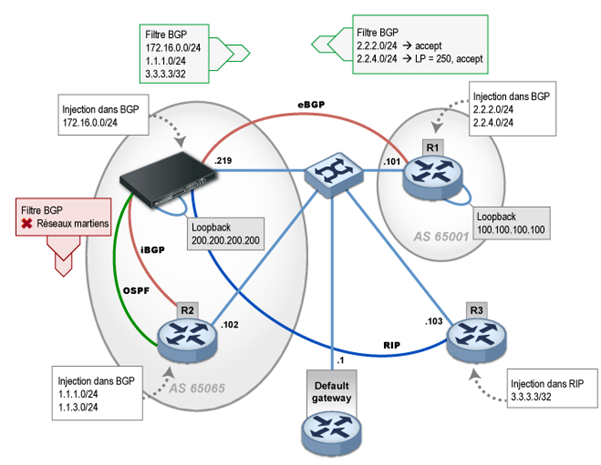
The client's network includes routers R2, R3 and the Stormshield Network firewall. Router R1 is an external BGP neighbor. This network represents a realistic architecture setup, except for the fact that all routers are physically connected through a single LAN.
A standard filter policy is implemented to:
- Announce only outbound public BGP networks,
- Avoid advertising internal networks or martians in the internal BGP,
- Tag one of the routes that were learned in eBGP, with a local-preference value of 250. This measure is generally implemented to monitor load balancing among several eBGP neighbors,
- Announce only one default route in OSPF,
- Announce only one default route in RIP,
The networks that are announced by routers R2 and R3 are respectively announced over BGP and RIP. The use of OSPF to announce the default route is for illustration purposes only.
BIRD configuration
The following is the equivalent configuration file in BIRD:
router id 192.168.97.219;
function is_locormartians()
prefix set martians;
{
martians = [ 169.254.0.0/16+, 172.16.0.0/12+, 192.168.0.0/16+,10.0.0.0/8+, 224.0.0.0/4+, 240.0.0.0/4+ ];
# default
if net.ip = 0.0.0.0 then return true;
# LIR not authorized
if (net.len < 8) || (net.len > 24) then return true;
# martians
if net ~ martians then return true;
# local
if net = 100.100.100.100/32 then return true;
return false;
}
filter out_eBGP {
if net ~ [ 172.16.0.0/24, 3.3.3.3/32, 1.1.1.0/24 ]
then accept;
else reject;
}
filter out_iBGP {
if ( is_locormartians() )
then reject;
else accept;
}
filter lp_tag_in {
if net = 2.2.4.0/24 then {
bgp_local_pref = 250;
accept;
} else accept;
}
filter default_ok {
if net = 0.0.0.0/0 then {
accept;
} else reject;
}
sns_log all; # default is "no extra log"
# This pseudo-protocol watches all interface up/down events.
protocol device {
scan time 10; # Scan interfaces every 10 seconds
}
# The direct protocol automatically generates device routes to
# all network interfaces.
protocol direct {
interface "em3";
ipv4;
}
# This pseudo-protocol performs synchronization between BIRD's routing
# tables and the kernel.
protocol kernel {
learn; # Learn all alien routes from the kernel
persist; # Don't remove routes on bird shutdown
scan time 20; # Scan kernel routing table every 20 seconds
ipv4 {
export all;
preference 254; # Protect existing routes
};
}
protocol rip MyRIP {
# You can also use an explicit name
debug all;
interface "em4" {
mode multicast;
authentication none;
};
ipv4 {
import all;
export filter default_ok;
};
}
protocol ospf MyOSPF {
area 0.0.0.0 {
stub no;
interface "em4" {
type broadcast;
};
};
ipv4 {
export filter default_ok;
import all;
};
}
protocol bgp router1 {
debug all;
description "My 1st BGP uplink";
local as 65065;
neighbor 100.100.100.100 as 65001;
source address 200.200.200.200;
multihop 5;
hold time 180;
keepalive time 60;
ipv4{
export filter out_eBGP;
import filter lp_tag_in;
};
}
protocol bgp router2 {
description "My local BGP neighbor";
local as 65065;
neighbor 192.168.97.102 as 65065;
keepalive time 60;
ipv4 {
next hop self;
export filter out_iBGP;
import all;
};
}
NOTE
You are advised to set the value of the parameter priority 0 in the interface section of the OSPF node configuration, in order to disable the firewall's participation in elections for Designated Router/Backup Designated Router roles.
Allowing RIP, BGP and OSPF protocols in the filter policy
By referring to the sample filter policies presented in the individual RIP, BGP and OSPF configurations, add filter rules to allow RIP, BGP and OSPF routing traffic to and from the firewall.
Checking the proper operation of dynamic routing
Stormshield Network firewall routing table
bird> show route 0.0.0.0/0 via 192.168.97.1 on em4 [kernel1 14:37:15] * (254) 100.100.100.100/32 via 192.168.97.101 on em4 [kernel1 14:37:15] * (254) 3.3.3.3/32 via 192.168.97.103 on em4 [MyRIP 14:37:06] * (120/2) 192.168.97.0/24 dev em4 [MyOSPF 14:01:33] * I (150/10) [192.168.97.102] via 192.168.97.102 on em4 [router2 14:01:17] (100/10) [i] 1.1.1.0/24 via 192.168.97.102 on em4 [MyOSPF 14:01:36] * E2 (150/10/10000) [192.168.97.102] via 192.168.97.102 on em4 [router2 14:01:17] (100/10) [i] 1.1.3.0/24 via 192.168.97.102 on em4 [MyOSPF 14:01:36] * E2 (150/10/10000) [192.168.97.102] via 192.168.97.102 on em4 [router2 14:01:17] (100/10) [i] 2.2.2.0/24 via 192.168.97.101 on em4 [router1 13:54:12 from 100.100.100.100] * (100/?) [AS65001i] 2.2.4.0/24 via 192.168.97.101 on em4 [router1 14:01:17 from 100.100.100.100] * (100/?) [AS65001i] 172.16.0.254/32 dev lo0 [kernel1 14:37:15] * (254) 192.168.97.219/32 dev lo0 [kernel1 14:37:15] * (254) 172.16.0.0/24 dev em3 [direct1 13:54:11] * (240) 10.200.45.254/32 dev lo0 [kernel1 14:37:15] * (254)
To check the value of the local-preference on route 2.2.4.0/24, the details of the routes belonging to the instance of the router1 protocol are shown:
bird> show route protocol router1 all
2.2.2.0/24 via 192.168.97.101 on em4 [router1 13:54:12 from 100.100.100.100] * (100/?) [AS65001i]
Type: BGP unicast univ
BGP.origin: IGP
BGP.as_path: 65001
BGP.next_hop: 100,100,100,100
BGP.local_pref: 100
2.2.4.0/24 via 192.168.97.101 on em4 [router1 14:01:17 from 100.100.100.100] * (100/?) [AS65001i]
Type: BGP unicast univ
BGP.origin: IGP
BGP.as_path: 65001
BGP.next_hop: 100,100,100,100
BGP.local_pref: 250
Router R3 – show IP route
You will notice that the default route is also announced here:
@router3:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF, I - ISIS, B - BGP, > - selected route, * - FIB route
R>* 0.0.0.0/0 [120/2] via 192.168.97.1, eth0, 00:06:15
C>* 1.1.8.0/24 is directly connected, lo
C>* 1.1.9.0/24 is directly connected, lo
S>* 3.3.3.3/32 [1/0] is directly connected, Null0, bh
C>* 127.0.0.0/8 is directly connected, lo
C>* 192.168.97.0/24 is directly connected, eth0
@router3:~$
When this traffic has to be symmetrically routed, for example in the case of NAT, the BIRD configuration must be adapted so that the firewall can be announced as the next-hop. The configuration can be changed in the "default_ok" filter, which is used to announce the default route to R3 over RIP, and to R2 over OSPF:
filter default_ok {
if net = 0.0.0.0/0 then
{
dest = RTD_UNREACHABLE; # annonce le firewall comme next-hop pour cette route
accept;
}
}To impose a gateway other than the firewall itself, this directive must be used:
gw = <ip>;
Router R2 – show IP route
@router2:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
I - ISIS, B - BGP, > - selected route, * - FIB route
O>* 0.0.0.0/0 [110/10000] via 192.168.97.1, eth0, 22:26:17
C>* 1.1.1.0/24 is directly connected, lo
C>* 1.1.3.0/24 is directly connected, lo
B>* 2.2.2.0/24 [200/1] via 100.100.100.100 (recursive via 192.168.97.1), 00:02:04
B>* 2.2.4.0/24 [200/1] via 100.100.100.100 (recursive via 192.168.97.1), 00:02:04
C>* 127.0.0.0/8 is directly connected, lo
C>* 192.168.97.0/24 is directly connected, eth0
@router2:~$
Router R1 – show IP route
@router1:~$ show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP, O - OSPF,
I - ISIS, B - BGP, > - selected route, * - FIB route
S>* 0.0.0.0/0 [1/0] via 192.168.97.1, eth0
B>* 1.1.1.0/24 [20/0] via 200.200.200.200 (recursive via 192.168.97.219), 00:00:29
C>* 2.2.2.0/24 is directly connected, lo
C>* 2.2.4.0/24 is directly connected, lo
B>* 3.3.3.3/32 [20/0] via 200.200.200.200 (recursive via 192.168.97.219), 00:00:08
C>* 100.100.100.100/32 is directly connected, lo
C>* 127.0.0.0/8 is directly connected, lo
B>* 172.16.0.0/24 [20/0] via 200.200.200.200 (recursive via 192.168.97.219), 00:00:29
C>* 192.168.97.0/24 is directly connected, eth0
S>* 200.200.200.200/32 [1/0] via 192.168.97.219, eth0
@router1:~$
In high availability configurations (cluster)
When the BGP dynamic routing protocol is used in an SNS firewall cluster, and to allow the BGP neighbor to shut down a BGP session properly during a switch in the cluster, it would be helpful to define a BFD instance in the BIRD configuration:
protocol bfd mybfdsession {
neighbor myneighborip;
}In this example:
protocol bfd mybfdsession {
neighbor 100.100.100.100;
}And to name this instance in the BGP configuration accordingly:
protocol bgp MyBGP {
…
bfd graceful;
connect retry time 5;
…
}