BGP
The supported version is BGP v4 for IPv4 and IPv6.
The following is the "BGP simple" configuration:
The "BGP_simple" configuration is implemented as follows:
sns_log off; # default is "no extra log"
router id 192.168.97.219;
protocol kernel {
persist; # Don't remove routes on bird shutdown
scan time 20; # Scan kernel routing table every 20 seconds
ipv4 {
export all; # Default is export none
preference 254; # Protect kernel routes with high preference
};
learn; # Learn all alien routes from the kernel
}
protocol device {
scan time 10; # Scan interfaces every 10 seconds
}
protocol direct {
interface "em3";
}
protocol bgp MyBGP {
description "My 1st BGP uplink";
local as 65065;
neighbor 100.100.100.100 as 65001;
multihop 5;
hold time 180;
keepalive time 60;
ipv4 {
import all;
export where source = RTS_DEVICE;
};
default bgp_local_pref 100;
source address 200.200.200.200;
}
# This pseudo-protocol is used to configure static routes.
protocol static MyStaticRoutes {
ipv4;
}
Explanations
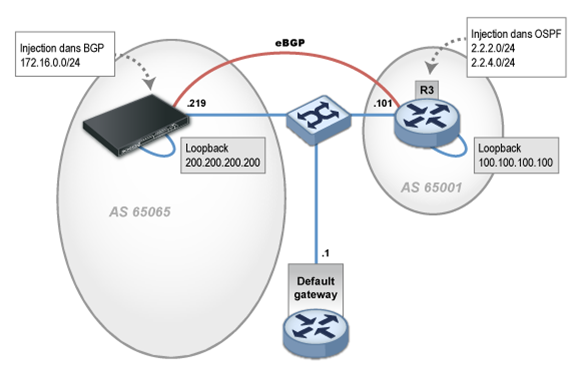
Unlike most mainstream routers, the local AS has to be specified for each BGP instance.
By following best practices, this eBGP session has to be set up between loopback interfaces, instead of physical interfaces. The IP address of the local loopback in question therefore has to be configured (200.200.200.200/32), by specifying this address as the source, and a static route to the neighbor's loopback.
Loopback virtual interfaces
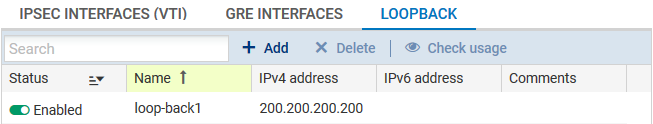
Loopback interfaces can be configured in the web administration interface, in Configuration > Network > Virtual interfaces, Loopback tab:
We recommend declaring the static route to the remote loopback on the firewall outside the BIRD configuration, in Configuration > Network > Routing, Static routes tab, to prevent BGP traffic from being blocked by “IP address spoofing” alarms:
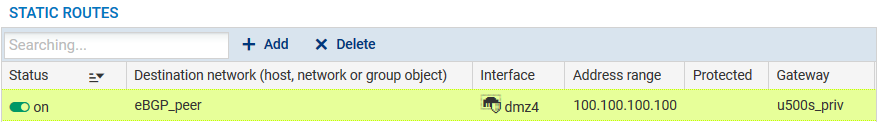
Once again, we will select only the sub-network 172.16.0.0/24, which is directly connected to the interface em3 as the route to be announced to our neighbors.
In this case, we have defined an anonymous export filter, directly in the "export” instruction, with "where” as the keyword. This export filter selects the routes that have RTS_DEVICE as their source, i.e., routes that were obtained by the direct pseudo-protocol.
The hold-time value has been set to 180s, a standard mainstream value. By default, BIRD implements 240s. The keepalive value (calculated as 1/3 of the hold-time) does not need to be specified, but we are mentioning it explicitly for clarity. The same goes for the default local-preference value.
Allowing the BGP protocol in filter policies
Filter rules are required in order to allow BGP routing traffic to and from the firewall.
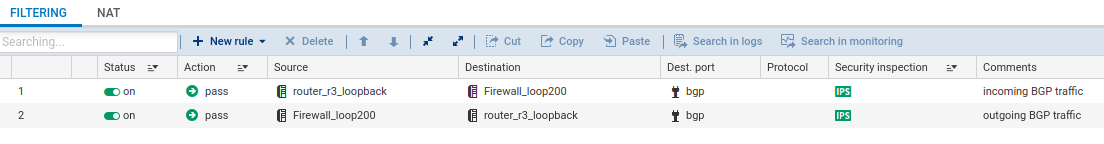
Checking the proper operation of BGP dynamic routing
The “show protocols” command below confirms that the session is functioning.
bird> show protocols router1 name proto table state since info router1 BGP master up 12:47 Established
Routes have been received from the neighbor:
bird> show route protocol router1 100.100.100.100/32 via 192.168.97.101 on em0 [router1 13:09 from 100.100.100.100] (100/?) [AS65001?] 2.2.2.0/24 via 192.168.97.101 on em0 [router1 13:09 from 100.100.100.100] *(100/?)[AS65001?] 2.2.4.0/24 via 192.168.97.101 on em0[router1 13:09 from 100.100.100.100] *(100/?)[AS65001?]
The BGP neighbor receives the route that has been announced and released by the filter. As for route 1.1.1.1/32, it has been blocked.
Authentication
TCP-MD5 authentication can be set up between BGP routers in a BIRD configuration.
With this method, BGP sessions can be protected through the authentication of frames in the TCP header, in line with RFC2385.
This involves adding the "password" directive in the BGP router configuration in the /usr/Firewall/ConfigFiles/Bird/bird.conf files (dynamic routing of IPv4 and IPv6 packets). The “source address" directive must also be added, by specifying the IP address of the interface that was used for the authentication.
For example:
protocol bgp MyBGP {
description "My 1st BGP uplink";
local as 65065;
neighbor 100.100.100.100 as 65001;
password "very_secret";
multihop 5;
hold time 180;
keepalive time 60;
ipv4 {
import all;
export where source = RTS_DEVICE;
};
default bgp_local_pref 100;
source address 200.200.200.200;
}
NOTE
Passwords must not contain spaces or equal symbols (‘=’).
In high availability configurations (cluster)
When the BGP dynamic routing protocol is used in an SNS firewall cluster, and to allow the BGP neighbor to shut down a BGP session properly during a switch in the cluster, it would be helpful to define a BFD instance in the BIRD configuration:
protocol bfd mybfdsession {
neighbor myneighborip;
}
In this example:
protocol bfd mybfdsession {
neighbor 100.100.100.100;
}
And to name this instance in the BGP configuration accordingly:
protocol bgp MyBGP {
…
bfd graceful;
connect retry time 5;
…
}