IMPORTANT
SNS 3.x versions have reached End of Maintenance since July 1st, 2024.
We recommend that you update your SNS firewalls to a version with maintenance to guarantee the protection of your infrastructure.
Modifying an Ethernet interface (in bridge mode)
If an interface is in a bridge, it will be represented as a child node in relation to the bridge. Thus, a bridge may contain several child nodes.
You can change the parameters of each interface, whether or not it belongs to the bridge. To do so, select an interface located inside or outside a bridge on the left-hand side of the window. Two tabs will then appear:
NOTE
Ethernet interfaces cannot be added or deleted.
“Configuration of the interface” tab
| Name (mandatory) |
Name given to the bridge interface. (See warning in the introduction to the section on Interfaces) |
| Comments |
Allows you to enter comments regarding the interface. |
| Physical port |
Name of the physical port (example: in (port 2)). |
| VLANs attached to the interface |
List of VLANs attached to the selected interface. The appliance does not need to be systematically rebooted whenever a VLAN is deleted.
|
| Color |
Color assigned to the interface. |
| This interface is |
An interface can either be “internal (protected)” or “external (public)”.
If you select “internal (protected)”, you are indicating that this interface is protected. This protection includes the memorization of machines that have logged on to this interface, conventional traffic security mechanisms (TCP) and implicit rules for services offered by the firewall such as DHCP (see the section Implicit rules). Protected interfaces are represented by a shield (
If you select “external (public)”, you are indicating that this part of the network is linked up to the internet. In most cases, the external interface, linked up to the internet, has to be in external mode. The shield icon disappears when this option is selected. |
Address range
| None (interface disabled) |
By selecting/unselecting this option, the interface will be enabled/disabled. By disabling an interface, it becomes unusable. In terms of use, this may correspond to an interface to be used in the near or distant future, but which is not active. An interface which has been disabled because it is not in use is an example of an additional security measure against intrusions. |
| Dynamic IP (obtained by DHCP) |
The assigned IP address can be matched to a domain name via a DNS service provider (dyndns.org for example) in order to contact this firewall without having to know its IP address. This option is used when your firewall does not have a static IP address (e.g., your service provider, or DHCP renews its IP address regularly).
This feature can be enabled by selecting a dynamic DNS account that you would have configured earlier. The configuration of dynamic DNS clients is explained further in the document Dynamic DNS module.
This field allows specifying to the firewall that the configuration of the bridge (IP address and mask) is defined by DHCP. In this case, the “DHCP” zone in the Advanced properties tab will be enabled. |
| Address range inherited from the bridge |
If the interface is part of a bridge, the address range of the bridge can be retrieved. |
| Fixed IP (static) |
By selecting this option, the interface will have a static address range. In this case, its IP address and the mask of the sub-network to which the interface belongs, have to be indicated. |
Here, several associated IP addresses and network masks may be defined for the same bridge (the need to create aliases, for example). These aliases may allow you to use this Stormshield Network firewall as a central routing point. As such, a bridge can be connected to various sub-networks with a different address range. To add or remove them, simply use the Add and Delete buttons located above the fields in the table.
Several IP addresses (aliases) can be added in the same address range on an interface. In this case, these addresses must all have the same mask. Reloading the network configuration will apply this mask on the first address and a mask /32 on the following addresses.
“Advanced properties” tab
| MTU |
Maximum length (in bytes) of frames transmitted on the physical support (Ethernet) so that they are sent at one go (without fragmentation). This option is not available for interfaces contained in a bridge. |
| Physical (MAC) address |
WARNING This option is not accessible for firewalls in high availability.
This window allows you to specify a MAC address for an interface instead of using the address assigned by the firewall. This allows you to better facilitate the integration of the Stormshield Network firewall in transparent mode into your network (by specifying your router’s MAC address instead of having to reconfigure all the workstations using this MAC address).
If the interface is contained in a bridge, it will have the same MAC address as the bridge. NOTE This field is grayed out as the interface belongs to a bridge. It can neither be modified nor deleted. |
DHCP
NOTE
This option will be indicated as “disabled” if the option Dynamic IP (obtained by DHCP) was not selected in the Configuration of the interface tab and the options will be grayed out.
| DNS name (optional) |
Name of the DNS server (FQDN) for the connection.
This optional field does not identify the DHCP server but the firewall. If this field has been entered and the external DHCP server has the option of automatically updating the DNS server, the DHCP server will automatically update the DNS server with the name and the IP address provided by the firewall.
This name consists of 6 bytes in hexadecimal separated by : |
| Requested lease time (seconds) |
Period during which the IP address is kept before renegotiation. |
| Request domain name servers from the DHCP server and create host objects |
If this option is selected, the firewall will retrieve DNS servers from the DHCP server it contacts (access provider, for example) to obtain its IP address.
Two objects will be dynamically created in the object database upon the selection of this option: Firewall_<interface name>_dns1 and Firewall_<interface name_dns2. They can then be used in the configuration of the DHCP service. So, if the Firewall provides the users on its network with a DHCP service, the users will also benefit from the DNS servers given by the access provider. NOTE This option will be disabled if the option Dynamic IP (obtained by DHCP) was not selected in the Configuration of the interface tab |
Bridge – Routing without analysis
NOTE
This option will be indicated as “disabled” if the option Address range inherited from the bridge was not selected in the Configuration of the interface tab and the options will be grayed out.
| Authorize without analyzing |
Allows letting IPX (Novell network), Netbios (on NETBEUI), AppleTalk (for Macintosh), PPPoE or Ipv6 packets pass between the bridge’s interfaces. No high-level analysis or filtering will be applied to these protocols (the firewall will block or pass). |
Bridge – Routing by interface
NOTE
This option will be indicated as “disabled” if the option Address range inherited from the bridge was not selected in the Configuration of the interface tab and the options will be grayed out.
| Keep initial routing |
This option will ask the firewall to not modify the destination in the Ethernet layer when a packet goes through it. The packet will be resent to the same MAC address from which it was received. The purpose of this option is to facilitate the integration of firewalls transparently into an existing network, as this makes it possible to avoid the need for modifying the default route of machines on the internal network.
This option must be enabled to ensure that a DHCP server located on the interface in question, and which sends unicast responses to requests, runs properly Known limitations Features on a firewall that inserts or modifies packets in sessions may fail to function correctly. These cases are:
|
| Keep VLAN IDs |
This option enables the transmission of tagged frames without the firewall having to be the VLAN endpoint. The VLAN tag on these frames is kept so that the Firewall can be placed in the path of a VLAN without the firewall interrupting this VLAN. The Firewall runs seamlessly for this VLAN.
This option requires the activation of the previous option "Keep initial routing". |
| Gateway address |
This field is used for routing by interface. All packets that arrive on this interface will be routed via a specified gateway. |
Media
| Media |
Connection speed of the network. By default the firewall detects this automatically but you can enforce the use of a particular mode. The different speeds available are: "Automatic detection", "10 Mb Half duplex", "10 Mb Full duplex", "100 Mb Half duplex", "100 Mb Full duplex", "1 Gb Half duplex", "1 Gb Full duplex". WARNING If the firewall is directly connected to an ADSL modem, you are advised to enforce the medium that you wish to use on the interface concerned. |
Interface’s bandwidth (for information only)
| Bandwidth |
Defines the throughput on an interface. This is an automatic entry that is not compulsory: it is used for monitoring in the calculation of bandwidth. |
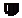 ).
).