SN Vulnerability Manager (SNVM)
Introduction
Stormshield Network Vulnerability Manager is a module that allows network administrators to gather information in real time and to analyze it in order to spot possible vulnerabilities that may compromise the security of their networks. Among other things, it also allows raising alarms generated by the intrusion prevention engine and thus to maintain an optimal security policy.
Stormshield Network Vulnerability Manager collects and archives in particular, information relating to the operating system, to various active services as well as to the different applications that have been installed. As a result, descriptive profiles can be made of network elements.
Stormshield Network Vulnerability Manager aims to:
- Configure your company network’s security policy.
- Analyze the status of the risk.
- Optimize the level of security.
- Report security events.
The procedure is as follows:
 Stormshield Network’s intrusion prevention engine (ASQ) extracts data in real time using network protocols that it knows.
Stormshield Network’s intrusion prevention engine (ASQ) extracts data in real time using network protocols that it knows.
 Vulnerability Manager then combines and weights these data.
Vulnerability Manager then combines and weights these data.
 The vulnerability found can then be fixed using databases that have been indexed dynamically. Once all this information has been collected, they will be used in Monitor so that flaws on the network can be corrected, or prohibited software can be detected, or the real risk relating to the attack can be identified in real time.
The vulnerability found can then be fixed using databases that have been indexed dynamically. Once all this information has been collected, they will be used in Monitor so that flaws on the network can be corrected, or prohibited software can be detected, or the real risk relating to the attack can be identified in real time.
 The profile is therefore complete.
The profile is therefore complete.
 One or several solutions can thus be considered.
One or several solutions can thus be considered.
Example
A company has a public website that it updates twice a month via FTP. At a specific date and time, a vulnerability that affects FTP servers is raised and Monitor immediately takes it into account, enabling the network administrator to detect it at practically the same time.
This vulnerability is represented by a line that indicates the number of affected hosts and whether a solution is available.
By deploying this line, details of the hosts concerned will appear, as well as the service that has been affected by the vulnerability. Help, in the form of links, may be suggested to correct the detected flaw.
Once the network administrator becomes aware of the vulnerability, he can correct it at any moment, quarantine the affected host(s) and generate a report.
When you click on the Vulnerability Manager menu in the menu directory, the scan window will consist of the following:
- A Vulnerabilities tab.
- An Applications tab.
- An Information tab.
"Vulnerabilities" tab
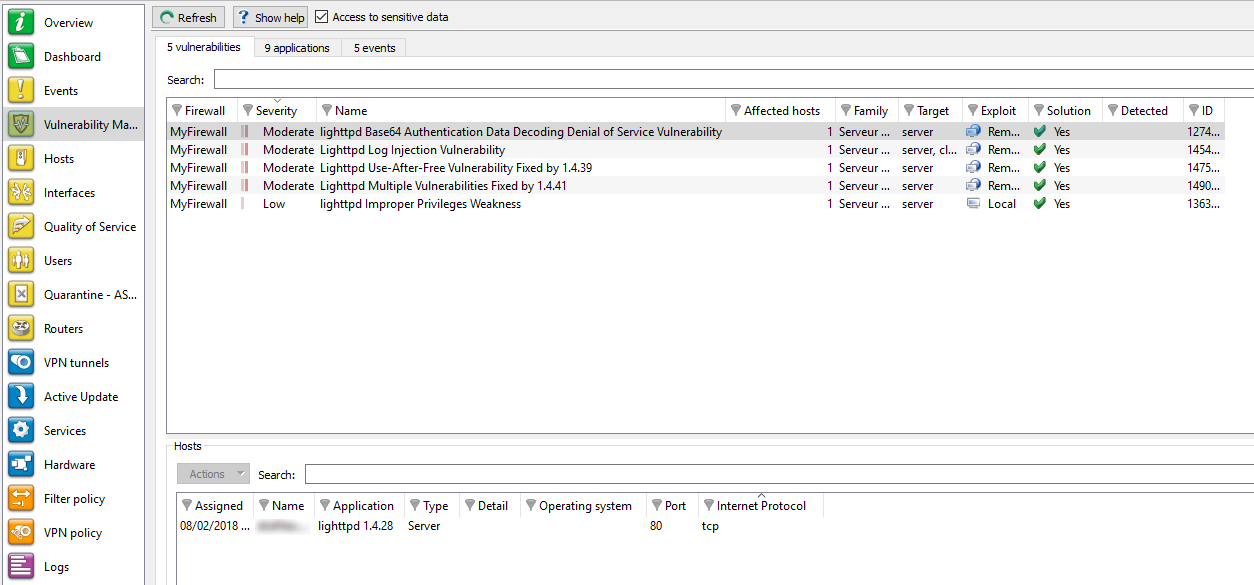
Figure 31: Vulnerability Manager
This screen consists of 3 views:
- A view of the list of vulnerabilities.
- A view of the list of hosts affected by this vulnerability.
- A hidden help view that you can display by clicking on "Show help" (top left of the screen). This allows working around the selected vulnerability, if a solution exists.
“Vulnerability(ies)” view
This view allows you to view all the vulnerabilities that the firewall has detected. Each line represents a vulnerability.
REMARK
The number of vulnerabilities is displayed in the tab’s label.
The information provided in the “vulnerability” view is as follows:
Firewall | Serial number or name (if known) of the firewall at the source of the vulnerability. |
Severity | Indicates the level of severity on the host(s) affected by the vulnerability. There are 4 levels of severity: Low, Moderate, High, Critical. |
Name | Indicates the name of the vulnerability. |
Affected hosts | Number of hosts affected by the vulnerability. |
Family | Family to which the vulnerability belongs. |
Target | One of 2 targets: Client or Server. |
Exploit | Access may be local or remote (via the network). It allows exploiting the vulnerability. |
Workaround | Indicates whether a workaround exists. |
Discovered on | Date on which the vulnerability was detected. WARNING This refers to the date on which the vulnerability was discovered and not the date on which it appeared on the network. |
ID | Allows a unique identification of the vulnerability. |
"Hosts" view
This view allows you to view all the vulnerabilities for a given host. Every row represents a host.
The "Hosts" view displays the following data:
Assigned | Date on which the host was assigned. |
Name | Name of the host affected by the attack (if it exists). |
Address | IP address of the host affected by the attack. |
Application | Name and version of the application (if available). |
Type | Application type (Client/Server/Operating system). |
Details | Name of the service prone to being affected by the vulnerability. |
Operating system | Vulnerable host’s operating system. |
Port | Number of the port on which the vulnerability had been detected. |
Internet Protocol | Name of the protocol used. |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View host,
- Add the host to the Object base,
Help zone
The help zone allows you to get more details relating to the attack. Thus the administrator can correct the vulnerability.
Click on the Show help button to show or hide the help zone associated with a vulnerability.
Typically, help comes in the form of a descriptive file that contains explanations, links to the publisher’s site or to bug fixes.
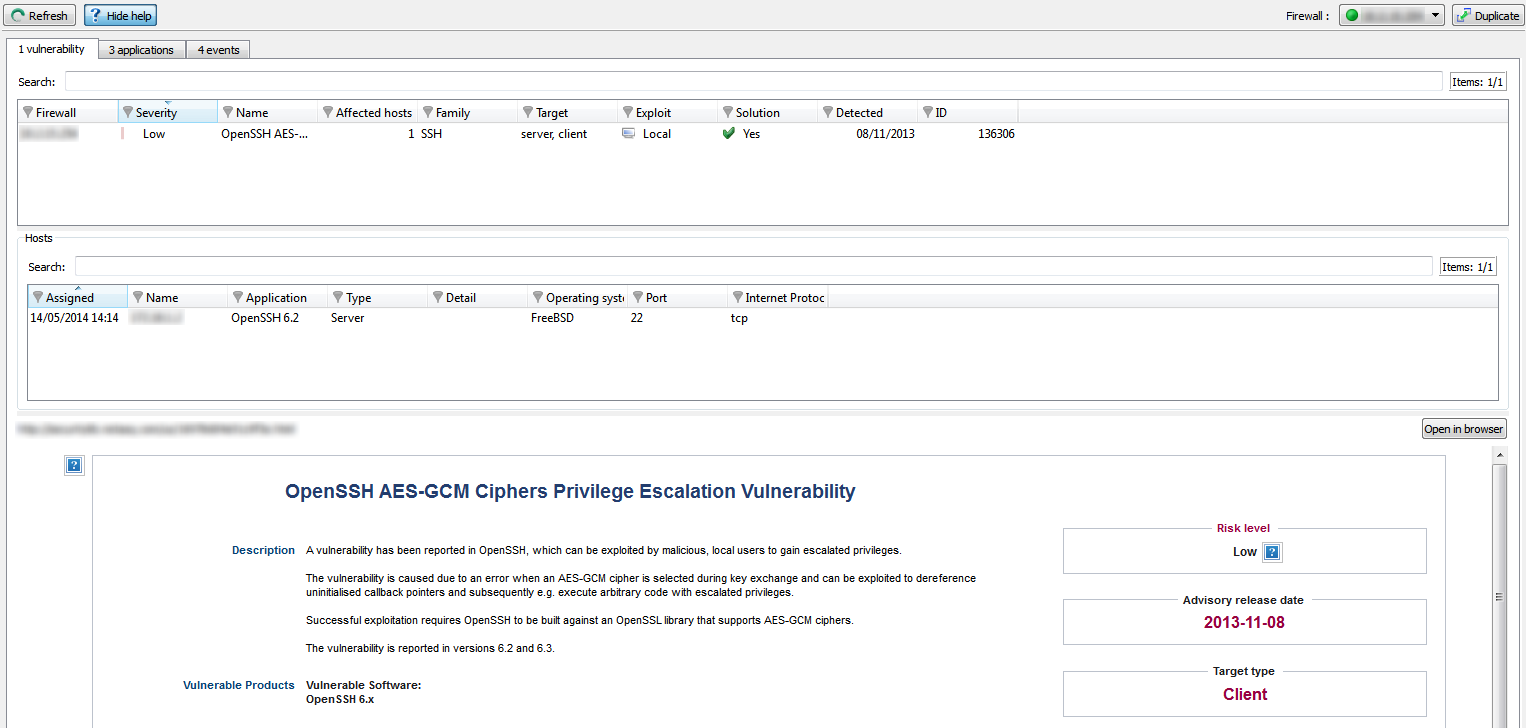
Figure 32: Help
"Applications" tab
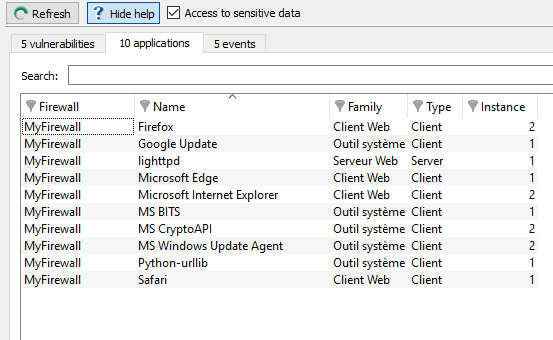
Figure 33: Vulnerability Manager - Applications
The Applications tab provides information on the application detected within the enterprise.
Two types of application may be detected:
- Products: these are client applications installed on the host (e.g.: Firefox).
- Services: these are server applications that are attached to a port (e.g.: lighttpd).
Using information detected by the ASQ engine, Stormshield Network Vulnerability Manager generates information about the detected applications. The design of this feature allows grouping applications by family, so by pairing such information with the vulnerability database, Stormshield Network Vulnerability Manager also suggests probable security loopholes linked to these applications.
This tab offers features that include filtering, optional column display, resizing to fit contents and copying of data to the clipboard. It displays information on the detected applications through the columns that can be seen in the window below:
This screen consists of 2 views:
- A view that lists the applications.
- A detailed view that lists the hosts.
“Application(s)” view
This view allows you to see the applications that the firewall detects. Each line represents an application.
REMARK
The number of applications is displayed in the tab’s name.
The Applications tab displays the following data:
Firewall | Serial number or name (if known) of the firewall. |
Name | Name of the software application. The version is not specified except for the operating systems. |
Family | The software application’s family (e.g.: “web client”). |
Type | Software type (Client: the software does not provide any service – Server: the software application provides a service – Operating system). |
Instance | Number of software applications detected in the monitored networks. For a server, the same service may be suggested on several ports. E.g.: an Apache http server which provides its services on port 80 and port 8080 (web proxy) would appear twice. |
"Hosts" view
This view allows you to see all the applications for a given host. Every row represents a host.
The "Hosts" view displays the following data:
Name | Host name. |
IP address | IP address of the host. |
Application | Name of the software as well as its version, if available. |
Type | Software type (Client: the software does not provide any service – Server: the software application provides a service – Operating system). |
Operating system | Host’s operating system. |
Port | Port that the software application uses (if it uses any). |
Protocol | Internet protocol of the software (if it uses any). |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View host,
- Add the host to the Object base,
"Events" tab
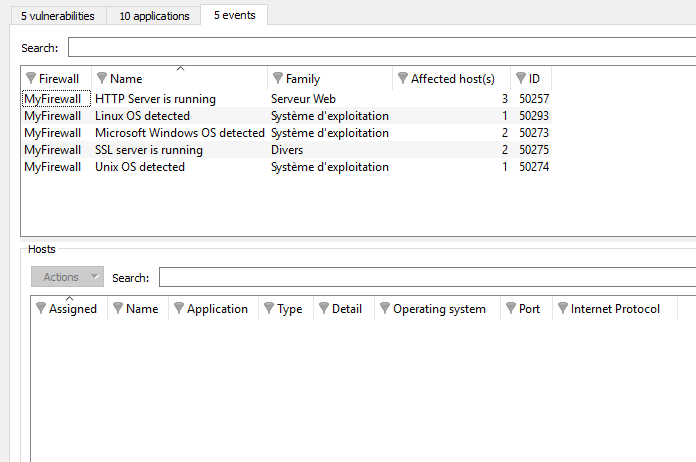
Figure 34: Vulnerability Manager - Events
The Information tab informs you of your network’s activity. You can therefore see the programs that are at risk of generating attacks.
This screen consists of 3 views:
- List of programs.
- List of hosts.
- Help zone.
“Events” view
This view allows you to see all the events that the firewall detects. Each line represents an event.
REMARK
The number of events is displayed in the tab’s name.
The “Information” view displays the following data:
Firewall | Serial number or name (if known) of the firewall. |
Name | Name of the detected OS or a server (e.g.: SSH server). |
Family | Host family.
Example SSH |
Affected hosts | Number of hosts affected. These hosts are identified in the Hosts view in this tab. REMARK The number of hosts indicated in the column "Affected hosts" is not always the same as the number of elements indicated in the "Hosts" zone in this window. In fact, the same service may use several ports. For example, the service thhtpd_server_2.25b can listen to 2 different ports, thus increasing the number of elements. |
ID | Identifier. |
"Hosts" view
This view allows you to see all the events for a given host. Every row represents a host.
The "Hosts" view displays the following data:
Assigned | Date and time of the event’s occurrence. |
Name | Host name. |
Address | IP address of the host. |
Application | Name of the software as well as its version, if available. |
Type | Software type (Client: the software does not provide any service – Server: the software application provides a service – Operating system). |
Details | Details about the operating system. |
Operating system | Host’s operating system. |
Port | Port that the software application uses (if it uses any). |
Internet Protocol | Internet protocol of the software (if it uses any). |
The Actions button makes it possible to perform certain actions on the selected event (for further information, please refer to the section Pop-up menu on rows):
- View host,
- Add the host to the Object base,
Help zone
The help zone allows you to get more details relating to the attack. Thus the administrator can correct the vulnerability.
Click on the Show help button to show or hide the help zone associated with an event.
Typically, help comes in the form of a descriptive file that contains explanations, links to the publisher’s site or to bug fixes.
REMARK
Refer to the Stormshield Network Security user guide to configure Vulnerability Manager.