Information prior to an update of the SMC server
Updates to version 3.7 - Connecting SNS firewalls to SMC
If in an earlier version of SMC, you had used the same connecting package to connect several firewalls, they may have taken turns to connect to SMC under the same name. Furthermore, version 3.7 could prevent them from connecting. To restore the configuration before the update to version 3.7:
-
Generate a new connecting package for each firewall.
-
Install it on the corresponding firewall.
The command smc-import-firewalls /data/tmp/filename.csv --package-only can be used to generate several packages at one go.
If after an update to version 3.7, a firewall is still unable to connect to SMC:
-
Select Allow another firewall to connect with the same package as part of a defective hardware replacement (RMA) in the System > Configuration tab of the firewall properties in the SMC interface.
If the issue affects several firewalls:
-
Log in to the SMC server via the console of your hypervisor or in SSH.
-
Disable the firewall serial number verification feature, by using the environment variable SMC_LOCK_SERIAL_NUMBER_ENABLED=false in the file /data/config/fwadmin-env.conf.local.
-
Restart the server with the command
nrestart smc. -
When all firewalls have been able to reconnect, enable the firewall serial number verification feature again by using the environment variable.
Managing dynamic routing from SMC
As of SMC version 3.6, when an SNS firewall is being updated to version 4.8.1 EA or higher, SMC automatically downloads the firewall's local dynamic routing configuration when it reconnects after the update.
As a result, Stormshield advises against making changes to a firewall's dynamic routing configuration between the end of its update and its reconnection to SMC.
Managing the configuration of SNS firewall network interfaces during an update from a version previous to 3.4 to a version higher than 3.4
After an update to a version higher than 3.4, the SMC server needs to retrieve again the configuration of interfaces and routing of SNS firewalls.
As such, please take note of the following points:
-
Before updating SMC, make sure you deploy the current changes to the firewall network configuration. Otherwise, changes will be lost.
-
Interface and route configuration remains read-only on SMC as long as the SNS firewall does not reconnect to SMC after the update.
After updating to a version higher than 3.4, if you manage a pool of over 200 firewalls, synchronizing the network configuration of SNS firewalls can cause the system to slow down. If this occurs, we recommend that you temporarily disable the consistency checker before updating SMC, and enabling it again later. To do so:
- Log in to the SMC server via the console of your hypervisor or in SSH.
- In the file /data/config/fwadmin-env.conf.local, add the environment variable: FWADMIN_ENABLED_CFGCHECK=false (replaced by the variable SMC_CFGCHECK_ENABLED from version 3.4 onwards).
- Restart the server with the command
nrestart fwadmin-server. - After the update, once all the firewalls are connected back, delete the line in the file and restart the server.
Interfaces with network or broadcast addresses
SMC no longer allows interfaces to be created with network or broadcast addresses, to ensure that interfaces correspond to SNS firewalls.
Before updating SMC, ensure that you do not have such interfaces in your configuration. Otherwise, the SMC administration interface will become unusable, and you will need to restore a snapshot or shadow copy of your virtual machine.
Size of the System disk
After successive updates of the SMC server, it may happen that free space on the System disk is not enough to allow new updates to be installed:
-
Use the following command to check the state of the system disk:
df -h /
For example:
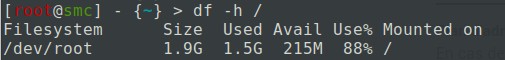
-
If the disk is almost full, you need to deploy a new virtual machine using the following procedure:
-
Back up the 3.x SMC server configuration.
-
Shut down the SMC server.
-
Deploy a new SMC server in the same 3.x version.
-
Restore the the configuration from your backup on the new virtual machine.
-
-
Update your new SMC server to the new 3.y version.
EXAMPLE
To update from a 3.1.4 version to a 3.1.6 version:
Back up the 3.1.4 SMC server configuration.
Shut down the server.
Deploy a new 3.1.4 server.
Restore the backed up configuration on the new 3.1.4 server.
Update the new server to version 3.1.6.
To get help or more information on these procedures, please refer to the SMC Administration guide or contact the Technical Assistance Center.../SMC Administration Guide/getting started.htm
Access to the SMC server during updates
When you update your SMC server, we recommend that you prevent other administrators from accessing SMC for the duration of the update. If you do not do so, they will not be informed of updates in progress and any configurations they are working on will not be saved.
Minimum hardware recommendations
Refer to the section Adapting the size of the virtual environment according to the number of SNS firewalls in the SMC installation guide to correctly scale your virtual environment.
Warning before connecting SNS firewalls to the SMC server
Take note of the following information if you wish to associate the SMC server with a pool of SNS firewalls already used in production, and which contain global configuration items.
Whenever SMC deploys a configuration on a firewall, all global configuration items found on this firewall will be deleted and replaced with configuration items defined in the SMC configuration, if any.
This includes:
- Global objects defined on the firewall,
- Global filter rules defined on the firewall,
- Global VPN tunnels defined on the firewall.
These items are not displayed by default in the SNS web configuration interface. To display them, go to the firewall Preferences, Application settings section and enable the option Display global policies (Filter, NAT, IPsec VPN and Objects).
By connecting an SNS firewall to SMC, you therefore accept that these global items, which could have been set up on this firewall, will be overwritten as soon as SMC deploys the configuration.
However, local objects, rules and VPN tunnels (which you handle by default in the firewalls' web administration interface) will never be modified or deleted when SMC deploys a configuration.
We therefore recommend that you recreate these global items in the form of local items on the firewall or rewrite rules in SMC before connecting the firewall to SMC, in order to avoid losing configuration items and disrupting production.
In most cases, in which the firewall to be connected does not have any global configuration items, no particular precautions need to be taken in connecting the firewall to SMC, and doing so will leave no impact on production.
In any case, we advise you to back up your firewall's configuration before connecting it to SMC.