Managing Radius users
The SMC server can be connected to a Radius server to authorize the company’s users to manage a pool of firewalls.
This type of authentication is intended to work with a Radius or FreeRADIUS server on Microsoft Windows Server 2016, 2019 and 2022.
Authentication via Radius server is configured in the SMC web administration interface.
To authorize administrators to connect to the SMC server via a Radius server, follow the three steps below:
- Configure the connection to the Radius server,
- Test the connection to the server,
- Authorize users and define their access privileges.
To configure and enable the connection to a Radius server:
- Go to Maintenance > SMC Server > Administrators, and click on Edit local authentication settings,
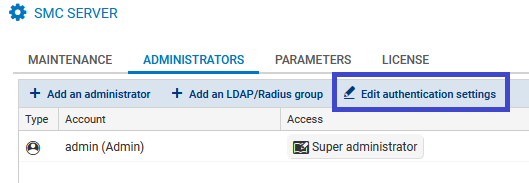
- In the Radius tab, select Radius authentication enabled.
- Fill in the following fields:
Field Description Main server Host IP address or FQDN of the main Radius server.
If the server’s FQDN is used, the DNS service must be configured beforehand.Port Port number to access the Radius server: 1812 by default Pre-shared key Secret key shared to enable authentication on the server
Backup server - Optional Host IP address or FQDN of the backup Radius server.
If the server’s FQDN is used, the DNS service must be configured in advance.
Port Port number to access the Radius server: 1812 by default Pre-shared key Secret key shared to enable authentication on the server
To allow Radius users to authenticate on the SMC server, the super administrator must add them to the list of administrators in the web administration interface.
-
Go to Maintenance > SMC Server > Administrators, and click on Add an administrator.
-
Fill in the following mandatory fields:
-
Select the access privileges. For more information, refer to the section Managing administrator privileges as super administrator and the section Restricting folder administrators' access privileges.
-
Unselect This administrator can use local authentication if you do not wish to define local authentication for the Radius user.
| Field | Description |
|---|---|
| ID |
Identifier of the Radius user. |
| Name | Name of the Radius user shown in SMC. |
The following terms are reserved on SMC, so cannot be used as IDs: root, daemon, bin, sys, sync, games, man, lp, mail, news, uucp, proxy, www-data, backup, list, irc, gnats, sshd, dhcpcd, messagebus, fwadmin-server, nobody.
NOTE
The IDs of users authenticated via the Radius directory must not contain spaces in order to be able to connect to the SMC server.
Users can belong to Radius groups.
To add a Radius user group:
-
In the Maintenance > SMC server > Administrators menu, click on Add an LDAP/Radius group.
-
Fill in the following mandatory fields:
-
Select the access privileges. For more information, refer to the section Managing administrator privileges as super administrator.
| Field | Description |
|---|---|
| Radius identifier |
Identifier of the Radius group. |
| Name | Name of the Radius group. |
If an administrator has a personal account in his/her name, and is also a member of one or several groups, the privileges that apply will be those assigned to the personal account.
NOTE
The IDs of users authenticated via the Radius directory must not contain spaces in order to be able to connect to the SMC server.