Configure network interfaces
From the SMC server, configure your firewalls’ network interfaces.
To perform these operations, you need to hold write access privileges on the folders in question in the SMC web interface. For more information, refer to the section Restricting folder administrators' access privileges.
Go to the System > Configuration tab of the firewall in question and select Configure the network for this firewall in SMC to indicate that SMC manages the network for this firewall.
Next, go to the Interfaces > Interfaces and Interfaces > IPsec interfaces (VTI) tabs to configure the interfaces.
If this option is not selected, SMC will not manage the network for this firewall and the firewall’s Interfaces tab will be in read-only mode.
If you select this option when a firewall is already part of a route-based VPN topology, any associated IPsec interfaces (VTI) that are missing will automatically be created and shown in the IPsec interfaces (VTI) tab. For further information, refer to the section Configuring Ipsec interfaces (VTI).
When the Interfaces tab is in read-only mode, SMC retrieves the firewall's interfaces every time the page of the firewall's settings is opened. This is not the case when routing and network configuration is managed by SMC.
In the firewall's settings, you can then force the retrieval of the interface and routing configuration:
-
Go to the firewall's settings,
-
In the System > Configuration tab, select Configure the network for this firewall in SMC if it has not already been selected,
-
Expand Firewall information and configuration retrieval (advanced) and click on Retrieve configuration of interfaces and routing.
When you force a firewall's interfaces to be retrieved, and if the firewall has virtual IPsec interfaces (VTI), we recommend that you look up the server's logs to ensure that there is no conflict in the interface name, IP address or mask between the IPsec interfaces created on SMC and the IPsec interfaces created on the firewall. Identical names or addresses may delete interfaces used in routes or rules.
The SMC server automatically displays the interfaces of your firewall in the Interfaces > Interfaces tab in the firewall's settings. You will then be able to configure them from a central point, or add them manually. For more information on interface configuration, refer to the Interfaces section in the SNS User guide.
SMC makes it possible to configure the following network interfaces in IPv4:
-
Ethernet interfaces
-
Bridges
-
VLANs
-
Aggregates
There are three possible aggregate modes:
-
LACP, which is the default mode.
-
Failover, only on SNS firewalls in version 4.3 and higher.
-
Broadcast, only on SNS firewalls in versions 4.3.25, 4.7.5, 4.8.1 and higher.
The interfaces that SMC does not support can also be retrieved in read-only mode (Wi-Fi, dialup, Loopback, GRETUN, GRETAP and USB/Ethernet). These interfaces are shown as Other interface in the grid.
They cannot be changed from SMC but can be used in the routing configuration.
When SMC retrieves the routes displayed in a firewall's Routing tab, the interfaces will also be retrieved automatically. If any interfaces were created on SMC but were not deployed, they will be overwritten when routes are retrieved.
When deploying the network configuration, the existing VLAN, aggregate and bridge interfaces on the firewall are not preserved. The network configuration deployed from the SMC server will overwrite the local configuration on the firewall.
Limitations to the configuration of interfaces from the SMC server
-
Currently, configuration in IPv6 is not supported.
-
High availability: The network interfaces used for high availability links are shown on the SMC server but cannot be configured.
-
Monitoring: Currently interfaces cannot be monitored from the SMC server. To monitor the interfaces of a firewall, connect to the firewall in question.
-
Configuring modems: Currently, the Safety/Bypass mode is not supported.
-
For interfaces configured in DHCP, SMC does not display their values in detail.
-
Bridge: A bridge can be modified and deleted even if it contains interfaces that are not managed by the SMC server.
-
GRE/GRETAP interfaces are not supported. VLAN interfaces connected to a GRETAP are therefore not displayed on the SMC server.
The SMC server automatically displays the IPsec interfaces of your firewall in the Interfaces > IPsec interfaces (VTI) tab in the firewall's settings. You will then be able to configure them from a central point. The firewall must be in at least version 4.2.3.
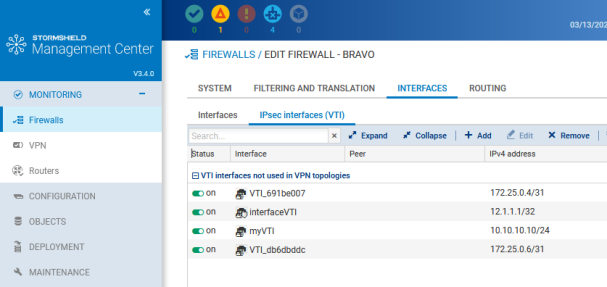
The IPsec interfaces on firewalls can be used in route-based VPN topologies, and in the configuration of routes and policy-based routing filter rules.
For more information on IPsec interfaces, refer to Creating or modifying an IPsec interface (VTI) in the SNS user guide and in the technical note IPsec virtual interfaces.
IPsec interfaces shown in SMC originate from three different sources, and behavior may vary depending on whether the firewall's network configuration is managed by SMC or not:
| The firewall belongs to a route-based VPN topology |
SMC will automatically create the associated IPsec interfaces if SMC manages the firewall's network configuration. The interfaces are classified by VPN topology in the grid. They can neither be modified nor deleted. The See VPN configuration button makes it possible to go to the configuration panel of the VPN topology in question. |
| The IPsec interfaces were created on the firewall |
SMC will retrieve them automatically during the migration from SMC version 3.3 to version 3.4, even if SMC does not manage the firewall's network configuration. If SMC manages the firewall's network configuration, you can force the interfaces to be retrieved at any time, as explained in Configure network interfaces. If they are used in a route-based VPN topology created from SMC, they will be associated with the topology in question in the grid of the IPsec interfaces (VTI) tab. If the network configuration is managed by SMC from version 3.4 onwards, we recommend that you no longer create IPsec interfaces directly on firewalls, as they will be overwritten the next time the configuration is deployed. |
| IPsec interfaces were created manually from SMC |
This can be done only if SMC manages the firewall's network from version 3.4 onwards. |
You can modify or delete IPsec interfaces only for firewalls for which SMC manages the network configuration, and if they do not belong to a route-based VPN topology.
As for IPsec interfaces used in route-based VPN topologies, some changes made in a topology may have an impact on the configuration of IPsec interfaces. In this case, the impact will immediately be replicated on the IPsec interfaces of firewalls for which SMC manages the network configuration.
As for firewalls with network configurations that SMC does not manage, changes made in a topology have the following consequences:
-
If a topology is deleted, the associated IPsec interfaces will not be automatically deleted,
-
If you change the name of a topology or a peer, the comment associated with the IPsec interface and shown in the IPsec interfaces (VTI) tab will not be automatically updated,
-
If you change the VTI network pool of the topology, IP addresses of IPsec interfaces will be modified, and you must replicate the change manually on SNS firewalls.