Filtering applications via command line arguments
In application IDs, you can indicate command line arguments as an identifying criterion.
This criterion makes it possible to apply different rules to the same application, depending on how it is used, to gain better control over the use of certain applications.
EXAMPLE
With this type of filtering, you can prevent PowerShell from running only when it is run as an invisible process, or when its command line arguments attempt to bypass Windows execution policies. Such behavior may indeed be deemed malicious.
Managing compatibility with agent versions
This feature can be used with agents in at least version 2.2.2. If a group of agents in a version lower than 2.2.2 applies a policy that contains application IDs using the Command line criterion, indicators will appear in various parts of the console to indicate incompatibility. For more information, refer to the section Managing a pool with agents in different versions.
To make your agent pool support this feature, the SES Evolution release notes explain the procedure of updating built-in security policies and agent pools in
Using the Command line criterion in an identifier
To create an application identifier based on command line arguments:
- Select a policy in Security > Policies, then select a set of rules.
- Click on the Identifiers tab at the top right, then on the Application IDs tab.
- Click on Edit in the upper banner, then on Add an ID.
A blank ID appears below the existing IDs. - Click on Edit at the bottom right.
- In the field New application ID, enter an ID name, then a description if needed.
- Click on
 and select Command line.
and select Command line. - Click outside the criteria window.
- Click on Edit.
- Enter a name and select a mode:
- Custom parameters (default mode): customize the parameters that the rule must search for in a command line.
Contains at least one parameter: the rule will apply every time it finds command lines containing at least one parameter.
Without any parameter: the rule will apply every time it finds command lines that do not contain any parameters.
- If you have chosen Custom parameters mode, you will create one or several specifications by selecting options on the left, and by indicating command line parameters in the field on the right. If you are creating several specifications, they are linked by logical “AND” operators. This means that the rule using this identifier will apply if all the specified conditions are met.
- Choose from the following options:
General Not The rule applies to all command lines that do not contain the parameter(s) indicated in the field on the right. Case sensitive The rule applies only when it finds the parameter(s) in the case specified indicated in the field on the right. Command After the specified parameter, the rest of the command line is interpreted as a nested command line. Such command lines are introduced with the -Commandparameter for PowerShell or the/cparameter for cmd for example.Parameter type String The parameter is a character string. Flag The parameter is found in a command line option beginning with
/or-for example.To create an identifier corresponding for example to the editor of the registry that silently runs a .reg file, i.e. regedit /s in command line:
Create a Path criterion and enter
*\regedit.exe.Create a Command line criterion, select the Flag and Is equal to options, then enter
sin the field on the right.
The
/or-characters do not need to be entered.Take note that the double dash
--is not supported. For example, to search for the--argargument, you must select String as the type of parameter.Check Is equal to The parameter must be the same as the character string indicated in the field on the right. Begins with The parameter must begin with the character string indicated in the field on the right. Ends with The parameter must end with the character string indicated in the field on the right. Contains The parameter must contain the character string indicated in the field on the right. Is prefixed with The value that the rule recognizes rule may be a prefix of the character string indicated in the field on the right. For example, the character string “version” will match the values "v", "ve", "ver", etc., up to “version”. Position (visible from the second specification onwards) None There is no position criterion. Followed by The parameter searched for follows the previous parameter. Immediately followed by The parameter searched for immediately follows the previous parameter. - Enter one or several parameters in the field on the right. In the same specification, parameters are linked by logical “OR” operators. This means that the rule using this identifier will apply if at least one of the specified conditions is met.
- Choose from the following options:
-
When you have created all the specifications, confirm the creation of the “Command line” criterion.
-
Confirm the creation of the identifier.
Use case
As part of SES Evolution‘s anti-ransomware protection mode, this criterion type makes it possible to set Process creation rules on applications that may attempt to delete Windows shadow copies, among other operations. However, these shadow copies must be protected so that files encrypted by a ransomware program can be retrieved. For further information, refer to Managing ransomware attacks. These rules are included in the built-in Anti-ransomware protection rule set.
EXAMPLE
The use of VSSAdmin to manage Windows shadow copies can be allowed in your pool, except when it attempts to delete a shadow copy, for example. Indeed, a ransomware program may carry out such an action.
In this case, create an application ID by indicating the following values for the Path criterion: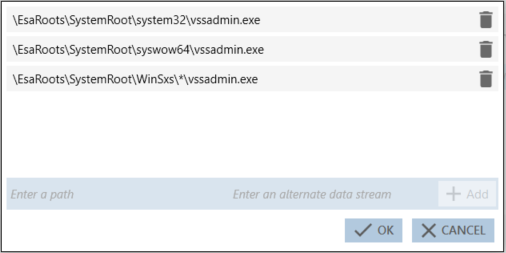
Next, indicate the following values for the Command line criterion: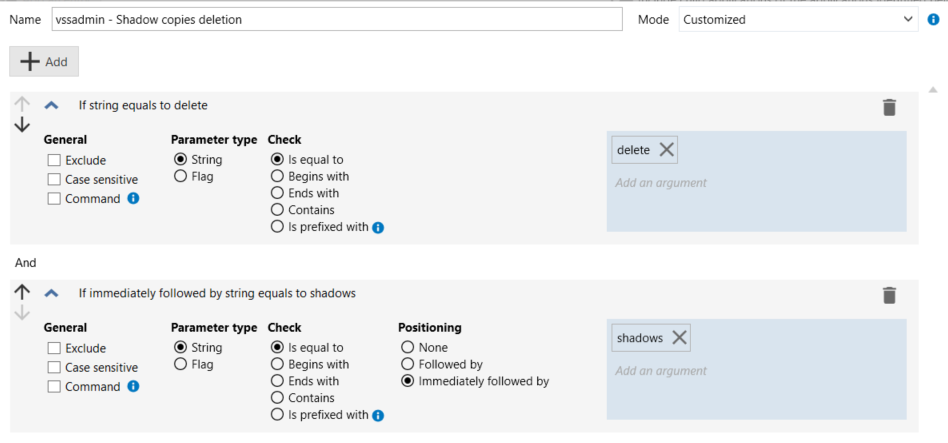
The ID will then include the following entry: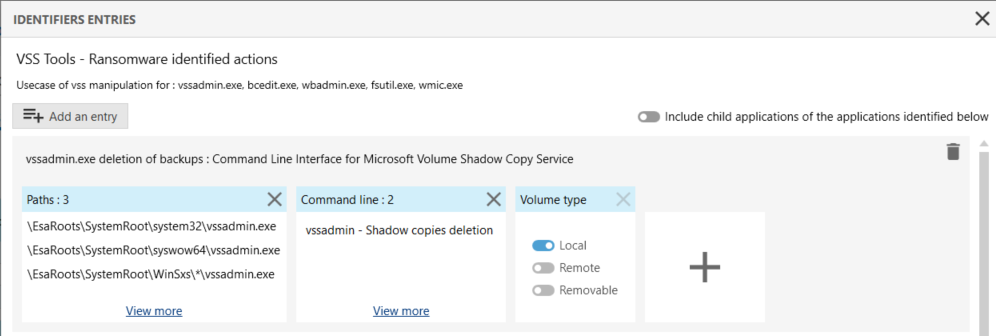
The ID can then be used in a blocking Process creation rule that kills the VSSAdmin application when it detects an attempt to delete a Windows shadow copy.