Forwarding Windows events in SES Evolution
The forwarding of Windows events consists of indicating in a rule which logs and which Windows events SES Evolution must collect and display.
EXAMPLE
You can choose to forward events relating to user connections on workstations, to monitor who logged in and when.
Create an event forwarding rule:
- Select the Security > Policies menu and click on your policy.
- Select an audit rule set.
- Click on External events > Event forwarding.
- If you are in read-only mode, click on Edit in the upper banner.
- Click on Add > Rule (Event forwarding).
A new line is displayed. - Click on + Monitored events and provide the following information:
 Log name
Log nameEnter the name of the Windows log, e.g., Security, Microsoft-Windows-Windows Defender/Operational. To find out the name of a log, look up its properties in the Windows Event Viewer.
You can monitor a log that is not enabled in Windows. In this case, SES Evolution will automatically enable it. However, keep in mind that if there are too many events in this log, it may impact the performance of Windows.If you enter a filter request in XML in the next field, the Log name is not completely necessary.
 Filter request
Filter requestIf needed, enter a filter request to collect only some events in the log. To obtain a request:
- Open the Windows Event Viewer.
- Right-click on the log of your choice > Filter the current log.
- In the Filter tab, select your filtering options.
- Copy the contents of the XML tab and paste it in the Filter request field in the window of the event forwarding rule.
You can also manually enter a request in XPath. Enter for example the log name Security and the filter request *[System[(EventID=4625)]] to retrieve all events with the ID 4625 in the Security log.
 Description
DescriptionEnter a description if necessary.
You can also import a custom Windows events view, which will automatically fill in all fields with the desired values. To do so, go to the Windows Event Viewer and export the desired custom view in XML, and import it by clicking on the arrow on the right
 .
.EXAMPLE
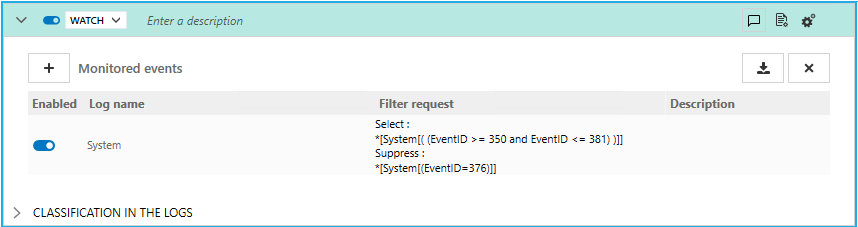
Here, the event IDs 350 to 381 in the System log will be forwarded, except for ID 376.
- In the upper banner in the rule, you can:
- Select the log settings that this rule will send. The severity of a log depends on its severity in Windows. Both severity levels are mapped as follows:
Windows event type SES Evolution log Audit Information Critical Critical Error Error Warning Warning Information Information Verbose Diagnosis - Specify whether an action must be performed when a log is sent for this rule.
- Enter a description to explain what this rule aims to achieve.
- Enter a comment.
- Select the log settings that this rule will send. The severity of a log depends on its severity in Windows. Both severity levels are mapped as follows:
- Add other event forwarding rules if necessary.
- Click on Save at the top right of the window to save changes.
SES Evolution makes up for the Windows events that were generated when it was inactive, such as when the machine is restarting.