Adding exceptions for logs
If, after analyzing a log, you consider that the action that triggered it was not malicious and should not have been blocked, you can add an exception to the log. Doing so will prevent this action from being blocked and/or logged again in the future. Likewise, if you think that a file was wrongly quarantined, add an exception on the quarantine log.
Adding an exception creates a new exception rule in the exception rule set of your choice.
- In the Environment > Agent logs panel, select one or more logs you no longer wish to generate.
- Right click, then click Add exceptions. The Create Exception Rules wizard appears, allowing you to view the rule(s) that will be created by SES Evolution.
- Expand the various boxes to display all the information on the rules. The policy(ies) affected by these rules are visible in the top right-hand corner.
- Change the rules as you see fit:
- In the Rule set drop-down list, select the rule set in which the exception rules will be created: an existing Exceptions-type rule set, or a rule set created for the occasion with the label NEW.
Click the Pencil button to edit the rule set name and type, or click the Eye button to view the rule set. - Uncheck the rules or rule groups that you do not want to create.
- If necessary, change the rule intent, comment, application ID, or behavior for each action. For more information, see Defining access control rules
- Click the
 button of a rule to reset its original values.
button of a rule to reset its original values.
NOTE
If an identical exception rule already exists for the selected logs, it cannot be modified in the wizard, but you can modify it by clicking on the button to navigate to the rule.
button to navigate to the rule. - In the Rule set drop-down list, select the rule set in which the exception rules will be created: an existing Exceptions-type rule set, or a rule set created for the occasion with the label NEW.
- Click Validate.
This will automatically:- Add one or more rules to the selected exception rule set. These rules ensure that a blockage does not occur in identical circumstances. The application or file IDs required for the rules are also created if necessary.
- Assign a False positive status to the log in question, and identify the user who added the exception.
- Add the comment “Automatic exception created from this log” to the log.
- In an exception on a quarantined file, the file will automatically be restored at its original location the next time the environment is deployed.
- If required, you can view or modify the exception rule created from the log:
- Display your log by enabling the False positive filter.
- Hover over the three dots to the right of the log line and select the View exception rule menu.
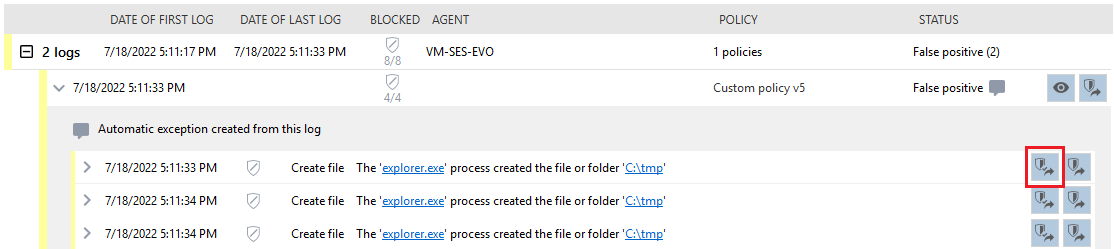
The exception rule that matches this log is displayed. It is distinguished from other rules by a blue bar on the left.
If the rule cannot be found, it has been deleted in the meantime.
Special cases
-
If you request the creation of exceptions on several similar but not identical logs, the wizard displays an exception rule for each log:
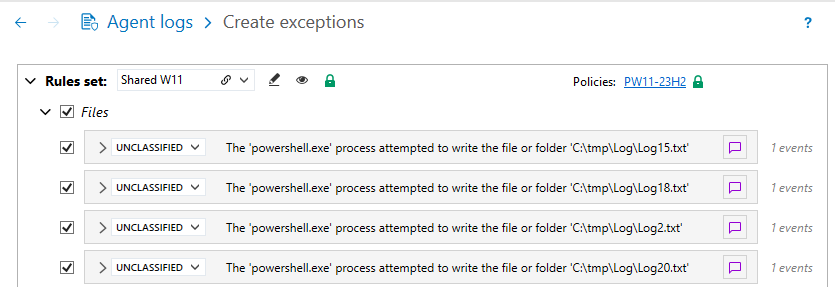
In this case, you can change the ID of one of the rules to extend it to other similar rules using the wildcards * and ?.
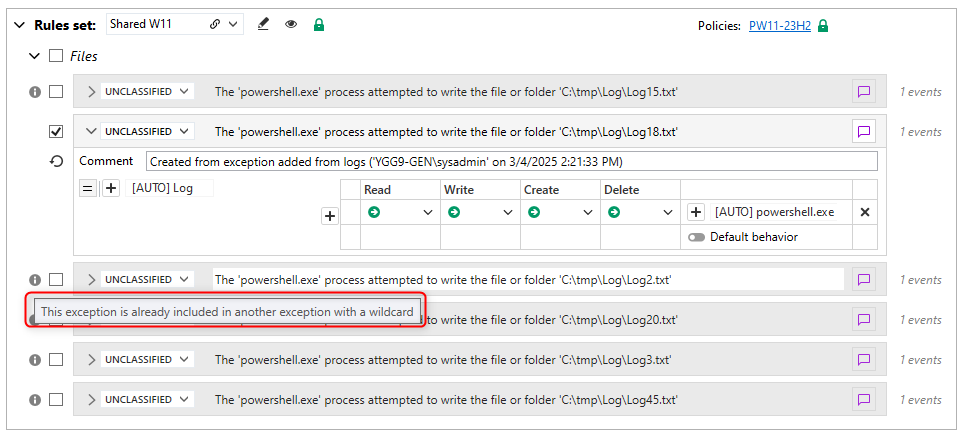
In the example above, you can change the file ID to c:\tmp\Log\Log* to include all similar logs in the same exception rule.Other similar rules that match the new ID are automatically deselected in the wizard, and become false positives after validation.
-
If the selected log is linked to a policy that no longer exists, you are notified and can choose whether or not to set the log to False positive status by activating the Set event as false positive button.