Enabling an authentication method
The SSO Agent authentication method must be configured on your firewall so that users can authenticate on an authentication domain. You can configure up to five SSO Agent authentication methods.
- Log in to the firewall's administration interface: https://firewall_IP_address/admin,
- Go to Configuration > Users > Authentication, Available methods tab.
- Click on Add a method or Enable a method (according to the version installed on the SNS firewall) and select SSO Agent in the drop-down menu.
- In the section on the right, select the relevant authentication domain from the drop-down list in the Domain name field.
- Continue with the configuration section by section according to the parameters below.
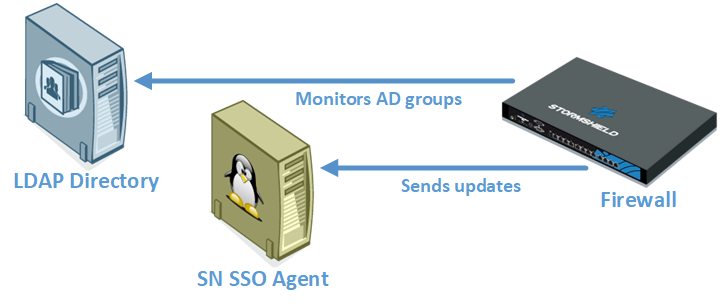
Enter the information about the main SN SSO Agent:
| Field | Details |
| IP address |
Select from the list the host object that corresponds to the SN SSO Agent created earlier. |
| Port |
Leave the object agent_ad selected by default. |
| Pre-shared key |
Enter the SSLKey defined when SN SSO Agent was installed. This key is used to encrypt exchanges between SN SSO Agent and the firewall in SSL. The strength of the pre-shared key indicates the password’s level of security. |
Add all the LDAP directories that control the authentication domain concerned. They must be saved beforehand in the firewall’s Network objects database. For more information, refer to the section Creating network objects.
Mode: since SN SSO Agent is installed on a Linux machine, select Syslog server mode.
Syslog server configuration:
| Field | Details |
| Listening IP address |
Select from the list the host object associated with the machine that hosts SN SSO Agent and its syslog server. |
| Listening port |
Select from the list the port object representing the listening port on the syslog server. The object syslog is selected by default (UDP port 514) |
| IP address search |
Regular expression that will be used to search for IP addresses in logs hosted on the syslog server. For this technical note, we used: ([0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3})\s |
| User search |
Regular expression that will be used to search for user names in logs hosted on the syslog server. For this technical note, we used: DOMAINNAME\\([a-zA-Z0-9\.]*)\s Replace “DOMAINNAME” with the authentication domain used. Remember to protect special characters, if you are using any. |
| Message search |
Regular expression that will be used to search for connection messages in logs hosted on the syslog server. For this technical note, we used: connect\|ok Ensure that the format of this regular expression is correct so that you do not include unnecessary results in the search. |
For more information on these elements, refer to the SNS user guide.
Maximum authentication duration: define the maximum length of an authenticated user’s session. After this period expires, the firewall will delete the user associated with this IP address from its table of authenticated users, logging the user out of the firewall.
This limit is defined in minutes or hours, and is set by default to 10 hours.
Refresh user groups updates: for every LDAP directory configured, the firewall will check for any changes to the LDAP directory groups. The firewall then updates the configuration of its directory, and sends back this information to SN SSO Agent.
This limit is defined in minutes or hours, and is set by default to 1 hour.
Disconnection detection: enable the disconnection method so that authenticated users can be deleted when a host is disconnected or when a session is shut down. If this method is not enabled, the user will be logged out when the maximum authentication period expires, even when the session has been shut down.
SN SSO Agent tests the accessibility of all hosts authenticated on the firewall by pinging them every 60 seconds. To ensure the success of these tests:
- Workstations on the authentication domain must allow responses to pings (ICMP requests). The Windows firewall may block such requests in some cases.
- A rule in the firewall’s filter policy must allow SN SSO Agent to test hosts on the authentication domain if the agent must access it through the firewall.
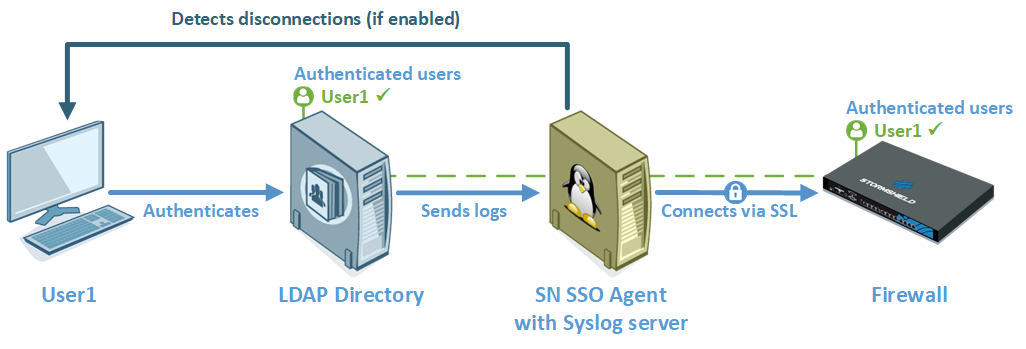
Consider offline after: if a host does not respond within the time frame set in the “Disconnection detection” test conducted every 60 seconds, SN SSO Agent will consider this host offline. The agent will then send a disconnection request to the firewall, which will delete the user from its table of authenticated users, logging the user out of the firewall.
This duration defined in seconds or minutes is set by default to 5 minutes.
Enable DNS host lookup: enable this setting if the hosts connected to the firewall have several IP addresses or their addresses change regularly. This setting may be useful, for example, if your users often switch from an Ethernet configuration to a Wi-Fi connection.
Periodically, SN SSO Agent will perform DNS requests (PTR) to check that machines have not changed their IP addresses. If there is a new IP address, the information will be sent to the firewall. To ensure the success of these tests:
- A Reverse lookup zone (right-click on the folder) must be added to the settings of the DNS server for the authentication domain,
-
A rule in the firewall’s filter policy must allow SN SSO Agent to test hosts on the authentication domain if the agent must access it through the firewall.
Ignored administration accounts: in the firewall’s factory configuration, the authentication of this list of users is ignored. This list contains the usual logins dedicated to the administrator (Administrator and Administrateur by default).
This mechanism was set up because the LDAP directory treats the execution of a service or an application (Run as administrator feature, for example) as an authentication. As SN SSO Agent restricts authentication by IP address, this type of authentication may potentially replace the authentication of the user with an open session.
The pre-defined list of “Ignored Administrator accounts” allows SN SSO Agent to ignore their authentication. Edit it if necessary.