Architectures presented
Scenario 1: distribution of IPsec VPN tunnels
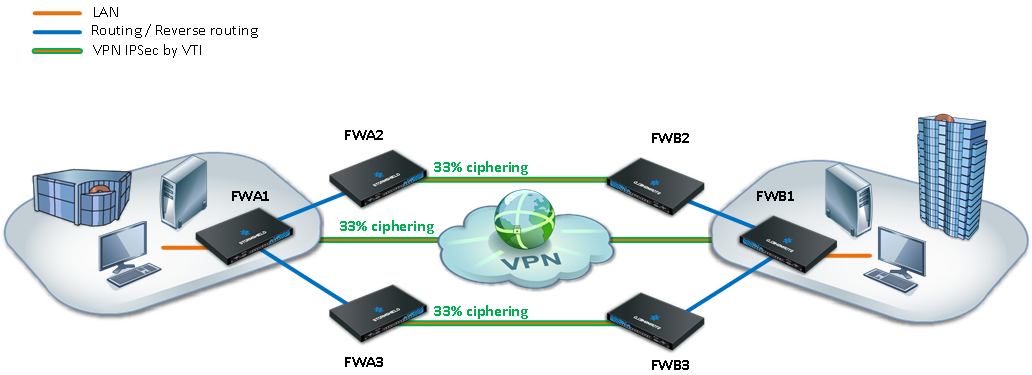
The first scenario shown in this technical note uses router objects and return routes in order to distribute IPsec tunnels over several firewalls, thereby spreading out the system resources needed for encrypting/decrypting data.
In this case, IPsec tunnels are based on virtual IPsec interfaces (VTI - see technical note Virtual IPsec interfaces) so that encryption decisions may be made based on routing instead of the Security Policy Database (SPD), thanks to the concept of router objects. As for return routes, they ensure that response packets are routed to the sending firewall.
The configuration examples shown in this technical note assume that traffic initiated from Site A is going to Site B.
Scenario 2: proxy distribution

The second scenario presented in this document uses router objects and return routes in order to distribute traffic according to type (SSL, HTTP and mail) to proxies enabled on separate firewalls.
Protocol-based routing in the filter policy in this case also relies on the use of router objects. As for return routes, they ensure that response packets are routed to the sending firewall.