Tracking users connected to the SSL VPN on the SNS firewall
In the SNS firewall's administration interface, you can track connected users or those connected to the SSL VPN. In the case of zero trust network access (ZTNA), this section also provides information on how to identify a client workstation's compliance status during a connection to the SSL VPN.
To ensure that images are easier to read, some columns in tables have been hidden. The default layout on your SNS firewall may differ slightly.
Information on access to private data
Some information can be accessed only if the user has been granted permissions to look up private data. If you hold this permission or a code to access private data, click on Logs: restricted access. For further information, refer to the technical note Complying with privacy regulations.
Displaying users currently connected to the SSL VPN
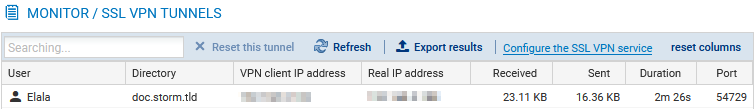
This view shows real-time information on the sessions of users connected to the SSL VPN.
Go to Monitoring > Monitoring > SSL VPN tunnels.
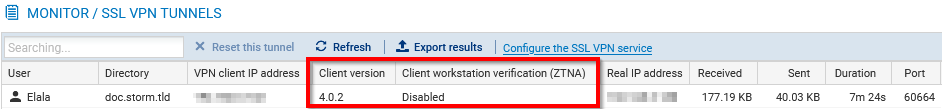
In SNS version 4.8 or higher:
- The "Client version" column shows the version of the Stormshield SSL VPN client used. The value indicated for a third-party or incompatible SN SSL VPN client is N/A.
- The "Client workstation verification (ZTNA)" column shows the client workstation's compliance status. There are several possible values:
- Disabled: the client workstation verification policy has been not enabled,
- Not verified: the SSL VPN client that was used to set up the tunnel is not compatible with the client workstation verification feature, but incompatible clients are explicitly allowed to set up tunnels (permissive mode),
- Compliant: the client workstation complies with the criteria defined in the client workstation verification policy.
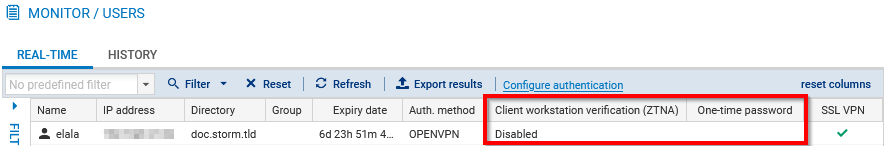
Displaying users currently authenticated on the SNS firewall
This view shows in real-time the users authenticated on the SNS firewall.
Go to Monitoring > Monitoring > Users.
The SSL VPN column identifies users connected to the SSL VPN.
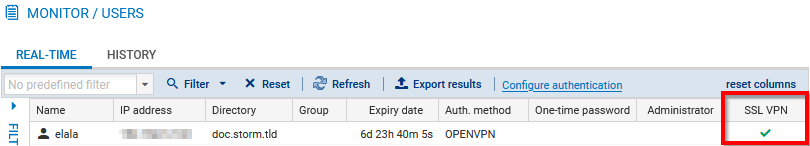
In SNS version 4.5 and higher, the One-time password column indicates whether a user has used a TOTP from the Stormshield TOTP solution to log in.
In SNS version 4.8 and higher, the Client workstation verification (ZTNA) column shows the client workstation's compliance status. There are several possible values:
- Disabled: the client workstation verification policy has been not enabled,
- Not verified: the SSL VPN client that was used to set up the tunnel is not compatible with the client workstation verification feature, but incompatible clients are explicitly allowed to set up tunnels (permissive mode),
- Compliant: the client workstation complies with the criteria defined in the client workstation verification policy.
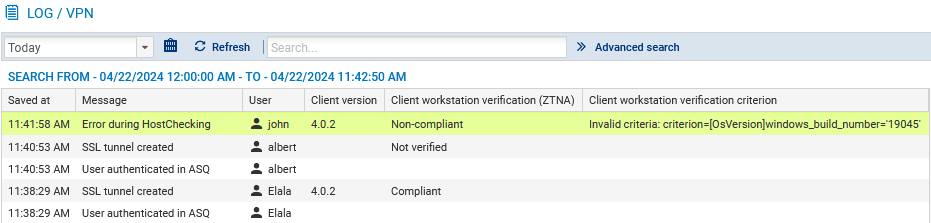
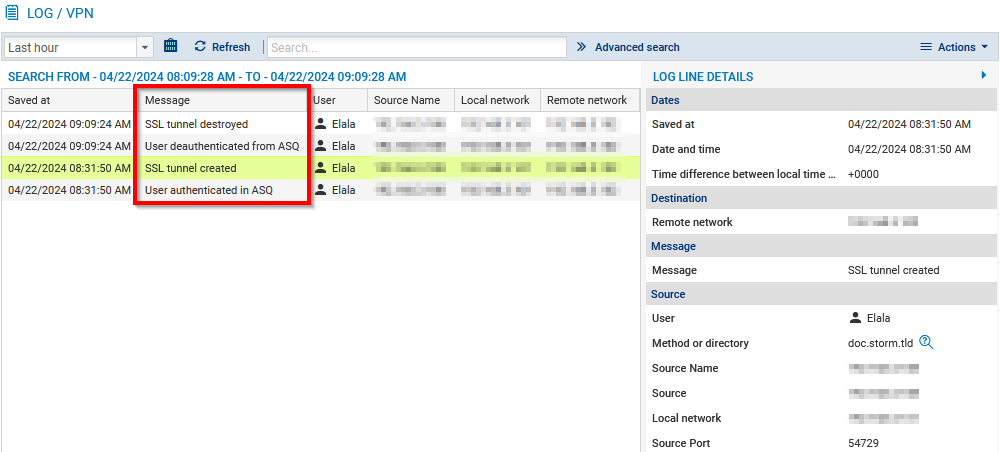
Displaying VPN logs (SSL and IPsec) and identifying the verification criteria that have not been met on a client workstation
This log shows events relating to the various types of tunnels (SSL or IPsec).
Go to Monitoring > Logs - Audit logs > VPN.
The Message and User columns show the user who generated the event and the event message (VPN tunnel connected or disconnected, user authentication in the firewall authentication engine, etc.).
You can view the details of an event in the panel on the right by clicking on it.
In SNS version 4.8 or higher:
- The Message column can contain messages relating to the verification of a client workstation's compliance (HostChecking feature):
“Error during HostChecking” with a “Non-compliant” client workstation: indicates that one or more criteria defined in the client workstation compliance verification policy are not compliant,
“Error during authentication: HostChecking failed” with a “Not verified” client: indicates that the SSL VPN client used is not compatible with the client workstation verification feature, and that the setup of tunnels for incompatible clients is not explicitly allowed (permissive mode),
- The "Client workstation verification (ZTNA)" column shows the client workstation's compliance status. There are several possible values:
- Disabled: the client workstation verification policy has been not enabled,
- Not verified: the workstation's compliance status has not been verified as the SSL VPN client used is not compatible with the client workstation verification feature. To find out whether the tunnel has been set up, refer to the Message column,
- Non-compliant: the client workstation does not comply with the criteria defined in the client workstation verification policy,
- Compliant: the client workstation complies with the criteria defined in the client workstation verification policy.
- The Client workstation verification criterion column shows non-compliant criteria when an SSL VPN tunnel fails to set up due to the non-compliance of the client workstation or user.