Building a customized security policy
After having highlighted the function codes of the industrial protocol circulating on your network, you will now be able to implement an adapted security policy. The various steps that you need to follow are:
- Choose a predefined protocol inspection profile or build a customized profile for the industrial protocol being considered.
- Associate this protocol profile with an application inspection profile.
- Modify the action associated with the "function code denied" alert to make it block such traffic.
- Modify the filter rule dedicated to the industrial protocol in order to call up this application inspection profile.
- In the Configuration > Application protection > Protocols menu, click on Industrial protocols, then click on the industrial protocol to be configured (Modbus in the example). The menu for selecting protocol profiles offers 9 predefined profiles (numbered from 0 to 8) and a customized profile (9),
- By clicking on each of these profiles, view the prohibited or allowed public operations and locate the profile corresponding to the configuration you wish to set up.
- If none of the predefined profiles meet your needs, choose profile "(9)" which will be used during the analysis. Select the action Scan for each public operation to allow. Click on Apply.
- In the Configuration > Application protection > Inspection profiles menu, click on Go to profiles.
- For a more legible configuration, select the IPS profile bearing the same number as the selected protocol profile. For example, if you have chosen to apply the protocol profile titled "Read_write" (profil no. 3) for the industrial protocol being considered (Modbus in the example), select the IPS profile named "(3) IPS_03" which will apply this protocol profile by default.
NOTE
If this profile is unavailable, select an unused IPS profile, then double-click on the application profile applied by default for the industrial protocol and select the profile to use:
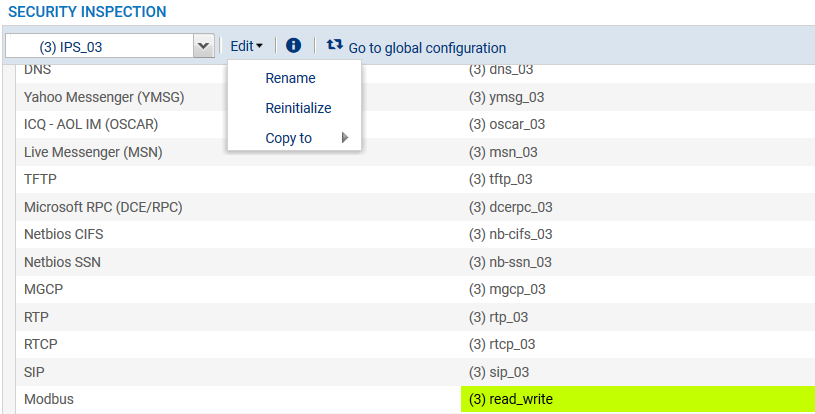
- You can rename this profile in order to give it a more representative name (Edit > Rename menu). Example: "IPS_Modbus_Protocol".
- In the Configuration > Application protection > Applications and protections menu, select the customized inspection profile used in the filter rule (IPS_Modbus_Protocol in the example).
- Enter the name of the industrial protocol to be filtered in the search field. All alarms relating to this protocol will appear.
- Locate the "function code denied" alarm and modify its action by double-clicking on Allow. Select Block.
- Click on Apply.
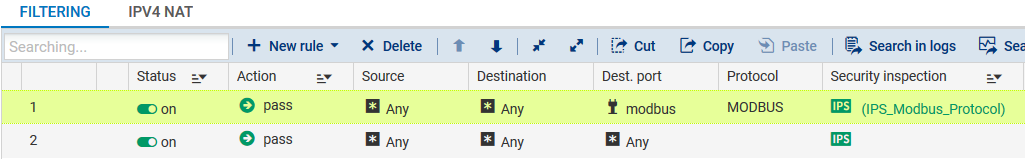
- In the Configuration > Security policy > Filter - NAT menu, select the filter rule created to discover industrial traffic going through the network.
- Double-click on the inspection profile (Security inspection column) and choose the profile selected for the industrial protocol analysis (IPS_Modbus_Protocol in the example).
- Click on Save and apply.
The filter rule will then look like this: