Creating a filter rule using the customized inspection profile
The aim of this rule is to allow all function codes from the selected industrial protocol (Modbus in this document) while systematicaly generating an alarm in order to identify them in the firewall's logs.
NOTE
While this rule is temporary, it needs to be placed at the top of the active filter policy.
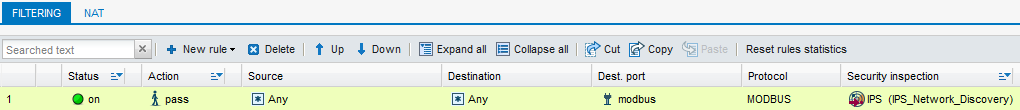
- In the Configuration > Security policy > Filter - NAT menu, select the active filter slot (slot (9] Filter 09 in the example), then click on New rule and select Simple rule.
- In the Status column, double-click on Off to enable the rule (the status of the rule becomes On).
- In the Action column, double-click on block then select the value pass for the Action field:
- In the Port - Protocol section located to the left of the rule editing window, assign the following values to the various fields:
- Destination port: modbus
- Protocol type: Application protocol,
- Application protocol: modbus
- In the Inspection section, select the inspection profile that was renamed earlier ((9)IPS_Network_Discovery in the example):
- Confirm the changes by clicking on OK.
The filter rule will then look like this:
IMPORTANT
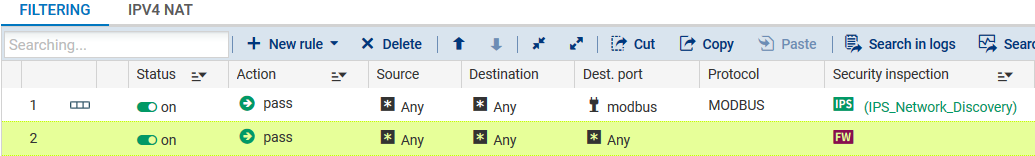
If none of the security policies were enabled on the firewall, a second filter rule must be created to ensure that no traffic outside the Modbus protocol is blocked. This rule will be the last in the filter slot and will have the following values:
- Status: On,
- Action: pass,
- Source: Any,
- Destination: Any,
- Destination port: Any,
- Protocol: leave the field blank,
- Security inspection: select the Firewall mode.
The filter policy will then become:
- Enable the filter policy by clicking on Save and apply.