Filter rules
Create the three rules needed to allow authorized traffic to reach the local network:
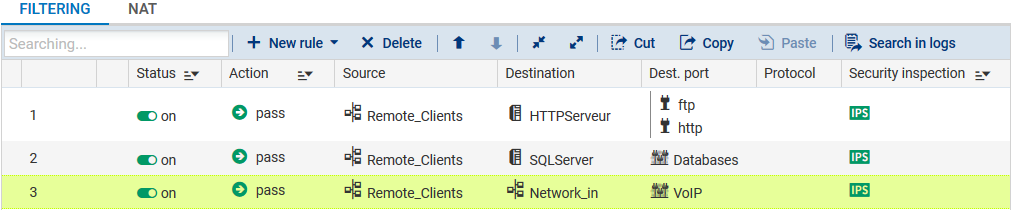
Add a rule using the same following elements:
-
Action (General tab)
In the Action field, select the value Pass
-
Source (General tab)
In the Source field, select the host, host group or network allowed to set up HTTP and FTP connections to the server. In the example, the selected object is the network Remote_clients.
-
Destination (General tab)
In the Destination field, select the host or host group hosting HTTP and FTP services. In the example, the selected object is HTTPServer.
-
Port – Protocol
Select the objects corresponding to the authorized ports. In the example, HTTP and FTP have been selected.
Add a rule using the same following elements:
-
Action (General tab)
In the Action field, select the value Pass
-
Source (General tab)
In the Source field, select the host, host group or network allowed to set up connections to the production server(s). In the example, the selected object is the network Remote_clients.
-
Destination (General tab)
In the Destination field, select the host or host group hosting production services. In the example, the selected object is SQLServer.
-
Port – Protocol
Select the objects corresponding to the authorized ports. In the example, the Databases group is used, which includes various ports for connecting to the SQL database (PostgreSQL, MySQL,etc.).
Create a filter rule using the same following elements:
-
Action (General tab)
In the Action field, select the value Pass
-
Source (General tab)
In the Source field, select the host, host group or network allowed to set up connections to the production server(s). In the example, the selected object is Remote_clients.
-
Destination (General tab)
In the Destination field, select the host, host group or network with which connections will be set up. In the example, the selected object is Network_in.
-
Port – Protocol
Select the objects corresponding to the authorized ports. In the example, a VoIP group is used, containing different ports needed for VoIP.
The configuration of the firewall protecting client workstations is now complete. We will check whether this configuration is operational.