Checking the tunnel setup
From a client workstation located on the Spoke A site, first of all set up a connection to a host on the Hub site (using a ping for example, if you have allowed ICMP in all filtering rules), in order to test the setup of the first tunnel (Spoke A to Hub).
Via the Stormshield Network administration suite
Launch Stormshield Network Real-Time Monitor, log on to the Firewall of the Hub site through the program and click on the module Logs > VPN. Check that phases 1 and 2 took place correctly (message “Phase established”):
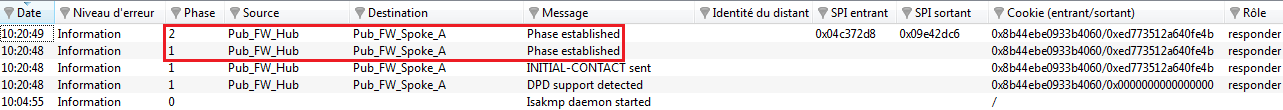
In the module VPN Tunnels, you can also view the first tunnel as well as the amount of data exchanged:
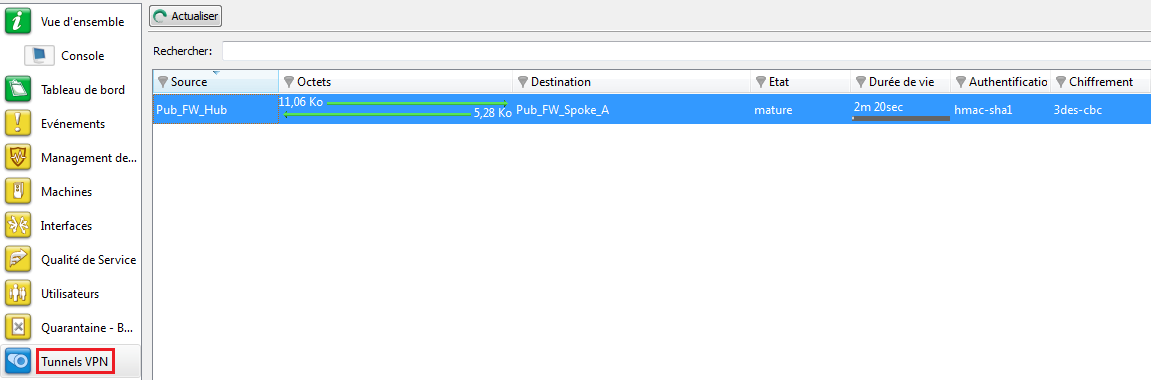
From the same client workstation on the Spoke A site, set up a connection to a host on the Spoke B site, in order to test the setup of the second tunnel (Hub to Spoke B).
In the module Logs > VPN in Stormshield Network Real-Time Monitor, check that phases 1 and 2 took place correctly (message “Phase established”):
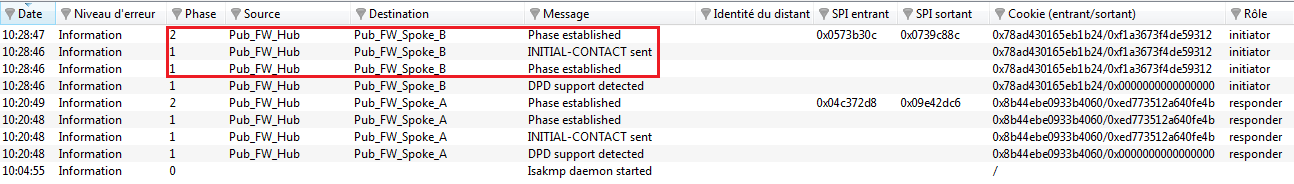
In the module VPN tunnels, you can now see both tunnels:
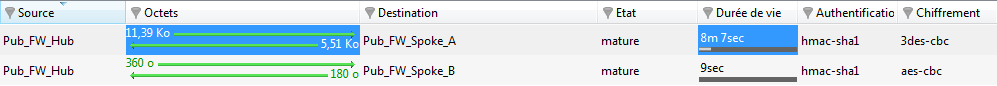
Information and diagnosis tools in console mode
showSPD command
The command showSPD displays the active IPsec policy on the Firewall. Its result will be the same whether tunnels have been set up or not.
In Case no.2 of this tutorial (all traffic via IPsec tunnel), executing this command on the Spoke A Firewall will return the following result:
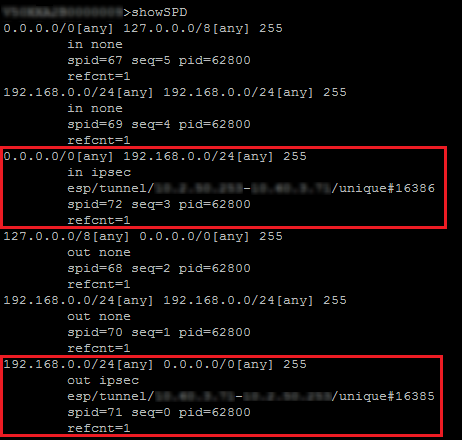
The following information will be found:
- The local network and the remote network: “192.168.0.0/24 [any] 0.0.0.0/0 [any]”,
- The direction of the tunnel: “out ipsec”,
- The IP addresses of the IPsec gateways: “esp/tunnel/local address – remote address”,
- The ID of the Security Association (SA): “unique#16385”.
showSAD command
The command showSAD lists the security information of SAs (Security Associations) set up on an IPsec gateway. Such information will be available only when tunnels have been set up.
In Case no.2 of this tutorial (all traffic via IPsec tunnel), executing this command on the Spoke A Firewall will return the following result:
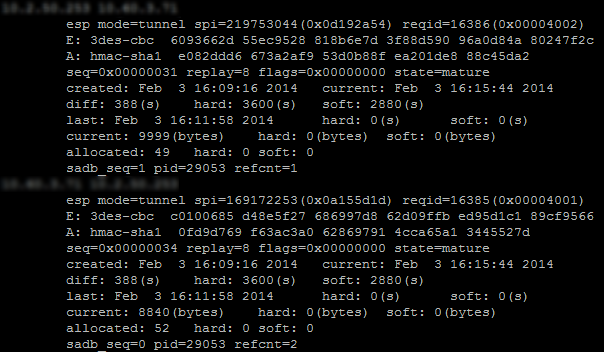
The following information will be found:
- IP address of the sending gateway – IP address of the receiving gateway.
- The SPI (Security Parameter Index): “spi=169172253 (0x0a155d1d)”. The SPI is identified according to the direction of the SA displayed. As such, for an SA described in the direction remote IP – local IP, the SPI indicated is the incoming SPI. It therefore allows identifying incoming traffic.
- The encryption method used: “E: 3des-cbd”,
- The authentication method used: ”A: hmac-sha1”,
- The state of the tunnel: “state=mature”. This state can be mature (the tunnel has been set up correctly: the SA is available and usable), larval (the SA is being negotiated) or dying (the SA’s lifetime has expired and it will be renegotiated when the traffic requires it).
- The date/time the tunnel was set up and the current date/time,
- The number of bytes exchanged. current: 8840 (bytes).
Incident resolution - Common errors
- If you have chosen to use authentication by certificate, please refer to the section “Incident resolution - Common errors” in the tutorial “IPsec VPN – Authentication by certificate”.
- If you have opted for authentication by pre-shared key, please refer to the section “Incident resolution - Common errors” in the tutorial “IPsec VPN – Authentication by pre-shared key”.