Setting up filtering rules
The VPN tunnel is meant to interlink two remote sites securely, but its purpose is not to filter traffic between these two entities. Filtering rules therefore need to be set up in order to authorize only necessary traffic between identified source and destination hosts.
In the menu Configuration > Security policy > Filtering and NAT:
- Select your filtering policy.
- In the Filtering tab, click on the menu New rule > Standard rule.
- Fill in the Action, Source, Destination and Destination port fields.
For better security, you can create a more restrictive rule on the Firewall that hosts the intranet server by specifying the source of the packets. To do so, when selecting the traffic source, indicate the value “IPsec VPN tunnel” in the field Via (Advanced properties tab):
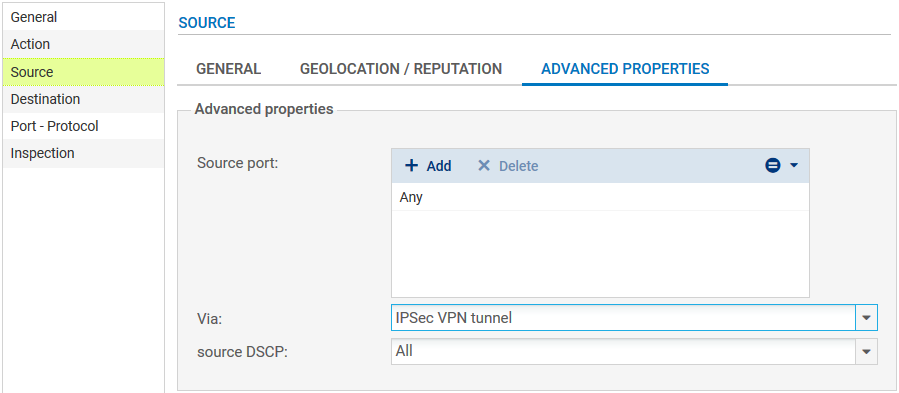
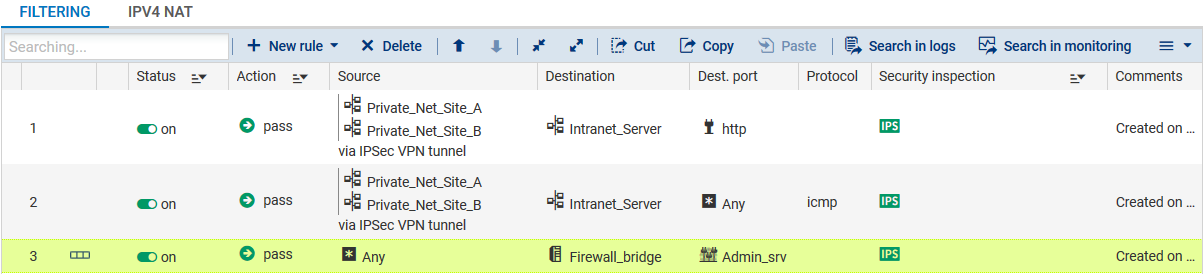
In the case presented, client workstations located on remote sites must be able to connect in HTTP to the intranet server located on the local network of the main site (rule no. 1). You can also temporarily add, for example, ICMP to test the setup of the tunnel more easily (rule no. 2).
The filtering rules on the main site will look like this:
NOTE
The advanced features on Firewalls (use of proxies, security inspection profiles, etc) can of course be implemented in these filtering rules.