Restricting the use of the SSL proxy
To optimize memory consumption, restrict the use of the SSL proxy by following the recommendations below.
In order to restrict the use of the SSL proxy, you can allow direct connections for the most frequently visited trusted internal websites.
In the Configuration > Security policy > Filter - NAT module, in the Filtering tab, add a single rule above your SSL rules with the following properties:
- Action: Pass
- Destination: FQDN object representing your trusted website (i.e., FQDN object mywebsite.com created beforehand).
- Dest. port: https
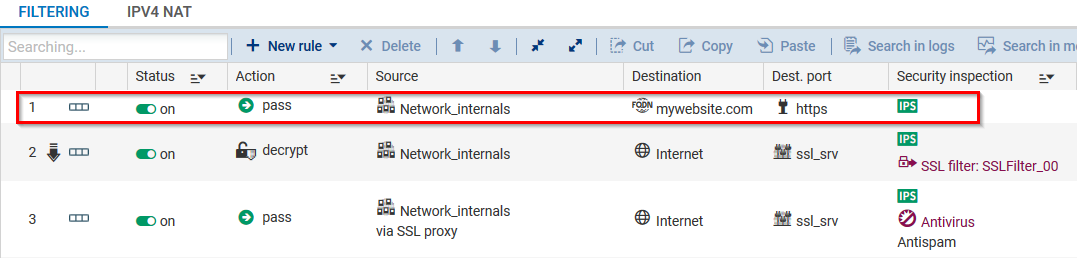
In this example, any connection to the website https://mywebsite.com will be allowed without any redirection to the SSL proxy. It will therefore consume less memory and will not be deducted from SSL connections.
Add a rule for each trusted website.
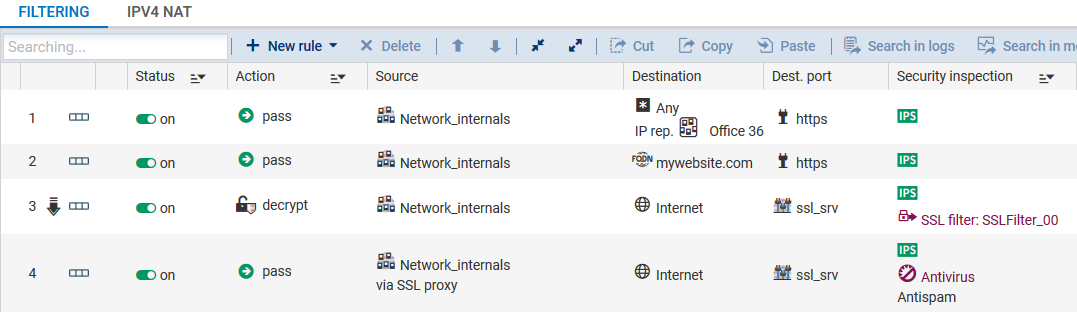
If your users have Office 365 accounts, you can allow direct connections to all Office 365 resources without redirecting them to the SSL proxy.
In the Configuration > Security policy > Filter - NAT module, in the Filtering tab, add a single rule above your SSL rules with the following properties:
- Action: Pass,
- Dest. port: https,
- Destination: In the destination's Geolocation/Reputation tab, select the Office 365 reputation category.
Whenever a user visits a web page, not only is he establishing a connection with the website in question, he is also connecting to many other advertising websites. To reduce the number of connections, you are therefore strongly advised to block advertising websites (Ads or Advertisements & Pop-Ups) in the SSL filter policy.
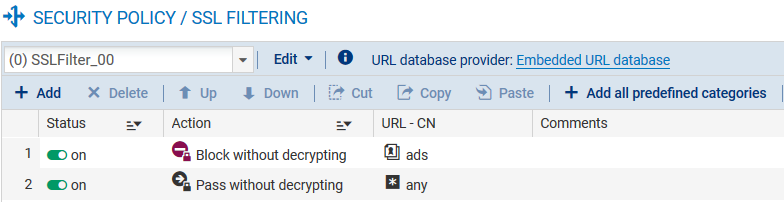
In order to block as many URLs as possible and filter them more thoroughly, use the Extended Web Control URL database instead of the embedded URL database. This will boost performance as this database is not loaded in memory.
In the Configuration > Objects >
If you do not have the Extended Web Control option on your firewall, get in touch with your Stormshield contact.