How the SSL proxy works
The SSL proxy is placed as a "man in the middle" on the SSL traffic between the client and the web server. It manages SSL negotiations and thereby secures SSL proxy/server and SSL proxy/client connections. Between both sides, it allows or blocks connections according to the filter policy, and where necessary, it decrypts SSL traffic.
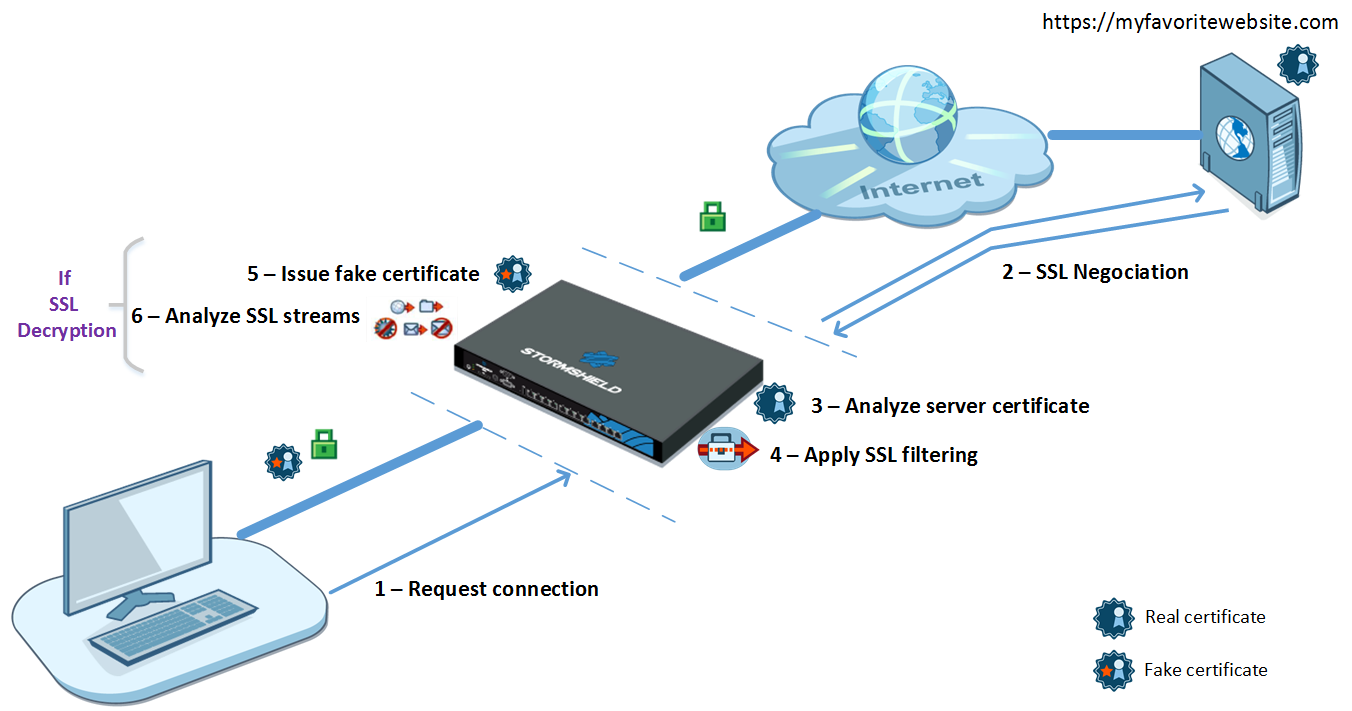
The various steps in SSL filtering are as follows:
- The SSL proxy intercepts connections from the client over TCP port 443.
- It carries out SSL negotiations with the web server on behalf of the client.
- It analyzes the certificate sent by the server. If the certificate is non-compliant, access to the server will be blocked.
- If the certificate is compliant, the SSL proxy will look up the SSL filter rules:
- Block without decrypting: it blocks connections,
- Pass without decrypting: it allows connections to pass through,
- Decrypt: it decrypts traffic, which will then be evaluated by the filter rules that follow.
- If the action is Decrypt, the SSL proxy will generate a fake certificate and present it to the client, which will verify the certificate. If the certificate from the signing authority has not been installed in the browser or on the system, and declared as a trusted authority, an error message will appear.
- If the certificate is present, traffic will be secured. Application protections will then be applied (e.g., anti-virus, antispam, sandboxing).
NOTE
Steps 5 and 6 are relevant only if you apply filtering WITH SSL traffic decryption.