Creating SSL inspection rules in the filter policy
In order for your newly created SSL filter policy to be applied in the firewall's filter policy, you need to create an SSL inspection rule.
- Log on to the web administration interface.
- In the module Configuration > Security policy > Filter - NAT, select the Filtering tab.
- In the drop-down list, select the filter policy with which SSL filtering needs to be associated.
- Click on New rule > SSL inspection rule.
- In the Profile of traffic to be decrypted area in the SSL inspection wizard, keep the default values to create a rule that will intercept all traffic originating from the internal network and going to the Internet over the port group ssl_srv. The port group ssl_srv contains standard ports of services that use TLS sessions: HTTPS, SMTPS, POPS, etc. However, the SSL proxy does not manage FTPS.
Modify the values of fields where necessary if the default configuration is not suitable. For example, if you are using the SSL proxy only for HTTPS traffic, indicate https only instead of ssl_srv to minimize consumption of firewall resources. Use the port group ssl_srv only if all the protocols that it includes need to be decrypted.
- In the Inspect encrypted traffic area, enter the following information:
- Inspection profile: Select the desired inspection profile. For more information, refer to the Administration and configuration guide.
- SSL filter policy: Select the filter policy that you have created in the section Defining SSL filter policies (SSLFilter_00).
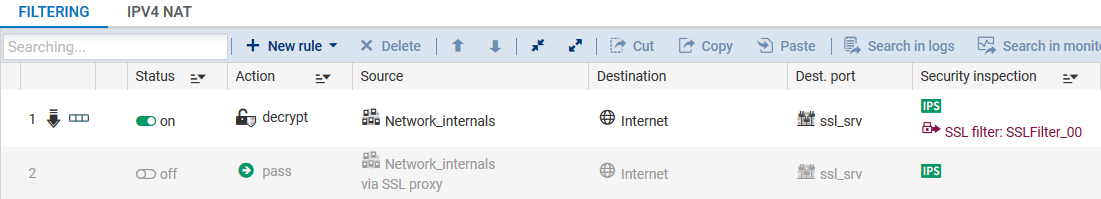
- Click on Finish. The wizard will generate two filter rules:
- The first rule makes it possible to intercept traffic originating from the internal network to the Internet over the port group ssl_srv. All this traffic will be directed to the SSL proxy. This rule will apply SSL filtering and the Decrypt action.
- The second rule allows traffic originating from the internal network and leaving through the SSL proxy to the Internet.
- If you have chosen filtering WITHOUT decrypting SSL traffic, disable the second rule as it will not be used.
-
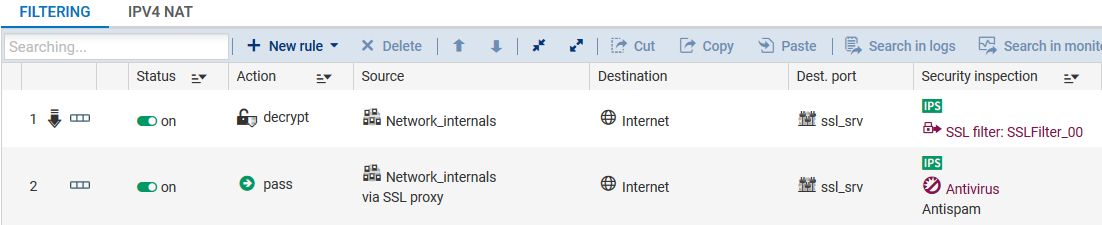
If you have chosen filtering WITH SSL traffic decryption, double-click in the Security inspection column of the second rule and enable the relevant application protection (antivirus, antispam, URL filtering, etc.).
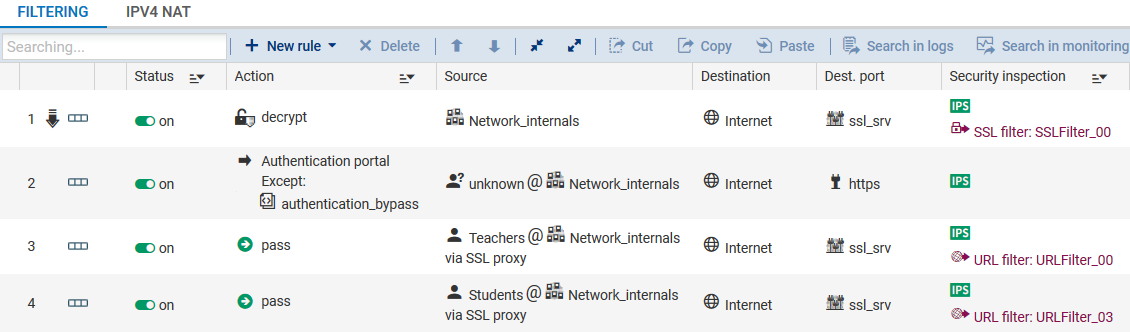
It is possible to set up different rules for different user groups. For example, in a school, you can have two groups – Students and Teachers – who will not have access to the same websites. After having created both of your SSL inspection rules:
- Double-click on the second rule to edit it.
- In the menu Source > General tab, > in the Users field, select the user group that this SSL filter concerns (for example, the Students group).
- Copy and paste both rules.
- Double-click on the first rule that you have just copied to edit it.
- In the menu Source > General tab, > in the Users field, select the user group that this SSL filter concerns (for example, the Teachers group).
- In the menu Inspection, in the SSL filtering field, select the SSL filter policy that you wish to associate with the Teachers group.
If users must authenticate whenever they attempt to log on to an HTTPS website, you need to add a rule that makes it possible to redirect them to the captive portal. This rule must be placed just after the decryption rule.
Add this rule using the button New rule > Authentication rule, then add https in the Destination port.