Creating a security group for traffic to and from the outside
This security group brings together rules for traffic allowed from external networks to the firewall and protected hosts, and from protected networks to the outside.
In this technical note, the following inbound traffic streams allowed :
- SSH: access to the firewall in console,
- SSH redirection port (e.g., TCP port 2222): access to the protected web server in console,
- HTTPS: access to the firewall’s web administration interface,
- HTTP: access to the web server protected by the firewall.
Creating the security group
In the COCKPIT 3DS OUTSCALE console, under the Network/Security menu:
- Select Security groups.
- Click on Create.
- Name the security group (e.g., Documentation-Security-Group).
- Add a description (e.g., SSH HTTPS HTTP Inbound access).
- Select the VPC (Documentation-VPC in the example).
- Click on Create.
Creating security rules corresponding to traffic allowed with the outside
- Select the security group created earlier (Documentation-Security-Group in the example).
The list of rules attached to the security group appears in the lower section of the configuration window. - In the list of rules, click on Create rule.
- Select Inbound mode.
- Set SSH as the protocol.
- Click on All IPs.
- Click on the + symbol.
- Repeat steps 3 to 6 with HTTP and HTTPS.
- Repeat steps 3 to 6 with the values Inbound, Custom, TCP, 2222 and All IPs.
- Confirm the rules by clicking on Create.
IMPORTANT
A rule allowing outbound traffic will automatically be created.
This rule must not be deleted because it allows outbound traffic that is necessary to get security updates for instances deployed in the VPC.
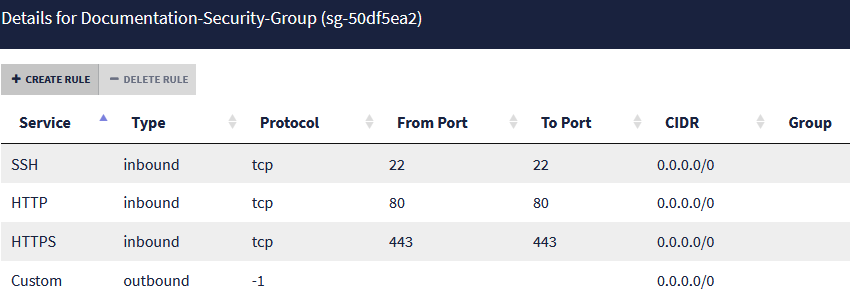
The list of rules regarding traffic allowed for the security group will then look like this: