Configuring dynamic routing
BIRD v2 can be configured in Configuration > Network > Dynamic routing > BIRD v2 (INACTIVE) tab.
In any implementation, the following lines must at least be configured in order to define a basic environment for cooperation with the system.
# WARNING : There is no implicit filtering rules implemented in SNS which allow to use various BIRD protocols
# There is more information in Technical Note > Bird Dynamic Routing
# Enable extra logs
# Possible values are :
# off No extra log
# all All extra log
# adj Log neighbors state changes
# route Log route addition/deletion
# or a combination of adj and route separated by '|'
# IE. sns_log adj|route;
sns_log off; # default is "no extra log"
# This pseudo-protocol watches all interface up/down events.
protocol device {
scan time 10; # Scan interfaces every 10 seconds
}
# The direct protocol automatically generates device routes to
# all network interfaces.
protocol direct {
ipv4; # Minimal IPv4 default channel config
}
# This pseudo-protocol performs synchronization between BIRD's routing
# tables and the kernel.
protocol kernel {
learn; # Learn all alien routes from the kernel
persist; # Don't remove routes on bird shutdown
scan time 20; # Scan kernel routing table every 20 seconds
ipv4 {
import all; # Default is import all
export none; # THIS CONFIGURATION MUST BE ADJUSTED
preference 254; # Protect existing routes
};
}
# This pseudo-protocol is used to configure static routes.
protocol static MyStaticRoutes {
ipv4;
# route 0.0.0.0/0 via 173.1.1.1; # Default route
# route 192.168.250.0/24 via "out"; # Declare network via username interface
# route 192.168.251.0/24 via 173.1.1.2; # Declare network via specific gateway
# route 192.168.252.0/24 via 173.1.1.3 bfd; # Declare network via specific gateway with BFD enabled
}
We will not cover each configuration line in detail here. If you require more exhaustive explanations, refer to the online BIRD documentation at:
http://bird.network.cz/?get_doc&f=bird.html.
The most important concepts to note are protocol instances and filters.
A protocol instance can either be BGP, RIP or OSPF, and it defines an appropriate configuration. Several instances can be defined when necessary for the same protocol.
Each protocol instance is connected to an internal BIRD routing table. This connection is monitored by two filters that can accept, reject or modify routes.
The export filter monitors routes that are sent from the internal BIRD routing table to the protocol. The import filter performs the same operation in the opposite direction.
IMPORTANT
Precision is key during the implementation of route filtering.
The use of full route imports or exports (e.g., import all;) between protocol instances may produce disastrous results.
Understanding syntax rules
- Any text on the line placed after a # is a comment,
- Any text between /* and */ is a comment,
- Blocks of several options are placed between curly brackets {},
- Every option ends with a semi-colon ;,
- The configuration is case sensitive.
Verifying a configuration
The example described below shows how to verify a configuration that contains two syntax errors.
The following configuration is entered in the configuration window:
# WARNING : There is no implicit filtering rules implemented in SNS which allow to use various BIRD protocols
# There is more information in Technical Note > Bird Dynamic Routing
sns_log off; # default is "no extra log"
router id 192.168.97.219;
protocol kernel {
persist; # Don't remove routes on bird shutdown
scan time 20; # Scan kernel routing table every 20 seconds
ipv4 {
export all; # THIS CONFIGURATION MUST BE ADJUSTED
preference 254; # Protect existing routes
};
learn; # Learn all alien routes from the kernel
protocol device {
scan time 10 # Scan interfaces every 10 seconds
}
Click on Check configuration. The verification console located at the bottom of the screen will indicate the first error that it encounters.
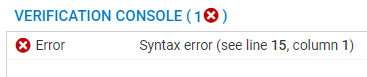
Line number 15 is also highlighted in red in the configuration.
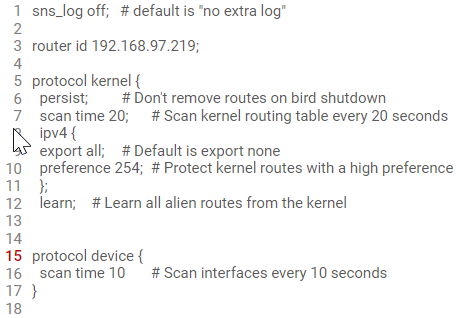
Explanation: if there is no curly bracket to close a block, the error will mention the first line of the following block, which is a line that does not match the command allowed in the unclosed block. The “}” character therefore needs to be inserted at the end of the previous line.
Once the first error has been fixed, click again on Check configuration to show the following syntax error in the verification console (with the line number corresponding to the error highlighted in red in the configuration):
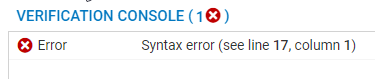
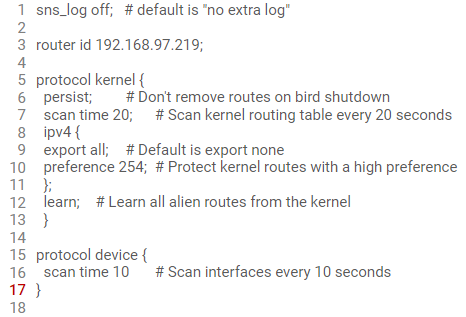
Explanation: the “;” character has to be inserted at the end of the previous line (line 16 in this example).
Interactions with Stormshield Network routing
In the default configuration provided on Stormshield Network firewalls, the firewall’s routing module takes priority over dynamic routing (maximum preference value of 254).
WARNING
When the firewall’s routes are reconfigured, they are temporarily erased, so BIRD can configure its own routes. The firewall’s routing has to be protected using an export filter on the kernel pseudo-protocol.
The following is an example of a filter that protects the default route and static route 1.2.3.0/24:
filter protect_Stormshield_routes{
if (net = 0.0.0.0/0) || (net = 1.2.3.0/24) the reject;
else accept;
}
protocol kernel {
learn; # Learn all alien routes from the kernel
persist; # Don't remove routes on bird shutdown
scan time 20; # Scan kernel routing table every 20 seconds
ipv4 {
import all; # Default is import all
export filter protect_Stormshield_routes;preference 254; # Protect existing routes
};
}
Dynamic routing with priority over Stormshield Network routing
In the BIRD dynamic routing table, if you want dynamic routing to take priority over Stormshield Network routing, the routes obtained by dynamic routing (BGP, OSPF or RIP protocol) must have a higher preference value than the routes obtained by the system (kernel pseudo-protocol). However, this will have no impact on the firewall’s routing table itself (which can be shown using the command netstat -r).
The preference value of the kernel must therefore be lowered, for example to 1:
protocol kernel {
(...)
ipv4 {
(...)
preference 1; # Protect existing routes
};
}
Routing the firewall’s interfaces
If the firewall’s interfaces have been configured with different sub-networks, and you wish to forward interface sub-networks via BIRD, use the direct pseudo-protocol.
By default, all interfaces will be taken into account. You can restrict the set of interfaces that are taken into account by using the interface attribute.
protocol direct {
interface "-vlan*","*";
}