Simple configurations
RIP
The version supported is RIPv2.
Below is the configuration “RIP_simple”.
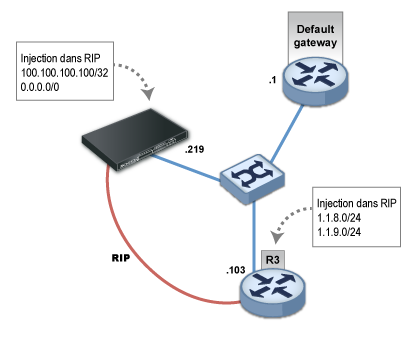
We will configure a default route and a static route to 100.100.100.100/32:
RIPv2 is configured by specifying “multicast” as the RIP mode associated with the interface “em0”. Requests by neighbors to send tables will be honored.
| router id 192.168.97.219; | ||
| protocol kernel { | ||
| persist; | # Don't remove routes on bird shutdown | |
| scan time 20; | # Scan kernel routing table every 20 seconds | |
| export all; | # Default is export none | |
| learn; | # Learn all alien routes from the kernel | |
| preference 254; | # Protect kernel routes with a high preference | |
| } | ||
| protocol device { | ||
| scan time 10; | # Scan interfaces every 10 seconds | |
| } | ||
| filter ripexport { | ||
| if (net = 0.0.0.0/0) || (net = 100.100.100.100/32) | ||
| then accept; | ||
| else reject; | ||
| } | ||
| protocol rip MyRIP { | ||
| debug all; | ||
| interface "em0" { | ||
| mode multicast; | ||
| authentication none; | ||
| }; | ||
| honor always; | ||
| authentication none; | ||
| import all; | ||
| export filter ripexport; | ||
| } | ||
The state of the protocol instance:
| bird> show protocols all MyRIP | |||||
| name | proto | table | state | since | info |
| MyRIP | RIP | master | up | 10:08:56 | |
| Preference: 120 | |||||
| Input filter: ACCEPT | |||||
| Output filter: ripexport | |||||
| Routes: 4 imported, 5 exported, 3 preferred | |||||
| Route change stats: | received | rejected | filtered | ignored | accepted |
| Import updates: | 147 | 0 | 0 | 140 | 7 |
| Import withdraws: | 0 | 0 | --- | 0 | 0 |
| Export updates: | 11 | 0 | 3 | --- | 8 |
| Export withdraws: | 0 | --- | --- | --- | 0 |
| bird> | |||||
Learned routes:
| bird> show route primary protocol MyRIP | ||||||
| 192.168.97.0/24 | via 10.200.45.250 on eth0 [MyRIP 10:29:19] ! (120/2) | |||||
| 1.1.9.0/24 | via 10.200.45.250 on eth0 [MyRIP 10:29:19] * (120/2) | |||||
| 1.1.8.0/24 | via 10.200.45.250 on eth0 [MyRIP 10:29:19] * (120/2) | |||||
Below are the routes received by the neighbor. Note that the default route has been received. Ordinarily, other routers on the market would reject the export of this route. However, in this case, it has to be filtered explicitly.
bird> show route primary protocol MyRIP
0.0.0.0/0 via 192.168.97.219 on eth0 [MyRIP 10:36] * (120/2)
100.100.100.100/32 via 192.168.97.101 on eth0 [MyRIP 10:36 from 192.168.97.219] * (120/2)
OSPF
The versions supported are OSPFv2 for IPv4 and OSPFv3 for IPv6.
Below is the configuration “OSPF_simple”:
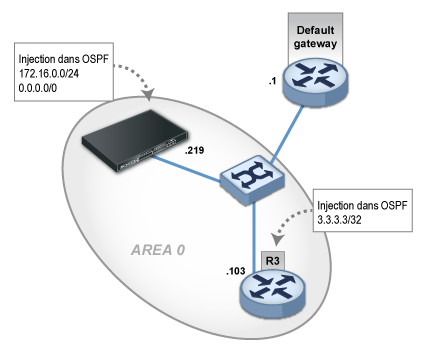
It consists of deploying an area 0 on a LAN where a possible neighbor is explicitly indicated. All routes are imported from OSPF and redistributed in OSPF. The route of the sub-network directly linked to the interface em3 (172.16.0.0/24) and the default route are redistributed in OSPF.
| router id 192.168.97.219; | ||
| protocol kernel { | ||
| persist; | # Don't remove routes on bird shutdown | |
| scan time 20; | # Scan kernel routing table every 20 seconds | |
| export all; | # Default is export none | |
| learn; | # Learn all alien routes from the kernel | |
| preference 254; | # Protect kernel routes with a high preference | |
| } | ||
| protocol device { | ||
| scan time 10; | # Scan interfaces every 10 seconds | |
| } | ||
| protocol direct { | ||
| interface "em3"; | ||
| } | ||
| filter ospfexport { | ||
| if (source = RTS_DEVICE) || (net = 0.0.0.0/0) | ||
| then accept; | ||
| else reject; | ||
| } | ||
| protocol ospf MyOSPF { | ||
| export filter ospfexport; | ||
| import all; | ||
| area 0.0.0.0 { | ||
| stub no; | ||
| interface "em4" { | ||
| type broadcast; | ||
| neighbors { | ||
| 192.168.97.103 eligible; | ||
| }; | ||
| }; | ||
| }; | ||
| } | ||
NOTE
You are also advised to set the parameter "priority 0" in the interface section of the OSPF node configuration in order to disable the firewall's role in elections for Designated Router / Backup Designated Router roles.
The following command indicates that the neighborhood has been established (indicated by the state “full”).
The neighbor has been declared a “Designated Router” (indicated by the state “dr”)
| bird> show ospf neighbors | |||||
| MyOSPF: | |||||
| Router ID | Pri | State | DTime | Interface |
Router IP |
| 192.168.97.103 | 1 | full/dr | 00:34 | em4 | 192.168.97.103 |
|
bird> |
|||||
Routes received:
bird> show route protocol MyOSPF
3.3.3.3/32 via 192.168.97.103 on em4 [MyOSPF 16:17:38] * E2 (150/10/10000) [192.168.97.103]
192.168.97.0/24 dev em4 [MyOSPF 16:15:43] * I (150/10) [192.168.97.219]
bird>
The OSPF topology can be displayed:
| bird> show ospf topology | ||||
| area 0.0.0.0 | ||||
| router 192.168.97.103 | ||||
| distance 10 | ||||
| network 192.168.97.0/24 metric 10 | ||||
| router 192.168.97.219 | ||||
| distance 0 | ||||
| network 192.168.97.0/24 metric 10 | ||||
| network 192.168.97.0/24 | ||||
| dr 192.168.97.103 | ||||
| distance 10 | ||||
| router 192.168.97.103 | ||||
| router 192.168.97.219 | ||||
|
bird> |
||||
As well as the LSA database:
|
bird> show ospf lsadb |
|||||
| Global | |||||
| Type | LS ID | Router | Age | Sequence | Checksum |
| 0005 | 3.3.3.3 | 192.168.97.103 | 501 | 8000000a | ec8a |
| 0005 | 172.16.0.255 | 192.168.97.219 | 1150 | 80000001 | 81b6 |
| 0005 | 0.0.0.0 | 192.168.97.219 | 1150 | 80000001 | 37f1 |
| Area |
0.0.0.0 |
||||
| Type | LS ID | Router | Age | Sequence | Checksum |
| 0001 | 192.168.97.103 | 192.168.97.103 | 455 | 8000000a | 2254 |
| 0002 | 192.168.97.103 | 192.168.97.103 | 456 | 80000006 | 9384 |
| 0001 | 192.168.97.219 | 192.168.97.219 | 1144 | 8000041b | 0bf8 |
|
bird> |
|||||
NOTE
Note that the type of LSA is shown on the left whereas it is generally used as a horizontal delimiter by the usual display standards.
BGP
“BGP_simple” configuration
The version supported is BGPv4 for IPv4 and IPv6.
Below is the configuration “BGP _simple”.
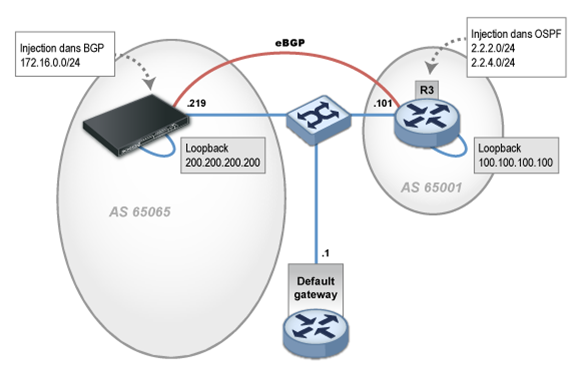
The configuration “BGP_simple” is implemented as follows:
|
router id 192.168.97.219; |
||
| protocol kernel { | ||
| persist; | # Don't remove routes on bird shutdown | |
| scan time 20; | # Scan kernel routing table every 20 seconds | |
| export all; | # Default is export none | |
| learn; | # Learn all alien routes from the kernel | |
| preference 254; | # Protect kernel routes with a high preference | |
| } | ||
| protocol device { | ||
| scan time 10; | # Scan interfaces every 10 seconds | |
| } | ||
| protocol direct { | ||
| interface "em3"; | ||
| } | ||
| protocol | bgp router1 { | |
| description "My 1st BGP uplink"; | ||
| local as 65065; | ||
| neighbor 100.100.100.100 as 65001; | ||
| multihop 5; | ||
| hold time 180; | ||
| keepalive time 60; | ||
| export where source = RTS_DEVICE; | ||
| import all; | ||
| default bgp_local_pref 100; | ||
| source address 200.200.200.200; | ||
| } | ||
Explanations
Unlike most routers on the market, the local AS has to be specified for each BGP instance.
According to the best practices, this eBGP session is set up between loopback interfaces and not physical interfaces. It is therefore necessary to configure the IP of the local loopback in question (200.200.200.200/32), to specify this address as the source and a static route to the neighbor’s loopback.
Loopback virtual interfaces
In version 2, the web administration interface allows configuring loopback interfaces via the Virtual interfaces module, in the Loopback tab:
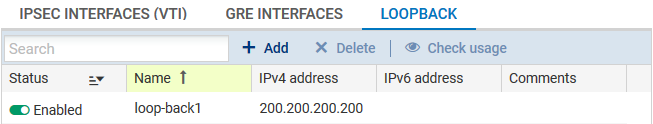
It is advisable to declare the static route to the remote loopback on the firewall outside the Bird configuration via the Routing module in the Static routes tab, in order to prevent BGP traffic from being blocked by “IP address spoofing” alarms:
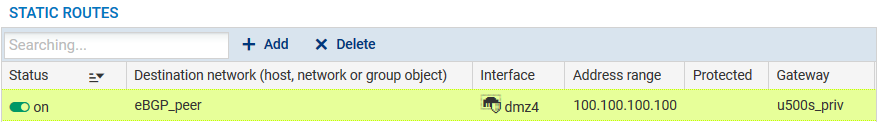
Once again, we will select only the sub-network 172.16.0.0/24 directly linked to the interface em3 as the route to announce to our neighbors.
Here, an anonymous export filter has been defined directly in the “export” instruction, with the keyword "where". This export filter selects routes with RTS_DEVICE as their source, meaning routes obtained by the “direct” pseudo-protocol.
The value of the hold-time has been specified as 180s, the usual market value. BIRD implements by default 240s. The value of the keepalive duration does not need to be specified (calculated at 1/3 of the hold-time) but we are mentioning it explicitly for clarity. Likewise for the default local-preference.
The command “show protocols” below confirms that the session is indeed working.
|
bird> show protocols router1 |
|||||
| name | proto | table | state | since | info |
| router1 | BGP | master | up | 12:47 | Established |
|
bird> |
|||||
The neighbor has received the routes:
| bird> show route protocol router1 | ||||
| 100.100.100.100/32 | via | 192.168.97.101 | on em0 | [router1 13:09 from 100.100.100.100] |
| (100/?) [AS65001?] | ||||
| 2.2.2.0/24 | via | 192.168.97.101 | on em0 | [router1 13:09 from 100.100.100.100] |
| *(100/?)[AS65001?] | ||||
| 2.2.4.0/24 | via | 192.168.97.101 | on em0 | [router1 13:09 from 100.100.100.100] |
| *(100/?)[AS65001?] | ||||
| bird> | ||||
On the BGP neighbor, the route announced and released by the filter is received. As for the route 1.1.1.1/32, it has been blocked.
| @router1:~$ show ip bgp | ||||
| BGP table version is 0, local router ID is 2.2.2.2 | ||||
| Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, | ||||
| r RIB-failure, | S Stale, | R Removed | ||
| Origin codes: i - IGP, e - EGP, ? - incomplete | ||||
| Network | Next Hop | Metric LocPrf | Weight | Path |
| *> 2.2.2.0/24 | 0.0.0.0 | 1 | 32768 | ? |
| *> 2.2.4.0/24 | 0.0.0.0 | 1 | 32768 | ? |
| *> 100.100.100.100/32 | 0.0.0.0 | 1 | 32768 | ? |
| *> 172.16.0.0/24 | 200.200.200.200 | 0 | 65065 i | |
| *> 192.168.97.0 | 0.0.0.0 | 1 | 32768 | ? |
| Total number of prefixes 5 | ||||
| @router1:~$ | ||||
Authentication
TCP-MD5 authentication can be set up between BGP routers in BIRD.
This method allows protecting BGP sessions by authenticating frames in the TCP header in compliance with RFC2385.
This is represented by the addition of a "password" directive in the configuration of the BGP router in the files /usr/Firewall/ConfigFiles/Bird/bird.conf (dynamic routing of IPv4 packets) and /usr/Firewall/ConfigFiles/Bird/bird6.conf (dynamic routing of IPv6 packets). For example:
|
protocol bgp |
|
| { | |
| local as 65065; | |
| neighbor 100.100.100.100 as 65001; | |
| export where source = RTS_DEVICE; | |
| import all; | |
| source address 200.200.200.200 ; | |
| password "very_secret"; | |
|
} |
NOTE
Passwords must not contain spaces or the equal sign (‘=’).