Creating IoC analysis units
In IoC analysis units, you can import the various types of indicators of compromise in the form of lists. You can then use these analysis units in security policy rules, manual on-demand tasks or scheduled tasks.
Refer to the following sections on how to use analysis units:
-
You must hold the Resources-Modify privilege to create analysis units.
-
The indicators of compromise that you will use in analysis units must be compiled in CSV files. You can find examples of indicators on websites, such as the ANSSI's website. Indicators may also originate from your own device pool if you have detected a compromise with SES Evolution or via other means, or from Stormshield resources downloaded from the update server. For more information, refer to the section Downloading Stormshield updates.
The CSV file may be in the following format: indicator in the first column, followed by a separator (comma, semi-colon or tab) and a description in the second column. The description is not mandatory, in which case, the separator will not be necessary. If the CSV file contains more than two columns, it can still be imported into the unit but only the first two columns will be taken into account and shown in the console. Column titles are not required.
For hash indicators, the hash algorithm does not need to be indicated in the CSV file. The console will automatically detect it.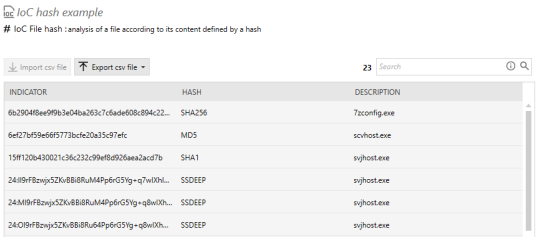
-
Select the Security > Resources menu.
-
In the left panel, click on + Add a resource.
-
Select IoC scan, then the type of indicators to search for in the scan:
-
Text: search for suspicious character strings (file name, domain name, host name, IP address, subject name, email address),
-
File name: searches for suspicious files,
-
File hash: searches for suspicious file hashes, If you import SSDEEP file hashes, you can change the default similarity rate of 80% by clicking on Global settings in the top right corner of the Resources panel. A 100% match between two files means that they are identical.
-
DNS request: searches for requests submitted to suspicious domain names,
-
Named object: the search will cover suspicious object names among Windows named objects (ALPC port, Event, Job, Mutant, Section, Semaphore, Timer, Mailslot, NamedPipe, etc.).
The new unit will be added to the IOC category in the panel on the left. You will find the resources provided by Stormshield under the category Stormshield IOC.
-
-
In the New analysis unit field, enter the name of your analysis, then a description below it if necessary.
- Click on Import .csv file and select a CSV file that lists the indicators matching the chosen type. The total number of indicators appears to the left of the Search field. You can import only one CSV file per unit.
- Click on Save.
IoC analysis units cannot be deleted while they are being used in an IoC task, scheduled scan or as an action when logs are generated in an SES Evolution rule.
To obtain a local copy of the CSV file, if it was imported by another administrator, for example, click on  and select a destination folder. You can then look up this file, edit it and import it into the same analysis unit or into another unit.
and select a destination folder. You can then look up this file, edit it and import it into the same analysis unit or into another unit.
You can also import a .cab file directly from the ![]() menu in the panel on the left. Cab files contain the file(s) to be used in a Yara or IoC analysis unit as well as other data such as the title and description of the unit. In the same menu, the Export sub-menu makes it possible to export an analysis unit with all this information in a .cab file.
menu in the panel on the left. Cab files contain the file(s) to be used in a Yara or IoC analysis unit as well as other data such as the title and description of the unit. In the same menu, the Export sub-menu makes it possible to export an analysis unit with all this information in a .cab file.